What Is a Rainbow Table Attack and How Does It Work?

Urfa Sarmad

Hackers and cyber-criminals use password-cracking techniques to compromise users’ accounts and access sensitive data. Rainbow Table Attacks are one of the methods that they use. Unsure of what a Rainbow Table Attack is and how it can cause harm to organizations and individuals alike? Keep reading as we talk about Rainbow Table Attacks and what actionable steps you can take to help prevent them.
Table of Contents
What Is A Rainbow Table Attack?
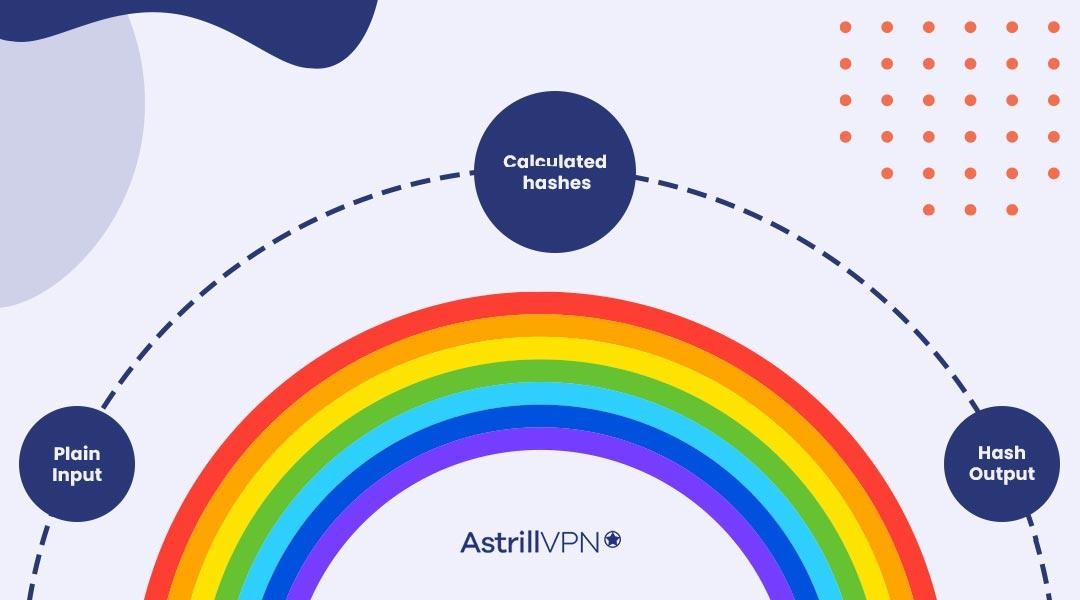
A Rainbow Table attack is a cryptographic attack to crack password hashes using a database. Rainbow tables are precomputed tables primarily used for password cracking. They contain precomputed hash values and their plaintext inputs.
The attackers exploit weak hashing algorithms to determine the original plaintext password from its hash value. Applications don’t save passwords in plaintext but encrypt passwords using hashes, so to verify that a password is correct during login, the system takes the entered password and compares the resulting hash value to the hash value stored in the database. If they match, then it means that the password is valid.
Rainbow Table Attack relies on the fact that hash functions are easily determined, meaning that the same input produces the same output. Rainbow tables get generated by applying a hash function to many possible passwords and then storing the pairs in a table. The hash function takes an input (passwords) and produces fixed-sized elements stored in a database.
When a rainbow table attack occurs, the attacker looks at the stolen hash values from the Rainbow table and finds a matching plaintext password. Using Rainbow Tables enables attackers to quickly find passwords without doing much technical work.
What Is Hashing?
Hashing transforms data (such as files and passwords) into fixed-sized characters, typically a hash value. Hashing is used primarily to verify data and for data integrity purposes. Hashing is deterministic, meaning the same input produces the same hash value.
Hash values are always of a fixed length, regardless of the input data size. A good hash function also ensures that producing the same hash value for different input data is improbable.
How Does A Rainbow Table Attack Work?
