Phishing Email Examples: How to Spot and Avoid Online Scams

Arsalan Rathore

Phishing emails are a prevalent and dangerous cyber threat, designed to trick recipients into revealing sensitive information like passwords or credit card numbers. These fraudulent messages often mimic trusted sources, making them hard to identify.
The goal of phishing is to steal personal or financial data, spread malware, or gain unauthorized access to systems. Cybercriminals use psychological tactics, urgency, and fear to push victims into clicking malicious links or downloading harmful attachments.
This guide highlights real-world phishing examples, red flags to watch for, and practical tips for staying secure. Let’s equip ourselves with the knowledge to outsmart cybercriminals.
Table of Contents
Common Types of Phishing Emails
Phishing emails come in many forms, each tailored to exploit vulnerabilities or target particular groups. Understanding the different types of phishing emails is essential for recognizing and defending against these attacks. Below, we’ve outlined the most common types of phishing emails and examples to help you stay informed and vigilant.
2.1 Deceptive Phishing
The most common type is deceptive phishing, in which attackers impersonate trusted entities like banks, social media platforms, or online retailers. The goal is to trick recipients into sharing sensitive information, such as login credentials or credit card details.
For example, you might receive an email claiming to be from your bank, stating that your account has been compromised and urging you to click a link to “verify your details.” The link leads to a fake login page designed to steal your credentials. These emails often use urgent language and appear legitimate at first glance, making them highly effective.
2.2 Spear Phishing
Spear phishing takes a more targeted approach. Attackers research their victims and craft personalized emails referencing specific details, such as their job title, recent purchases, or workplace events.
For instance, an employee might receive an email from what appears to be their company’s IT department referencing a recent meeting and asking them to reset their password due to a “system upgrade.” The email includes the employee’s name and job title, making it credible. Attackers often gather personal information from social media or previous data breaches to make their emails more convincing.
2.3 Whaling (CEO Fraud)
Whaling attacks target high-profile individuals, such as executives or senior managers, often impersonating top-level executives to pressure employees into taking action. For example, a finance team member might receive an email from the “CEO,” urgently requesting a wire transfer for a “confidential business deal.” The email uses authoritative language and bypasses normal approval processes, creating a sense of urgency that compels the recipient to act without verification.
2.4 Pharming
Pharming is a more technical form of phishing that redirects users to fake websites, even if they type the correct URL. This is often achieved through malware or DNS hijacking, making it harder to detect. For instance, you might attempt to visit your bank’s website only to be redirected to a fraudulent site that looks identical to the real one. Unknowingly, you enter your login details, which the attacker then captures. This attack often relies on malware or DNS hijacking to manipulate web traffic.
2.5 Clone Phishing
In clone phishing, attackers create a near-identical copy of a legitimate email you’ve previously received, replacing legitimate links or attachments with malicious ones. For example, you might receive an email that appears to duplicate a recent invoice from a vendor. However, the attachment or link in the email has been replaced with a malicious version designed to install malware or steal information. The email may claim to be an “updated” or “resent” version to explain its reappearance.
Real-Life Phishing Email Examples
Phishing emails are designed to look legitimate, but upon closer inspection, they often reveal subtle clues that expose their true intent. Let’s look at real-life phishing email examples to understand how cybercriminals operate and what makes these emails so convincing and dangerous.
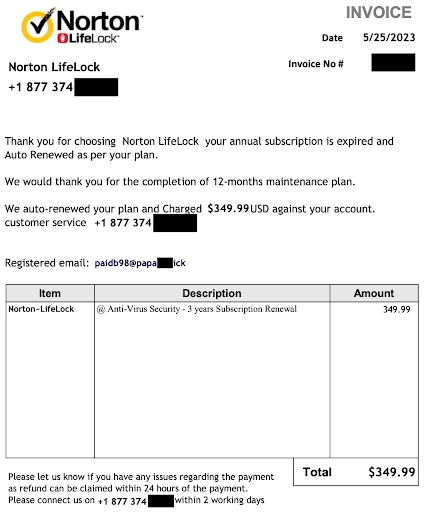
The Fake Invoice Scam
Imagine receiving an email from a vendor you’ve worked with. The subject line reads, “Overdue Invoice—Payment Required. ” The email claims you have an outstanding payment for services rendered. Attached is an invoice with your company’s logo and details, making it seem authentic. The email urges you to click a link to view the invoice or make the payment immediately to avoid service disruption.
