Understanding Ransomware-as-a-Service: The Cyber Threat Landscape

Arsalan Rathore
Ransomware-as-a-Service (RaaS) represents a transformative evolution in the cybercrime landscape. By operating as a subscription-based model, RaaS provides cybercriminals with ready-made ransomware tools, significantly lowering the barriers to launching attacks. This “ransomware marketplace” allows even inexperienced actors to execute complex attacks, leading to a surge in ransomware incidents globally.
The impact of RaaS is felt across all sectors, from small businesses to large enterprises, as attackers increasingly target critical data and operations. Understanding the Ransomware as a Service model, its methods, and its implications is crucial for businesses and individuals. This guide looks at how RaaS works, the dangers it brings, and some tips on how to keep yourself safe from this fast-growing threat in our digital world.
Table of Contents
What is Ransomware as a Service (RaaS)?
Ransomware as a Service (RaaS) is a subscription-based model that enables cybercriminals to lease pre-configured ransomware tools from developers, similar to the Software as a Service (SaaS) model. It allows individuals with minimal technical expertise to launch sophisticated ransomware attacks, bypassing the need to develop malware independently.
Growing Significance of RaaS in Cybersecurity
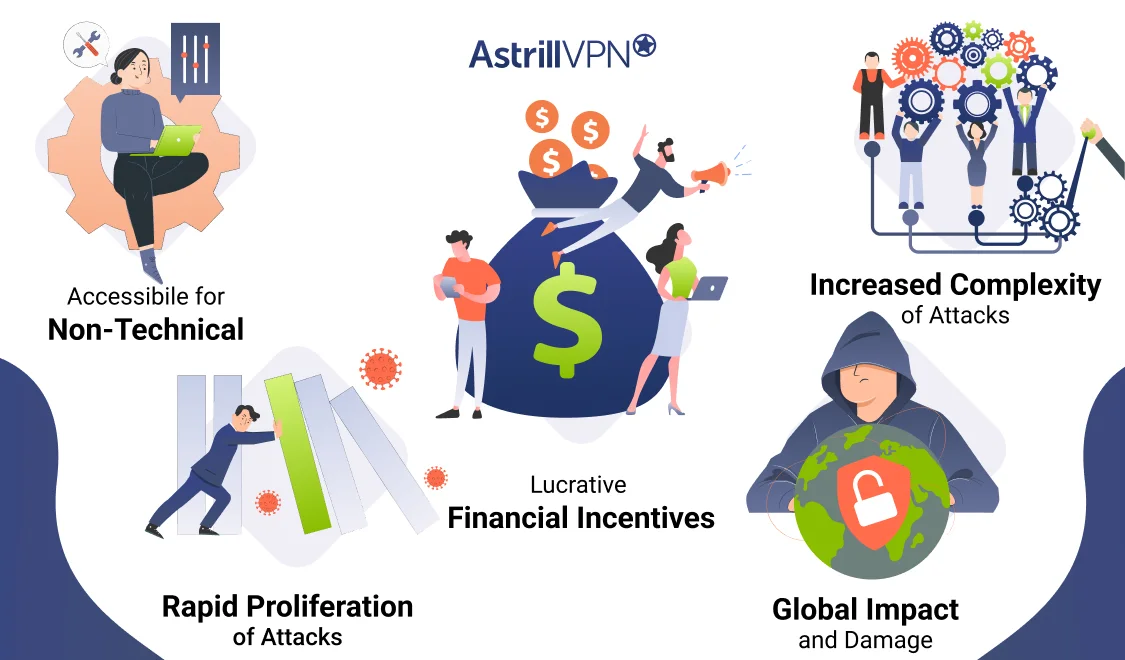
1. Accessibility for Non-Technical Threat Actors
RaaS significantly lowers cybercriminals’ barriers to entry by offering ready-made ransomware tools paired with guides, dashboards, and technical support. This has dramatically expanded the pool of potential attackers.
2. Rapid Proliferation of Attacks
The subscription or commission-based structure incentivizes affiliates to carry out as many attacks as possible, leading to a rise in both the frequency and scope of ransomware incidents.
3. Lucrative Financial Incentives
With ransom demands often reaching hundreds of thousands of dollars and payouts made in untraceable cryptocurrencies, RaaS has become a highly profitable venture for developers and affiliates.
4. Increased Complexity of Attacks
Affiliates can use these tools to target specific vulnerabilities, employ double-extortion tactics, and breach complex systems, including those of critical infrastructure and multinational corporations.
5. Global Impact and Damage
From disrupting healthcare services to compromising government agencies, RaaS-enabled attacks have caused significant economic losses and operational downtime worldwide, making them a critical focus in cybersecurity.
