What is URL Phishing, and How to Prevent It

Bisma Farrukh

As the world continues to advance technologically, cyber threats also continue to evolve. One of the most common threats on the internet is phishing attacks, which often involve the use of phishing links or URLs.
URL phishing attacks are a serious threat that can result in losing sensitive information and financial loss. By being aware of the tactics used by cybercriminals and taking the necessary precautions, you can protect your online privacy from these attacks.
This blog post will provide a detailed overview of URL phishing, how it works, and, most importantly, how to prevent it.
Table of Contents
What is a Phishing link?
URL phishing, also known as “phishing,” is a type of cyber attack where an attacker creates a fake website that looks like a legitimate website to trick users into entering their login credentials, personal information, or financial data. This type of attack is often done through a phishing email, where the attacker sends a message that appears to be from a trusted source and includes a link to the fake website.
How Does It Work?
URL phishing attacks are usually carried out by cybercriminals who use various techniques to make phishing links appear legitimate. For example, they may use URL shorteners or create domains similar to legitimate ones but with slight variations.
Once victims click on the phishing link, they are redirected to a fake website that looks similar to the legitimate one. The phony website is designed to trick the victim into providing sensitive information, such as login credentials, which the attacker can use to gain unauthorized access to the victim’s account.
Another technique used in URL phishing attacks is the use of malware. In this case, when clicked, the phishing link is designed to download malware onto the victim’s computer or mobile device. Once installed, the malware can steal sensitive information from the victim’s device, such as login credentials or financial details.
Phishing vs. Malware?
Phishing and malware are both types of cyber attacks but differ in their methods and goals. Phishing is a social engineering attack that aims to trick users into revealing sensitive information. At the same time, malware is malicious software designed to infect a computer or network and cause damage.
Phishing attacks typically involve fraudulent emails, websites, or social media messages that appear to be from a trusted source, such as a bank or social media site. A phishing attack aims to trick users into revealing sensitive information, such as login credentials, credit card numbers, or other personal data.
Phishing attacks can also spread malware by tricking the user into downloading a file or clicking on a link containing malware.
On the other hand, malware is a type of software designed to harm a computer or network. Malware can take many forms, including viruses, worms, Trojans, and ransomware. Once installed on a computer or network, malware can cause various problems, such as stealing sensitive data, disrupting normal operations, or damaging hardware.

Here’s a head to head difference between Phishing and Malware:
| Phishing | Malware |
|---|---|
| A social engineering attack that aims to trick users into revealing sensitive information | Malicious software that is designed to infect a computer or network |
| Often involves the use of fraudulent emails, websites, or social media messages | Can be delivered through a variety of means, such as email attachments, software downloads, or infected websites |
| Does not require the use of software to be successful | Requires software to be installed on a computer or network |
| The goal is to obtain sensitive information, such as login credentials or credit card numbers | The goal is to cause harm to a computer or network, such as stealing data or disrupting normal operations |
| Can be used to deliver malware, such as by tricking the user into downloading a file or clicking on a link | Can be delivered through phishing attacks, such as by tricking the user into opening an infected email attachment or visiting an infected website |
| It relies on human error, such as clicking on a link or entering sensitive information | Can be spread automatically, without user interaction |
| Can be prevented through education and awareness, such as teaching users to identify phishing emails and websites | Can be prevented through the use of antivirus software, firewalls, and other security measures |
How To Prevent URL Phishing?
Preventing URL phishing attacks requires a combination of technology and user awareness. Here are some effective ways to prevent URL phishing attacks:
1. Install anti-phishing software
Anti-phishing software can help detect and block phishing links before they can do any damage. This software uses advanced algorithms to identify phishing URLs and warn users before they click on them.
2. Verify the URL before clicking
Before clicking on any link, always check the URL to ensure it is legitimate. Look for slight variations in the domain name or URL structure.
3. Be cautious of unsolicited emails
Phishing links are often distributed via unsolicited emails. Always be cautious of emails from unknown senders, especially if they ask you to click on a link or provide sensitive information.