At first glance, the email appears legitimate, but a closer look reveals red flags. The sender’s email address doesn’t match the vendor’s official domain, and the link provided leads to a suspicious website. The message’s urgency is also a telltale sign, cybercriminals often use pressure tactics to prevent you from scrutinizing the email too closely.
Here’s an example about how a fake invoice looks like:
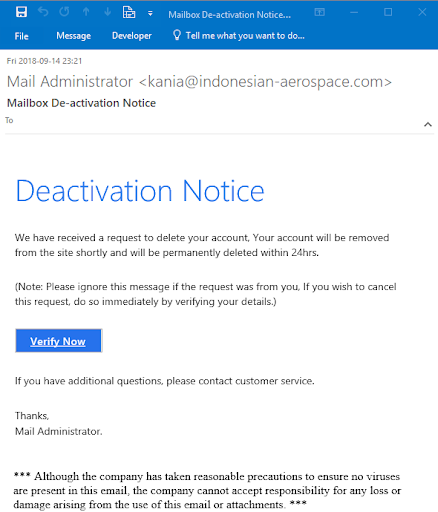
The Urgent Account Verification Request
Another common phishing tactic involves impersonating well-known companies like banks, social media platforms, or online retailers. For example, you might receive an email with the subject line, “Action Required: Verify Your Account Now.” The email claims that unusual activity has been detected on your account and instructs you to click a link to verify your information.
The email looks official, complete with the company’s logo and branding. However, the link provided doesn’t match the company’s official website, and the sender’s email address is slightly altered (e.g., support@secure-paypal.com instead of support@paypal.com). Urgent language, such as “failure to act within 24 hours will result in account suspension,” is a classic phishing tactic designed to provoke immediate action.
Here’s how the urgent account verification request looks like:
The Prize or Lottery Scam
Who wouldn’t be excited to receive an email announcing they’ve won a million dollars? Phishing emails often exploit this excitement by claiming you’ve won a lottery or prize. The email might say, “Congratulations! You’ve Won $1,000,000!” and instruct you to provide personal information or pay a small fee to claim your prize.
While the promise of a life-changing sum of money is tempting, these emails are almost always scams. The sender’s email address is unrelated to any legitimate organization, and the request for sensitive information or upfront payment is a clear red flag. Remember, if something seems too good to be true, it probably is.
The Fake Job Offer
Job seekers are often targeted with phishing emails that appear to be from recruiters or hiring managers. These emails offer lucrative job opportunities with minimal requirements and a high starting salary. For example, you might receive an email with the subject line, “Exciting Job Opportunity – Immediate Hiring!” The email asks you to complete an attached application form and provide sensitive information like your Social Security Number for background verification.
While the offer might seem enticing, it’s important to verify the sender’s legitimacy. Research the company and contact them through their official website to confirm the job offer. Legitimate employers will never ask for sensitive information or upfront fees during hiring.
The Brand Impersonation Scam
Phishing emails often impersonate trusted brands like Amazon, PayPal, or Microsoft. For instance, you might receive an email with the subject line, “Suspicious Activity Detected on Your Amazon Account.” The email claims that your account has been compromised and instructs you to click a link to verify your information.
The email looks official, complete with the brand’s logo and formatting. However, the provided link leads to a fake login page that steals your credentials. The sender’s email address is also suspicious, slightly different from the brand’s official domain. Always log in to your account directly through the official website or app to check for any issues.
