Brute force attack: Common types and its Prevention

Bisma Farrukh
In the ever-evolving landscape of cybersecurity, you face a constant battle against malicious actors seeking to breach your defenses. One of the most persistent threats you must guard against is the brute force attack. This relentless assault on your systems attempts to crack passwords and gain unauthorized access through sheer computational power and persistence.
As a cybersecurity professional, understanding the mechanics of brute force attacks and implementing robust countermeasures is crucial to safeguarding your organization’s digital assets. This article will explore practical strategies to fortify your defenses and stay one step ahead of these formidable cyber threats.
Table of Contents
What is a Brute Force Attack?
A brute force attack in cyber security is a relentless method hackers use to gain unauthorized access to systems or accounts. This technique involves systematically attempting every possible combination of passwords or encryption keys until the correct one is found. Brute force attacks can be time-consuming, but with modern computing power, they remain a significant threat.
Several brute force attacks include simple, dictionary, and hybrid attacks. Cybercriminals often employ sophisticated Brute Force Attack Tools to automate and accelerate their efforts. These tools can generate and test thousands of password combinations per second, making them a formidable weapon in a hacker’s arsenal.
Understanding brute force attacks and how they work is crucial for developing effective defense strategies in today’s digital landscape.
Common Types of Brute Force Attacks
Understanding the various types of brute force attacks in cyber security is crucial for effective defense.
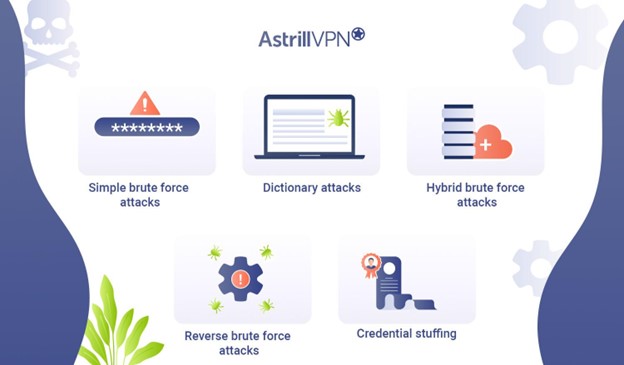
Simple brute force attacks:
A brute force attack involves systematically generating all possible combinations of characters until the correct password is found. This involves systematically trying every possible password option until you find the one that works.
Hackers try to guess your credentials without using software tools. They can reveal very simple passwords and PINs.
Once you have all the possible combinations generated, you then systematically try each one on the password protected system or account. This is done by a brute force attack tool or program that will automatically input each password combination and check if it works.
If a correct password is found, the attack stops. If all combinations are tried without finding the correct password, the attack failed. However, the attack may still be running in the background trying additional password combinations.
Dictionary attacks:
A hacker selects a target and tests possible passwords against that username. This is known as a dictionary attack and is a basic tool in brute force attacks. Hackers may use complete dictionaries and add special characters and numbers to words, but this type of sequential attack is difficult.
Dictionary attacks are when hackers or cybercriminals try to guess your passwords by systematically checking all words in an electronic dictionary.
Avoid common, simple passwords that use dictionary words, names, and numbers. Instead, create long passwords using a combination of upper- and lower-case letters, numbers, and symbols. Aim for at least 12 characters if possible.
Avoid reusing the same password across multiple accounts. Create a unique, complex password for each important account. If you have trouble remembering all of them, consider using a password manager application.
Ensble two-factor authentication whenever possible. This requires not just a password, but a second step like a code sent to your phone. Two-factor authentication makes it much harder for hackers to access your accounts, even if they guess your password.
Hybrid brute force attacks:
These hackers combine other methods with logical guesses to attempt to break in. A hybrid attack typically mixes dictionary and brute force attacks to crack passwords that combine common words with random characters.
A hybrid brute force attack combines two or more brute force techniques to compromise an account or system. This type of attack can be more effective than a basic brute force attack alone.
A hybrid brute force attack may start with a dictionary attack using common passwords. If that fails to crack the password, the attack may then switch to a brute force attack that systematically tests all possible combinations of letters, numbers, and symbols.
Another common hybrid attack is a mask attack. With this approach, the attacker starts with a dictionary list but then applies masks to the words. For example, adding numbers to the beginning or end, capitalizing letters, and inserting symbols. This expands the number of possible password guesses without resorting to a full brute force attack.
Reverse brute force attacks:
In this type of attack, hackers start with a known password and search through millions of usernames until they find a match. They often start with leaked passwords available online from existing data breaches.
A reverse brute force attack is a technique used by hackers to gain unauthorized access to systems and data.