How Does Ransomware as a Service Work?
Ransomware as a Service (RaaS) is a subscription-based cybercrime model where skilled developers create and lease ransomware to affiliates who carry out the attacks. This streamlined process democratizes access to sophisticated cyber tools, enabling novice and seasoned attackers to profit from ransomware campaigns.
Major Threats Posed by RaaS
Ransomware as a Service (RaaS) has significantly altered the cyber threat landscape by democratizing access to sophisticated attack tools. This model enables even those without technical expertise to launch destructive ransomware attacks, which can have devastating consequences for individuals, businesses, and government organizations. Below are some of the major threats posed by RaaS:
1. Increased Frequency and Scale of Attacks
One of the most significant threats RaaS poses is the unprecedented scale and frequency of ransomware attacks. By lowering the barrier to entry for cybercriminals, RaaS has resulted in a sharp increase in ransomware incidents. Organizations, especially those with weak cybersecurity defenses, are prime targets. RaaS operations are highly scalable, enabling affiliates to target multiple organizations simultaneously or across different regions. This has led to a dramatic rise in ransomware infections, with industries like healthcare, finance, and critical infrastructure often being in the crosshairs.
2. Financial and Operational Losses
Ransomware attacks, particularly those carried out through RaaS platforms, can have crippling financial consequences. When systems are locked, businesses may face prolonged downtime, impacting revenue and operational efficiency. Furthermore, the ransom demands can run into hundreds of thousands, if not millions, of dollars, especially for larger organizations.
3. Double and Triple Extortion
RaaS has introduced more complex extortion strategies, such as double and triple extortion. Double extortion refers to the practice of not only encrypting a victim’s data but also stealing it and threatening to release it publicly unless the ransom is paid. This adds pressure on organizations, increasing the potential harm to their reputation and compliance obligations, especially for industries with strict data privacy regulations.
Triple extortion takes it a step further, with cybercriminals threatening to launch Distributed Denial of Service (DDoS) attacks on the victim’s infrastructure or expose sensitive data not just to the organization but also to its clients and partners. This increases the attackers’ leverage and makes the ransom demands even more difficult for businesses to ignore.
4. Disruption of Critical Infrastructure
RaaS has been particularly dangerous for critical infrastructure, including healthcare, energy, and government sectors. Attacks targeting hospitals and emergency services have disrupted operations, putting lives at risk. The healthcare sector is particularly vulnerable, as ransomware attacks can delay medical procedures, interrupt patient care, and compromise sensitive medical data. Such disruptions’ financial, operational, and human costs can be catastrophic.
5. Data Privacy and Compliance Violations
With RaaS operators frequently using double and triple extortion methods, data privacy and compliance risks are significant. Organizations that handle sensitive customer data, such as financial institutions or healthcare providers, are prime targets for ransomware attacks. Such data breaches often lead to serious legal and regulatory consequences, especially with the implementation of GDPR and other data privacy laws.
6. Evolving Tactics and Ransomware Variants
RaaS developers continuously evolve their tactics to evade detection and thwart cybersecurity defenses. New ransomware variants are introduced regularly, each with different encryption, propagation, and extortion methods. The introduction of polymorphic ransomware, which changes its code to evade signature-based detection, and ransomware that targets cloud environments makes it harder for traditional security measures to keep up.
Notable RaaS Groups and Common Ransomware Attacks
Ransomware as a Service (RaaS) has led to the rise of highly organized criminal groups and affiliates that specialize in deploying ransomware attacks. These groups are responsible for some of the most high-profile and damaging ransomware incidents in recent years. Some notable RaaS groups and their variants include:
REvil (Sodinokibi)
REvil, also known as Sodinokibi, is one of the most infamous RaaS groups. It gained prominence for its sophisticated attacks targeting various industries, from healthcare to critical infrastructure. REvil operates on a “ransomware-as-a-service” model, providing affiliates with the tools to launch ransomware attacks. The group typically demands high ransoms, often in the millions of dollars. It has been involved in numerous data breaches, including the attack on the global IT company Kaseya in 2021, which impacted hundreds of businesses worldwide.
The REvil group also made headlines for publicly auctioning off stolen data if the ransom wasn’t paid, a tactic known as double extortion. This further incentivized victims to comply, increasing the financial pressure on organizations.
Conti
Conti is another notorious ransomware group that operates under the RaaS model. Known for its speed and efficiency, Conti has been responsible for multiple large-scale attacks, particularly on critical infrastructure sectors, including healthcare, education, and government. In 2021, Conti became one of the most active ransomware families, using highly sophisticated attack vectors such as phishing and exploiting zero-day vulnerabilities.