4. Enable two-factor authentication
Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification and a password. This makes it more difficult for attackers to gain unauthorized access to your accounts, even if they have your login credentials.
How to identify a URL phishing attack
identifying a URL phishing attack requires a combination of vigilance, awareness, and knowledge of the common signs of phishing attacks. By following the tips outlined below, individuals and organizations can better protect themselves against these types of attacks and prevent the loss of sensitive information or the spread of malware:
1. Look for Inconsistencies in the URL
One of the most common signs of a URL phishing attack is inconsistencies in the URL. This can include misspellings or variations in the domain name, such as substituting “1” for “l” or using a similar-looking domain name. Additionally, be wary of URLs that use subdomains or subfolders that you need to become more familiar with or URLs that use non-standard characters or symbols.
2. Check for SSL/TLS Certificate
Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates to verify a website’s authenticity and integrity. A legitimate website will typically have an SSL/TLS certificate, which is indicated by the padlock icon in the browser address bar. If the URL of the website you visit does not have a padlock icon or the address bar is not green, it may be a sign of a phishing attack.
3. Examine the Website Design
Phishing websites are often designed to look like legitimate websites to trick victims into providing sensitive information. However, there may be subtle differences in the design that can indicate a phishing attack. Look for differences in the website’s color scheme, font, or layout. Additionally, be wary of pop-ups or requests for sensitive information when visiting the website.
4. Analyze the Content of the Website
Another sign of a URL phishing attack is the website’s content. Be wary of websites that request sensitive information such as login credentials, financial information, or personal information. Additionally, be cautious of websites that offer deals or promotions that seem too good to be true, as these may be a tactic to lure victims into providing sensitive information.
5. Trust Your Instincts
Finally, trust your instincts when identifying a URL phishing attack. If something seems suspicious or too good to be true, it may be a sign of a phishing attack. Always err on the side of caution and take steps to verify the website’s authenticity before providing any sensitive information.
Five different types of URL phishing
1. Masked Links
Masked links, also known as shortened URLs, are a common type of phishing link used to hide the link’s true destination. Masked links are created by using a URL shortening service, which generates a short URL that redirects to the original long URL.
Cybercriminals use masked links in phishing attacks to trick victims into clicking on legitimate links but redirecting to a fraudulent or malicious website.
2. Typosquatting
Typosquatting is a technique cybercriminals use to create fraudulent websites with domain names similar to legitimate websites. These fraudulent websites are designed to trick users into providing sensitive information such as login credentials, financial information, or personal information.
Typosquatting is achieved by registering domain names similar to legitimate websites but with slight spelling or punctuation variations.
3. Legit Links
Also known as homograph links, these are phishing links that use Unicode characters to create URLs that look similar to legitimate websites. These characters are designed to look identical or similar to those used in legitimate URLs but are actually different.
This technique is used to trick victims into clicking on a link that appears to be legitimate but leads to a fraudulent or malicious website.
4. Subfolder Links
They are also known as deep links, a type of phishing link that uses a URL that appears to be legitimate but leads to a specific subfolder on a website. This technique is used to trick victims into thinking they are on a legitimate website when they are on a subpage of a fraudulent or malicious website.
Cybercriminals use this technique to make their fraudulent websites appear more legitimate and increase the likelihood that victims will provide sensitive information.
5. Malformed prefix links
These are a type of phishing link that uses a URL with a malformed prefix, such as “htp://” instead of “http://.” This technique is used to trick victims into thinking they are on a legitimate website when they are on a fraudulent or malicious website. Cybercriminals use this technique to exploit victims who do not pay close attention to the URL or do not understand how URLs work.
What does a phishing URL look like?