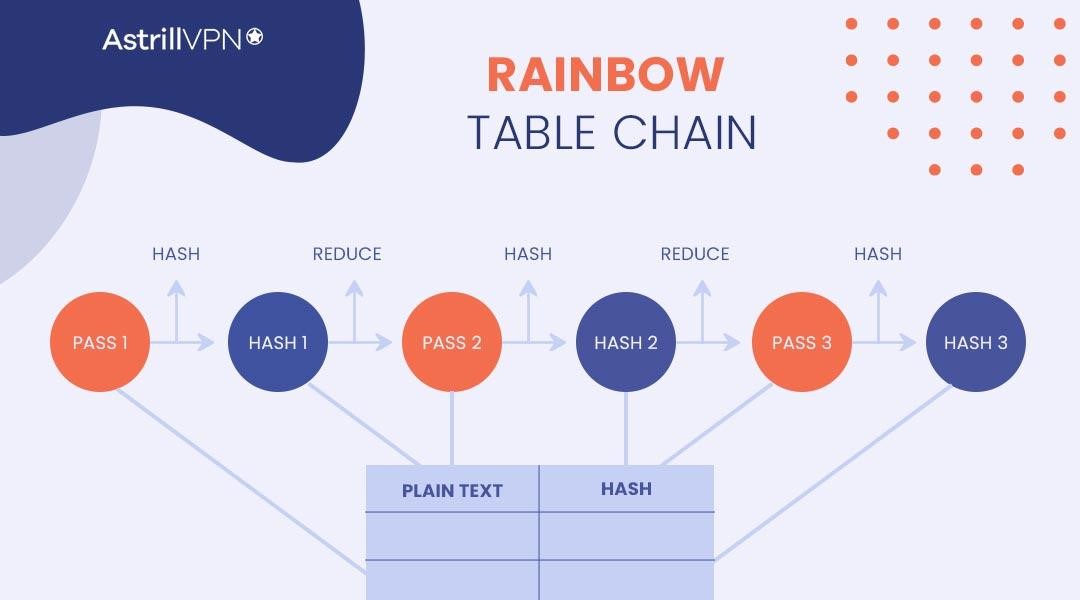
A Rainbow Table Attack is primarily used to crack password hashes. It leverages precomputed tables to determine plaintext passwords and their specific hash values. Here is a step-by-step process of how Rainbow Table Attacks work:
- The attacker starts collecting a set of password hashes from the system they’re targeting. These hashes are collected by hacking into the system or gaining unauthorized access to the system’s database.
- The attacker then generates a Rainbow table (a large lookup table) that matches hash values to corresponding plaintext passwords.
- The attacker generates the table in advance by repeatedly going through a set of passwords, hashing them, and then storing the password-hash pairs on the Rainbow table.
- When the Rainbow table gets prepared, the attacker looks for each stolen hash value in the table. If they find a match, the attacker retrieves it alongside the corresponding plaintext password.
- If they cannot find a direct match through the table, the attacker implements a reduction function to the hash value and repeats the process. The reduction takes the hash value as input and creates a new password to produce a new hash value when it hashed again. The new hash values then get checked against the table. The process is repeated until a match is found or the attacker has exhausted all his options.
- When a matching password plaintext is discovered from the Rainbow table, the attacker has succeeded in finding the hashed password. They use this information to gain authorized access to databases and systems or hack into other users’ accounts.
Rainbow Table Attacks only work against weak passwords and commonly used passwords. Strong passwords with a good length are complex and unpredictable and are less prone to Rainbow Table Attacks. That is why it is recommended to create strong passwords when signing up for a platform.
Examples of Rainbow Table Attacks
- A popular online store or service has a security breach, and the attackers get their hands on a database of user passwords. If the passwords get stored as unsalted hashes, the attacker can reverse the hashed passwords to access the user’s accounts.
- Sometimes users forget the passwords of their accounts and use Password Recovery Tools to get their accounts back. Some Password Recovery Tools use Rainbow Table Attacks to help users uncover their passwords. These tools use precomputed tables to match hash values with corresponding passwords.