In a reverse brute force attack, the hacker already has access to some information like a username. They then attempt to figure out the password by trying many different possibilities. Here are the basic steps involved:
1) The hacker obtains or guesses a valid username for the system they want to access. This could come from a data breach, social engineering, or an educated guess.
2) The hacker then starts testing password combinations to see which one matches and grants access. They will start with simple, common passwords and work their way up to more complex options.
3) The hacker utilizes password cracking tools or scripts to rapidly test thousands or even millions of possible password combinations in an automated way. This “brute force” approach continues until the correct password is discovered.
4) Once the correct password is found, the hacker now has unauthorized access to the system and any sensitive data it contains. They can then exploit this access for their own purposes.
Credential stuffing:
If a hacker finds a username-password combination that works for one website, they will try it on many others. Since users often reuse login information across multiple websites, they are the main targets of this type of attack.
Credential stuffing is a type of cyber attack where hackers use email and password combinations leaked from one service to gain access to people’s accounts on other services.
When people reuse the same password across multiple websites and apps, it becomes a major security risk. Once hackers get their hands on a large set of email/password combinations from one breach, they can try those credentials on many other platforms. If people reused that same password, the hackers will gain access.
This type of attack has become increasingly common. Hackers can use automated software programs to rapidly cycle through thousands of email/password combinations, trying them on different services at a fast pace.
Rainbow table Attack
A rainbow table attack is a method used by hackers to crack password-protected systems. Rainbow tables are large databases of precomputed hash values and their corresponding plaintext passwords. Hackers generate these tables in advance using sophisticated algorithms.
Once a hacker gains access to the hash values of passwords stored by a system, they can simply compare those hashes to the values in their rainbow table. If there’s a match, they instantly know the corresponding plaintext password.
The key thing is that most passwords have limited combinations, so hackers can precompute hash values for all common passwords and store them in these tables. Then, all they need to do is run a lookup.
Password spraying
Password spraying is a type of password attack that attempts common passwords across many accounts. While brute force attacks try all possible combinations on one account, password spraying targets many accounts with a smaller set of commonly-used passwords.
Password spraying attacks work by gathering a large set of usernames, often from data breaches or by crawling public information. The attacker then attempts to log in to each account using a list of common passwords. This list may consist of the top 100 or 1,000 most frequently used passwords, along with variations that replace letters with numbers and symbols.
Since most people reuse the same passwords across accounts, password spraying can be an effective attack. It allows an attacker to compromise multiple accounts quickly using a relatively short list of passwords. This makes the attacks harder to detect through things like login attempt limits on individual accounts.
To defend against password spraying, the most effective strategy is enforcing the use of long, unique passwords that are different for each account.
Brute-force attack Tools like Hydra and John the Ripper automate these processes, making it easier for attackers to breach systems. Understanding what a brute-force attack entails and its variations is essential for implementing robust cybersecurity measures.
Tools Used in Brute Force Attacks
- Automated tools assist in brute force attacks by rapidly guessing every possible password. These tools are capable of finding a single dictionary word password within one second. They are programmed with workarounds to:
- Work against various computer protocols such as FTP, MySQL, SMPT, and Telnet
- Allow hackers to crack wireless modems
- Identify weak passwords
- Decrypt passwords in encrypted storage
- Run all possible combinations of characters
- Conduct dictionary attacks
- Additionally, some tools scan pre-computed rainbow tables for the inputs and outputs of known hash functions. These tables remove the hardest part of brute-force attack, making the process faster.
- To speed up the process further, hackers have developed hardware solutions. By combining the CPU and GPU, computing power is accelerated. Using GPU processing, hackers can crack passwords about 250 times faster than using a CPU alone.
What do hackers gain from Brute Force Attacks?
Understanding what motivates cybercriminals to employ brute force attacks in cyber security is crucial for effective defense.
These attackers primarily seek unauthorized access to sensitive systems and data. Hackers aim to crack user credentials and infiltrate networks by systematically attempting countless password combinations.
Successful brute-force attacks have significant potential gains. Hackers may obtain valuable personal information, financial data, or intellectual property. They could also gain control over systems to launch further attacks, install malware, or hold data for ransom. Additionally, compromised accounts might be sold on the dark web or used for identity theft.
Various types of brute force attacks exist, each tailored to specific targets. Sophisticated Brute Force Attack Tools can block brute force attacks, automate the process, making these attacks more efficient and dangerous for unprepared organizations.
How to Prevent Brute Force Attacks?