A phishing URL is a hyperlink sent to a recipient via email, text message, or social media with the intent to steal personal information or install malware on the recipient’s device. Phishing URLs often resemble legitimate links but contain subtle differences that make them dangerous. Here are some signs to look for:
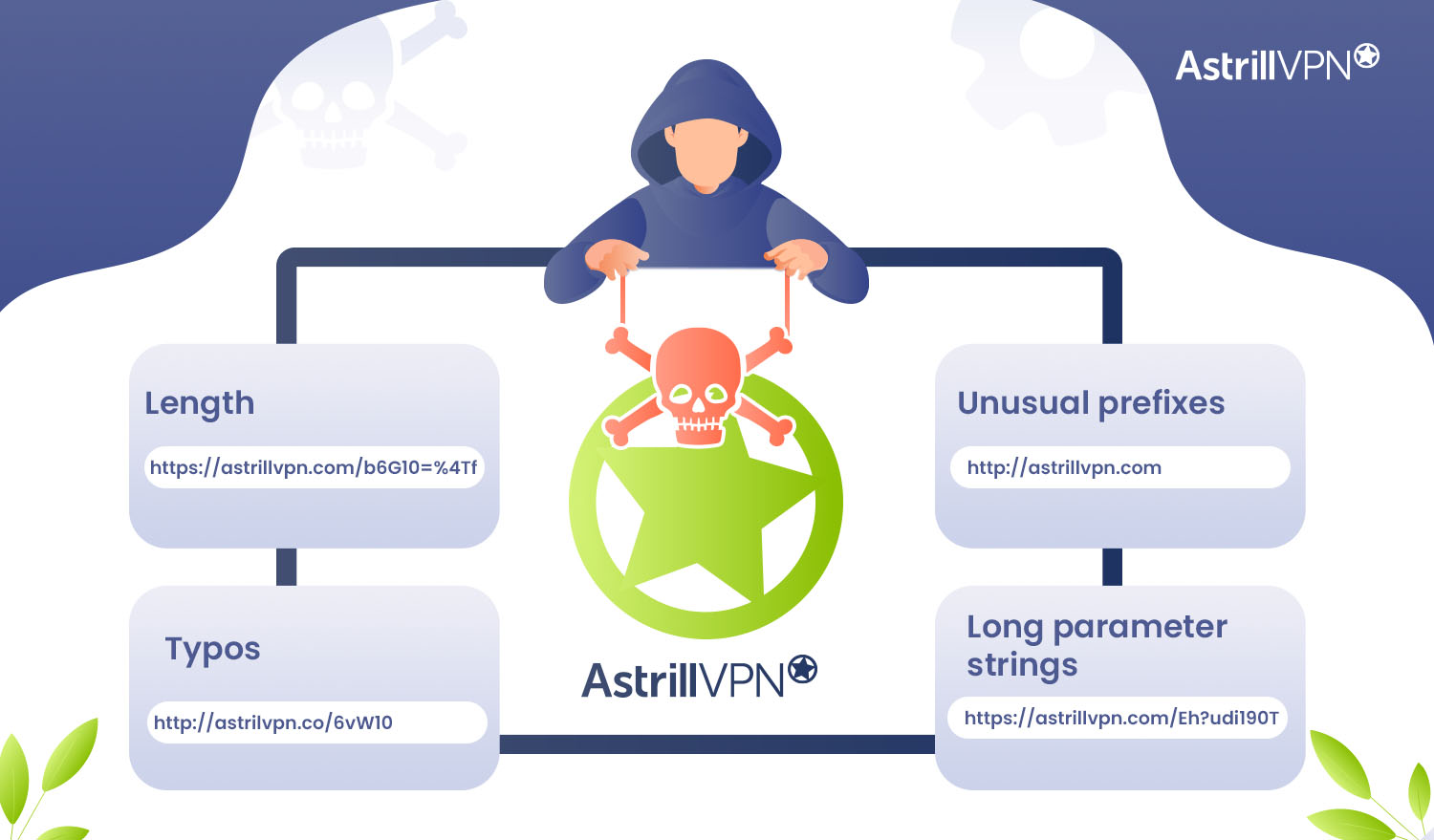
- Length
Phishing URLs tend to be excessively long and contain random characters. The randomness makes it difficult to spot that the URL does not belong to a trustworthy source. Legitimate URLs are usually short and contain only relevant keywords.