- Companies and organizations sometimes use Rainbow Table Attacks for security audits. Companies perform Rainbow Table Attacks against their password databases to rule out weak or easily crackable passwords. They can use Rainbow Table Attacks to identify how secure their systems are and take measures to strengthen their security and passwords.
- Suppose an attacker steals the password database of a company. If the company has weak passwords, then the attacker can use Rainbow Tables to crack passwords easily, even if it’s offline. They wouldn’t need to access the system live.
Famous Rainbow Table Attack Cases
LinkedIn Breach (2012)
In 2012, LinkedIn’s professional networking platform suffered a significant setback when hackers accessed the company’s database containing hashed passwords of over 6.5 million users. Through this security breach, the hackers were able to use rainbow table attacks to crack a vast number of hashed passwords and get access to users’ accounts. However, it was recently discovered that not 6.5 million, but a staggering 117 million emails and passwords were stolen.
Gawker Media Breach (2010)
Gawker Media was running several popular websites and was a media company that faced a security breach in 2010. The attackers got hold of a database with hashed passwords and user account information. The attackers performed rainbow table attacks to get the passwords and gain unauthorized access to users’ accounts.
Characteristics of Rainbow Table Attacks & Dictionary Attacks
Both Rainbow Table Attacks and Dictionary Attacks are methods used in password cracking. However, the way that they approach it is different. Let’s look at the key characteristics of Rainbow Table Attacks and Dictionary Attacks and what makes them different from one another.
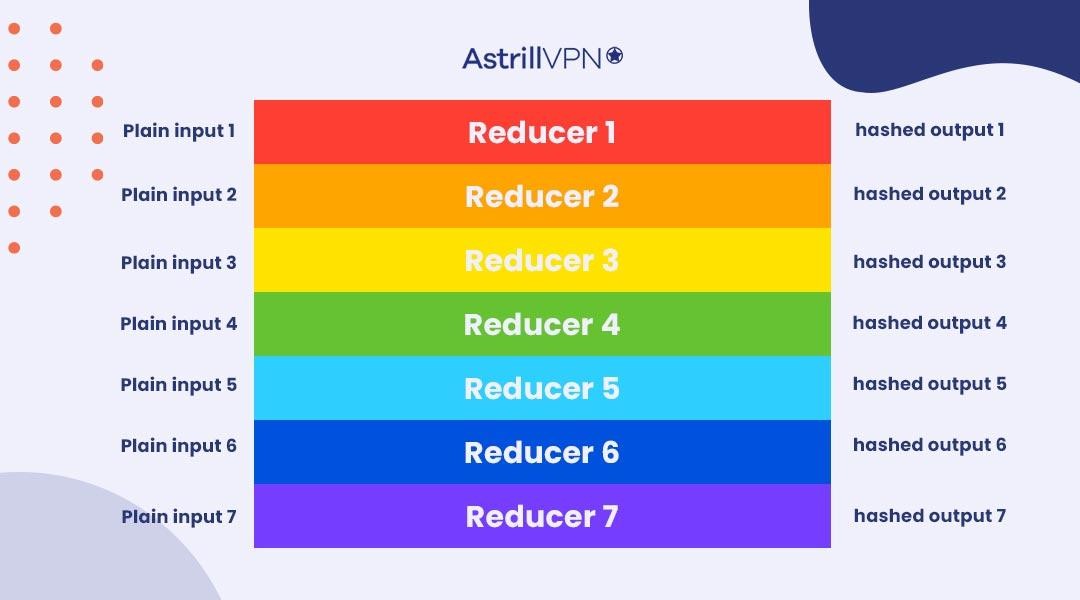
Rainbow Table Attacks Characteristics
Precomputation
Rainbow Table Attacks use pre computing and storing many hash chains that match hashed values to their corresponding plaintext passwords. These tables are generated in advance and involve a lot of resources and storage space.