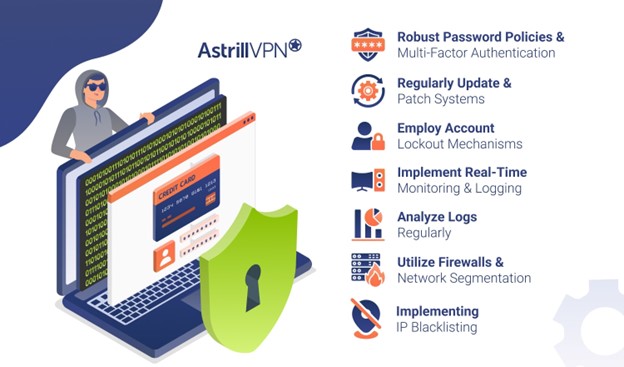
Brute force attack prevention is possible by following these strategies:
- Implement robust password policies and multi-factor authentication to protect against brute force attacks in cyber security.
- Regularly update and patch systems to address vulnerabilities that attackers might exploit.
- Employ account lockout mechanisms after a set number of failed login attempts to thwart automated brute force attack tools.
- Implement real-time monitoring and logging to detect suspicious activity. Use intrusion detection systems (IDS) and security information and event management (SIEM) tools to identify potential brute force attacks early.
- Analyze logs regularly for patterns indicative of a brute force attack, such as multiple failed login attempts from the same IP address.
- Utilize firewalls and network segmentation to limit exposure to different brute-force attacks.
- Consider implementing IP blacklisting for known malicious actors and employing CAPTCHAs to prevent automated attempts.
By combining these strategies, you can significantly enhance your defense against various types of brute-force attacks.
What are the common passwords for brute force attacks?
When attempting a brute force attack in cyber security, hackers often rely on common passwords that users frequently choose. These predictable choices make it easier for attackers to gain unauthorized access. Some of the most common passwords targeted in brute force attacks include:
- “123456” and variations
- “password”
- “qwerty”
- Common names and birthdays
- Popular phrases or song lyrics
Cybercriminals utilize specialized Brute Force Attack Tools to try thousands of password combinations systematically. Understanding the types of brute force attacks and common targets can help organizations better defend against these persistent threats. By educating users about strong password practices and implementing additional security measures, companies can significantly reduce their vulnerability to a brute force attack.
Reducing remote access risks with AstrillVPN
In the ongoing battle against brute force attacks in cybersecurity, Virtual Private Networks (VPNs) like AstrillVPN offer a robust defense mechanism. By encrypting your internet connection and masking your IP address, VPNs significantly reduce the risk of falling victim to various brute-force attacks.
AstrillVPN’s advanced security features such as Smart mode, Website and app filter provide additional protection against malicious actors attempting to gain unauthorized access to your systems. This is particularly crucial when dealing with remote access scenarios, where traditional security measures may fall short.
By implementing AstrillVPN, you shield yourself from potential brute force attack tools and create a secure tunnel for all your online activities. This proactive approach to cybersecurity helps mitigate the risks associated with brute force attacks in cybersecurity, ensuring your sensitive data remains protected.
Are brute force attacks carried out by hackers or bots?
Brute-force attacks in cyber security are typically executed by both hackers and automated bots. While skilled hackers may manually attempt to crack passwords, the sheer volume of combinations required often necessitates the use of sophisticated software. These automated tools, known as Brute-Force Attack Tools can rapidly test thousands of password combinations per second.
Cybercriminals frequently employ bots to carry out various brute force attacks, including dictionary and hybrid attacks. These bots tirelessly work through extensive lists of common passwords, phrases, and character combinations. However, it’s important to note that behind every bot is a human attacker orchestrating the assault. Understanding what is a brute force attack and how it’s executed is crucial for developing robust defense strategies.
Conclusion
Defending against brute force attacks remains a critical priority for organizations of all sizes. By implementing robust password policies, multi-factor authentication, account lockouts, and monitoring systems, you can significantly reduce your vulnerability to these relentless threats. Stay vigilant and proactive in your cybersecurity approach, regularly assessing and updating your defenses. Remember that attackers are constantly evolving their tactics, so your security measures must also evolve. You can effectively safeguard your systems and data from brute force attempts with the right combination of technology, processes, and user education.
FAQs
It’s a method where attackers systematically attempt all possible password combinations. Another name for a brute force attack is “exhaustive search.” While not fast, these attacks can be effective given enough time and computing power.
Yes, through monitoring login attempts and implementing security measures. There are various types of brute force attacks, including dictionary attacks. The main difference between a brute force attack and a dictionary attack is that the latter uses a predefined list of common passwords.
Brute-force attacks can be both online and offline. Online attacks target active systems, while offline attacks involve stolen password hashes. Cybercriminals often use specialized Brute-Force Attack Tools to automate and accelerate their efforts.

No comments were posted yet