- Typos
Hackers often make intentional typos in phishing URLs to disguise the actual website they are imitating. For example, instead of “paypal.com,” the URL may read “paypai.com” with an “i” instead of an “l.”
- Unusual prefixes
While “https://” is common, phishing URLs may use prefixes like “http://” or odd combinations of numbers, symbols, and letters before the domain name.
- Long parameter strings
Phishing URLs often contain long strings of random characters and numbers after a question mark. These parameters are designed to pass along malicious codes or track recipients.
In general, be wary of clicking on any URL in an unexpected email, text message, or social media post. If the link is related to an account or service you use, navigate to the website directly through your browser and log in from there.
How do I know if a URL is safe?
When you receive a link in an email, text message, or social media post, how can you determine if it’s safe to click?
The first step is to inspect the URL itself. Look closely at the web address to see if it contains any red flags.
Some signs a URL may be unsafe include:
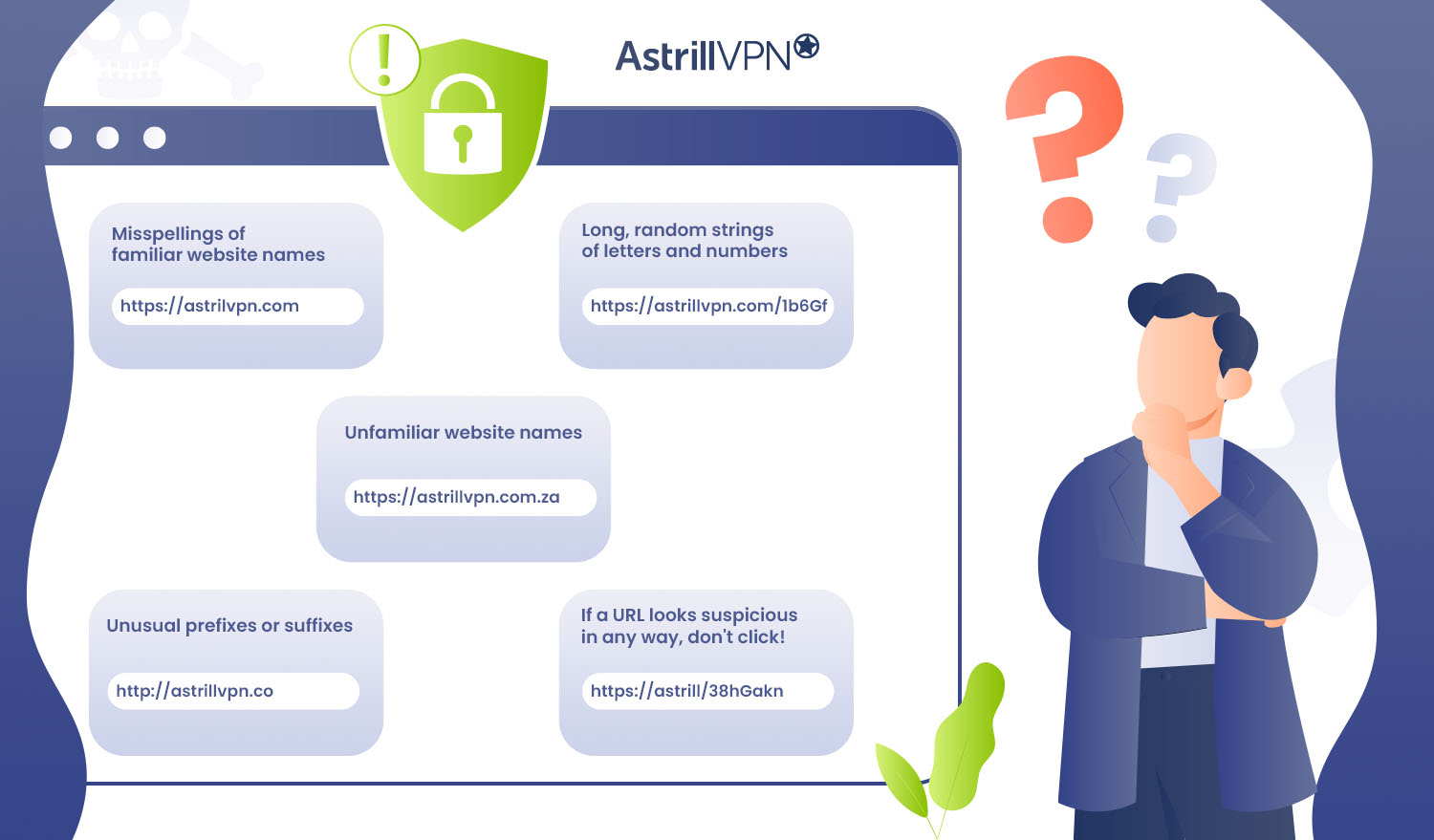
- Misspellings of familiar website names
Scammers often buy misspelled domain names that are similar to legitimate websites in the hopes of tricking people. Check the spelling of the domain name carefully.
- Unfamiliar website names
If you’ve never heard of the website being linked, that’s a warning sign. Don’t click on links from unfamiliar sites unless you’re sure the source is trustworthy.
- Unusual prefixes or suffixes
URLs with strange prefixes like “http://” instead of “https://” or unusual suffixes like “.co” instead of “.com” could be suspicious. Legitimate websites tend to use standard URL structures.
- Long, random strings of letters and numbers
Scammers often generate long URLs with random characters to hide the actual destination. Avoid clicking on these.
- If a URL looks suspicious in any way, don’t click!
The safest practice is to type website addresses directly into your browser instead of clicking links, especially from unfamiliar sources. You can also hover your mouse over a link to see the full URL before clicking, which may reveal any red flags.
Applying a bit of caution and common sense will help keep you safe online.
Recent Examples of URL Phishing Cases that Shook the World