Time-Efficient
Once the table gets generated, then things move quickly. The attacker quickly looks up the hashed passwords from the rainbow table and then uses them to find corresponding plaintext passwords.
Limited Passwords
Rainbow tables have limited password space since they’re based on specific hash algorithms and password lengths. If the attacker can’t find the password from the table, then their attempts will fail.
Vulnerability to Salting
Rainbow Table Attacks will be unsuccessful against salted passwords. Salting adds a unique value to each password before hashing, making precomputed tables practically useless.
Dictionary Attack Characteristics
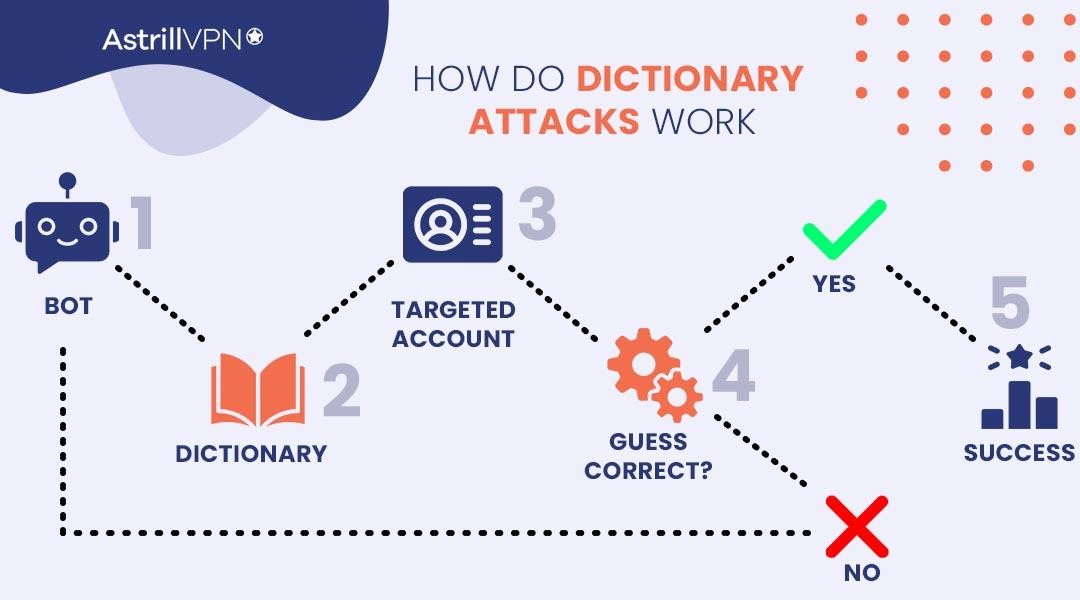
Brute Force Approach
Dictionary attacks use many words and phrases from an already generated list (dictionary) as passwords. The dictionary can contain phrases, passwords, and common words from previous breaches.
Time-Consuming
Dictionary Attacks are time-consuming, especially if the password is long and complex. The attack has to go through the entire dictionary and hash every entry to compare it to the target hash.
Salts & Other Security Measures
Like Rainbow Attacks, Dictionary Attacks are successful against weak passwords and don’t work against strong and salted passwords.
How Can Rainbow Table Attacks Be Prevented?
There are several security measures that you can implement to safeguard against Rainbow Table Attacks. Let’s go over them in detail.
Strong Passwords
To thwart Rainbow Table Attacks, you must use strong passwords. It would help to use lengthy and complex passwords that cannot be exploited by brute force or dictionary attacks. It would help if you didn’t use passwords that any hacker can easily guess or are commonly used. Go for a strong password with Uppercase and lowercase letters, characters, and numbers.