DarkSide
DarkSide gained notoriety in 2021 after launching a high-profile attack on Colonial Pipeline, one of the largest pipeline operators in the U.S. This attack disrupted fuel supplies across the East Coast of the U.S. and caused widespread panic, highlighting the group’s capacity for strategic targeting. DarkSide is considered a “professional” RaaS group, known for carefully planning and targeting high-value targets, particularly in industries with critical infrastructure.
LockBit
LockBit is a RaaS group known for its quick and highly automated ransomware attacks. The group has been behind several large attacks targeting corporations across various industries. Its ransomware variant, LockBit 3.0, is highly customizable, allowing affiliates to tweak it to suit their needs. LockBit has become notorious for its speed, with some variants able to encrypt an entire network in minutes.
LockBit also uses double extortion, with stolen data threatened with public release if the ransom isn’t paid. The group often targets larger organizations, particularly those with a significant financial capacity to pay large ransoms.
Hive
Hive ransomware operates under a RaaS model and has been one of the most active families. Affiliates target a broad range of sectors, including healthcare, finance, and manufacturing. Hive ransomware is known for its unique encryption algorithms and for exploiting known vulnerabilities, particularly in software like Microsoft Exchange.
In addition to the typical ransom demands, Hive has also engaged in double extortion, where they steal sensitive data and demand payment for its safe return. The group has been linked to several high-profile breaches, including attacks on healthcare providers, where the ransom demands were designed to be paid quickly to avoid jeopardizing patient care.
The Economics of RaaS
The economics of Ransomware as a Service (RaaS) is a significant driver of the rising number of ransomware attacks worldwide. The RaaS model has lowered the barrier to entry for cybercriminals, enabling those with minimal technical expertise to launch sophisticated ransomware attacks. This has created a lucrative underground economy that rewards both the developers and the affiliates involved in RaaS operations.
Revenue Sharing Model
The RaaS model operates on a revenue-sharing structure. RaaS developers (operators) provide ransomware tools, infrastructure, and support to affiliates in exchange for a percentage of the ransom payments. This percentage typically ranges from 20% to 40%, depending on the agreement between the developer and the affiliate. In some cases, affiliates are provided with detailed instructions, customer support, and even training to maximize the effectiveness of their attacks.
For example, in the case of REvil, the developers typically took 20% of the ransom payment, while affiliates kept the remaining 80%. This model ensures that both parties benefit financially from successful attacks, making RaaS an appealing and scalable business for cybercriminals.
Cost of Entry for Affiliates
Becoming an affiliate in the RaaS ecosystem is often inexpensive and relatively easy. While there may be initial fees or subscriptions to access RaaS platforms, these costs are generally low compared to the potential profits from a successful attack. Some RaaS groups, like Conti, may require a fee for access to their infrastructure, but this fee is often recouped quickly through the ransoms paid by victims.
Additionally, RaaS developers may offer additional services or upgrades, such as tools to bypass security measures, more customizable ransom demands, or additional decryption keys to increase the likelihood of receiving payment. These add-ons create further opportunities for developers to profit from their ransomware operations.
High-Reward, Low-Risk Strategy
One of the primary attractions of RaaS for affiliates is the high-reward, low-risk nature of the business model. For many affiliates, the risk of being caught or facing significant legal consequences is lower than other forms of cybercrime. While law enforcement agencies are increasingly cracking down on ransomware operations, many affiliates operate under pseudonyms and use advanced encryption and anonymizing tools like VPNs and the dark web to remain undetected.
This low-risk environment encourages more individuals to join the RaaS ecosystem and launch attacks globally. The profits from a successful ransomware attack can range from tens of thousands to millions of dollars, especially when targeting high-value industries such as healthcare, finance, or government.
Double Extortion as a Profit Maximizer
Double extortion is a tactic that has greatly increased the profitability of RaaS operations. In addition to encrypting a victim’s data and demanding a ransom for decryption, attackers now steal sensitive information and threaten to release it if the ransom is unpaid. This increases the pressure on victims, especially organizations with valuable intellectual property or personal data.
By leveraging double extortion, RaaS affiliates can often secure higher ransoms, as organizations are not only paying for decryption but also to prevent the exposure of sensitive information. This model has been particularly effective in industries where data confidentiality is paramount, such as finance, healthcare, and legal services.
The Role of Cryptocurrency
Cryptocurrency has become the preferred payment method in the RaaS economy due to its anonymity and ease of use. Ransom payments are often made in cryptocurrencies such as Bitcoin, Monero, or Ethereum, which makes it harder for law enforcement to trace the transactions. This decentralized nature of cryptocurrency helps cybercriminals evade detection while facilitating global transactions without intermediaries.