How to Identify a Phishing Email: Red Flags
Phishing emails can be convincing, but they often contain subtle clues that give them away. Here are the most common red flags to watch for:
Suspicious Sender Addresses
The email comes from an address that doesn’t match the official domain of the organization it claims to represent. For example, an email from “support@paypal-security.com” instead of “support@paypal.com.”
Generic Greetings
The email uses generic greetings like “Dear Customer” or “Dear User” instead of your name. Legitimate organizations usually address you by your full name.
Urgent or Threatening Language
The email pressures you to act immediately, often using phrases like “Your account will be suspended” or “Immediate action required.” Cybercriminals use urgency to prevent you from thinking critically.
Unusual Links or Attachments
The email contains links that don’t match the official website URL or attachments you weren’t expecting. Hover over links to check their destination before clicking.
Poor Grammar and Spelling
The email contains obvious grammatical errors, awkward phrasing, or misspelled words. Legitimate organizations typically proofread their communications.
Requests for Sensitive Information
The email asks for personal or financial information, such as passwords, Social Security Numbers, or credit card details. Legitimate companies will never ask for this via email.
Mismatched Branding
The email uses logos or branding that look slightly off, such as low-quality images or incorrect colors.
How to Protect Yourself from Phishing Emails
Phishing emails are a constant threat, but with the right precautions, you can significantly reduce your risk of falling victim to these scams. Here are some practical steps to protect yourself:
1. Use Email Filters and Antivirus Software
Enable spam filters on your email account to detect and block phishing emails. Additionally, install reputable antivirus software to scan for malware and other threats from suspicious emails.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security to your accounts. Even if a phishing attack compromises your password, 2FA prevents unauthorized access by requiring a second verification form, such as a code sent to your phone.
3. Keep Your Software Updated
Update your operating system, email client, and antivirus software regularly to protect against the latest security vulnerabilities. Cybercriminals often exploit outdated software to launch phishing attacks.
4. Use a VPN for Secure Browsing
AstrillVPN encrypts your internet connection, making it harder for attackers to intercept your data or redirect you to malicious websites. This is especially important when accessing sensitive accounts or using public Wi-Fi.
What to Do If You Receive a Phishing Email
Acting quickly and carefully is important if you suspect you’ve received a phishing email. Here’s what you should do:
Do Not Click Links or Download Attachments
Avoid interacting with any links, buttons, or attachments in the email. These could lead to malicious websites or install malware on your device.
Report the Email
Forward the email to your IT department (if you’re at work) or report it to your email provider (e.g., Gmail, Outlook). Most email platforms have a “Report Phishing” option to help combat these threats.
Mark as Spam or Phishing
Use your email client’s “Mark as Spam” or “Report Phishing” feature to move the email to your spam folder. This helps improve your email provider’s filters and prevents similar emails from reaching your inbox.
Verify the Sender
If the email claims to be from a company or organization, contact them directly using their official website or customer support number, not the contact information provided in the email.
Change Your Passwords
If you accidentally click on a link or provide sensitive information, change your passwords immediately. Use strong, unique passwords and enable two-factor authentication (2FA) for added security.
Scan Your Device for Malware
If you downloaded an attachment or clicked a link, run a full antivirus scan on your device to check for malware or other threats.
Conclusion
Phishing emails remain a major cybersecurity threat, exploiting human psychology and technical loopholes to steal sensitive information. As cybercriminals become more sophisticated, it’s crucial to stay vigilant, recognize red flags, and adopt proactive security measures.
By understanding the different types of phishing attacks, identifying common warning signs, and implementing security best practices, such as enabling two-factor authentication, using email filters, and staying cautious with unsolicited messages, you can significantly reduce the risk of falling victim to phishing scams.
Cybersecurity is a shared responsibility, and knowledge is your best defense. Stay informed, double-check suspicious emails, and always think before you click. If you suspect a phishing attempt, report it immediately to the relevant authorities or your IT department. Your awareness and caution can prevent cybercriminals from succeeding.

No comments were posted yet