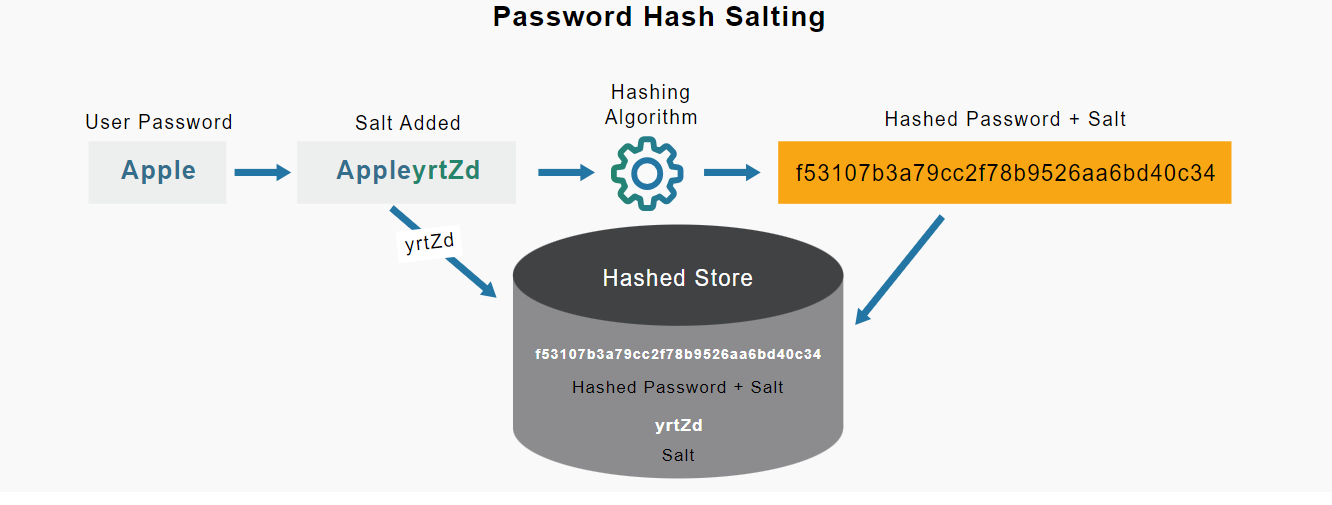
Salting
Another way to protect against rainbow table attacks is to use salted passwords. Salting is a process that involves adding a unique value (known as salt) to each password before hashing it. Salting increases the uniqueness of each hashed password, making precomputed rainbow tables useless.
Unique Salts
Use Unique salts for users’ passwords. Even if two users have the same passwords, their hashed passwords will differ because they use distinct salts. The salts should be long and completely random to enhance their effectiveness.
Change Passwords Regularly
Organizations can implement a policy whereby users have to change their passwords regularly. It helps prevent the risk of being a victim of Rainbow Table Attacks. Users should also consider not reusing old passwords or making minor changes to the old passwords.
Passwordless Authentication
Another secure way of protecting against rainbow table attacks is to use passwordless authentication. Passwordless authentication is more secure than passwords and includes biometric verification (fingerprints, thumbprints, retina scans), or you get sent an OTP (One-time-password) on your phone number or email, which only you can see.
Two-factor Authentication
Two-factor authentication is also an effective measure to counter rainbow table attacks. It adds an extra protection layer without relying on the user’s username, email, or password. It verifies your identity based on a passcode only you know or biometric data.
Wrapping Up
Rainbow Table Attacks can put the users’ accounts at risk. If the attackers get the passwords of users’ accounts, the user’s personal and confidential data could be compromised. Creating strong passwords and implementing salting can protect you against Rainbow Table Attacks, making them ineffective.
Frequently Asked Questions (FAQs)
Unlike dictionary and brute force attacks, where the attacker has to try every word in the dictionary to find a password that matches, the attacker can discover corresponding plaintext passwords from a precomputed table generated in advance.
Even though Rainbow Table Attacks can easily crack passwords if they’re all hashed the same way, they’re ineffective against salted passwords. A salt is a unique number you add to a password before hashing, making it secure and prone to Rainbow Table Attacks.
Hackers get their hands on leaked hashes before carrying out Rainbow Table Attacks. Another way they can do this is by carrying out phishing scams on those who have access to the passwords database.

No comments were posted yet