Cyber attacks aren’t something rare, and every now and then, we get to hear about a cyber attack on some popular business or brand. The state of online privacy is highly turbulent as the number of cyber-attacks has grown exponentially over the years.
Here are some of the recent URL phishing cases that have occurred worldwide:
1. SolarWinds supply chain attack
In December 2020, it was revealed that hackers had breached the SolarWinds software company and used it as a supply chain attack to target multiple US government agencies and other organizations.
The attackers used a sophisticated phishing campaign to trick SolarWinds employees into downloading malware, which was then used to steal data and compromise the company’s network.
2. Microsoft Exchange Server hack
It was discovered that in March 2021, a Chinese hacking group had exploited vulnerabilities in Microsoft Exchange Server software to launch a massive phishing campaign.
The attackers sent emails containing malicious links to thousands of organizations worldwide, which, when clicked, allowed the hackers to gain access to the target’s network and steal data.
3. COVID-19 vaccine phishing scams
In early 2021, several countries reported an increase in phishing attacks related to COVID-19 vaccines. Attackers sent emails and text messages claiming to offer early access to vaccines or asking for personal information to register for the vaccine. These phishing scams were designed to steal personal and financial information or to distribute malware. The type of phishing scam in this case, was Typosquatting.
4. Google Workspace phishing attacks
A new phishing campaign was discovered in February 2021 that targeted users of Google Workspace (formerly G Suite) by sending emails that appeared to come from legitimate sources, such as an IT help desk or a file-sharing service. The emails contained a link to a fake login page, which allowed the attackers to steal the victim’s Google credentials.
5. Amazon Prime Day phishing scam
It was reported that cybercriminals had launched a phishing campaign targeting shoppers during Amazon Prime Day in October 2021. The phishing emails claimed to offer discounts and other deals, but when the victim clicked on the link, they were taken to a fake website that requested their login credentials and other personal information.
How to protect against URL phishing?

1. URL Filtering
URL filtering is a technique used to block access to known malicious websites. This technique involves analyzing the URLs of websites and blocking access to those identified as malicious. Many security solutions offer URL filtering capabilities, which can block access to known malicious websites and prevent users from inadvertently visiting them.
2. Use a VPN
Using a VPN can provide additional protection against URL phishing attacks by encrypting all internet traffic between the user’s device and the VPN server. This encryption prevents attackers from intercepting the traffic and accessing sensitive information like login credentials.
When users connect to AstrillVPN, their data is sent through an encrypted tunnel before reaching the VPN server. No one, not even the attackers, can snoop on the data traveling via this tunnel.
When users click on a link in an email or type in a URL, their request is first sent to the VPN server. The server then forwards the request to the destination website. This means that the user’s IP address and location are hidden from the website they are visiting, making it more difficult for attackers to track their online activities and carry out phishing attacks.
AstrillVPN offers AES 256-bit encryption that protects your online privacy by encrypting your traffic and making you untraceable. Also, once connected to an AstrillVPN server, it uses web filtering to block malicious websites and prevent users from entering sensitive information on unsafe sites.
3. Domain Reputation Checks
It involves analyzing the reputation of a domain to determine if it is trustworthy or not. This involves analyzing the domain name, IP address, and other factors to determine if the domain is associated with known malicious activity. Many security solutions offer domain reputation check capabilities, which can be used to identify and block access to domains associated with known phishing attacks.
4. Artificial Intelligence (AI) Based Protection
AI-based protection involves using machine learning algorithms to identify and block phishing attacks. This technique involves analyzing large amounts of data to identify patterns and trends associated with phishing attacks. AI-based protection tools can be used to identify and block new and emerging phishing attacks, which traditional security solutions may not detect.
5. Security Awareness
It is critical to protect against URL phishing attacks as this involves educating users about the common signs of phishing attacks and providing them with the knowledge and skills to identify and avoid them. This can include training on how to identify suspicious URLs, how to check the authenticity of websites, and how to report suspected phishing attacks.
How to report phishing URLs
Reporting phishing URLs is an important step in the fight against phishing attacks. By reporting phishing URLs, you can help to take down fraudulent websites, prevent other users from falling victim to the same attack, and contribute to the overall effort to combat cybercrime.
Follow these steps for reporting phishing URLs:
- Before you navigate away from the phishing website, take a screenshot of the page. This will provide evidence of the phishing attempt and help the authorities investigate and act against the attackers.
- Many web browsers and email clients have a built-in reporting feature that allows you to report a phishing URL directly from the page. Look for a button or link that says “Report Phishing” or “Report Suspicious Activity.”
- If no reporting option is available, you can report the phishing URL to the appropriate authority. Depending on where you are located, this may be your national Computer Emergency Response Team (CERT), a law enforcement agency, or a cybersecurity organization. You can typically find contact information for these organizations online.
- When reporting a phishing URL, provide as much detail as possible about the attack. Include the URL of the phishing page, the date and time you received the email or visited the website, and any other relevant information, such as the email address or phone number used in the attack.
- After reporting the phishing URL, follow up with the appropriate authority to ensure that they received your report and are taking action to investigate the attack.
FAQs
What happens if I open a phishing link?
Clicking on a phishing link may result in stolen personal information or malware installation, compromising the security of the device and its data.
What makes a URL suspicious?
A URL may be suspicious if it contains spelling or formatting errors, lacks HTTPS, or prompts for sensitive information unexpectedly.
What happens if I click on a phishing link?
Clicking on a phishing link can lead to losing personal information or unauthorized access to the device or network.
What makes a URL suspicious?
A URL may be suspicious if it contains irrelevant or unusual content, has a suspicious domain, or prompts for sensitive information without proper security measures.

No comments were posted yet