Cryptocurrency has made it easier for RaaS affiliates to operate across borders, creating a truly global economy of ransomware attacks. As cryptocurrency grows in popularity, RaaS operations will likely continue to thrive, further expanding the scale of the ransomware threat.
Industry Profits and Future Outlook
The financial incentives provided by RaaS have led to exponential growth in ransomware attacks. According to estimates, the global cost of ransomware attacks reached billions of dollars annually, showing no signs of slowing down. As the RaaS ecosystem grows, the financial rewards for cybercriminals will continue to drive new individuals into the field, leading to more sophisticated attacks and evolving business models.
How to Protect Against RaaS Attacks
Ransomware-as-a-service (RaaS) attacks present a growing threat to organizations and individuals. Protecting against them requires a comprehensive strategy incorporating technical safeguards, employee training, and proactive preparation. Here’s how to mitigate the risks of RaaS attacks:
1. Educate and Train Employees
Cybercriminals often exploit human vulnerabilities through phishing emails and malicious links. Regularly educate employees on identifying suspicious activities, such as unexpected email attachments or URLs. Simulated phishing exercises can help employees practice spotting threats, while clear reporting procedures ensure swift responses to potential risks.
2. Enforce Strong Access Controls and Authentication
Restrict access to systems and data by applying the principle of least privilege—granting employees only the access necessary for their roles. Use multi-factor authentication (MFA) to add a layer of security, making it harder for attackers to gain unauthorized access even if credentials are compromised. Regularly review and adjust permissions to ensure they align with employees’ roles.
3. Maintain Reliable Backups
Frequent, automated backups are a cornerstone of ransomware defense. To ensure data integrity, store backups in secure, offline locations or use cloud storage with encryption. Test backups regularly to verify their reliability and the speed of recovery. This ensures critical data is available even in the event of an attack.
4. Update and Patch Software Regularly
Many ransomware attacks exploit outdated systems and software. Implement a robust patch management process to ensure all operating systems, applications, and firmware are up-to-date. Automated patching tools can help streamline this process, closing security gaps before they can be exploited.
5. Use Endpoint Protection Solutions
Deploy advanced endpoint security solutions, such as Endpoint Detection and Response (EDR), to identify and neutralize threats at their source. These tools monitor for unusual behavior, like unauthorized file encryption, and stop ransomware before it can spread. AI-powered solutions can also detect emerging threats based on behavior patterns.
6. Segment Your Network
Network segmentation limits the spread of ransomware by isolating systems and data. Organizations can contain an attack within a single segment by dividing networks into smaller, secure sections. This strategy is especially critical for protecting sensitive systems and data from broader exposure.
7. Implement a Zero-Trust Security Model
Adopt a zero-trust approach, treating all users and devices as potential threats. Continuously verify access requests based on user behavior, device health, and role-specific policies. Zero-trust strategies help minimize unauthorized access and lateral movement within networks.
8. Use a Secure VPN for Remote Connections
A VPN, such as AstrillVPN, encrypts internet traffic and masks IP addresses for remote workforces. This prevents attackers from intercepting sensitive data during transmission and provides additional protection for employees accessing corporate systems remotely.
9. Monitor and Respond to Threats Proactively
Continuous monitoring of network activity can help identify and respond to suspicious behavior before it becomes a larger issue. Establish an incident response plan that outlines steps to take in case of an attack, ensuring rapid containment and recovery.
The Future of RaaS
The future of Ransomware-as-a-Service (RaaS) looks poised to grow in sophistication and impact, driven by technological advancements and the increasing accessibility of cybercrime tools. Understanding the potential trajectory of RaaS is crucial for individuals, organizations, and cybersecurity professionals to prepare for emerging threats.
Enhanced Customization and Targeting
Future RaaS operations may incorporate advanced targeting mechanisms, allowing attackers to customize attacks for specific industries, organizations, or individuals. This includes tailoring ransom demands based on a victim’s financial profile, using detailed reconnaissance to exploit specific vulnerabilities, and delivering highly personalized attack vectors.
Integration of Emerging Technologies
Technologies like artificial intelligence (AI) and machine learning (ML) are expected to revolutionize RaaS capabilities. AI-powered ransomware could autonomously identify vulnerabilities, optimize payload delivery, and effectively evade detection. Similarly, deepfake technology could be used for social engineering attacks to deceive victims into granting access or paying ransom.
Evolving Extortion Tactics
Double extortion is a common tactic where attackers threaten to publish stolen data unless the ransom is paid. In the future, triple extortion may become prevalent, involving threats to disrupt third parties, customers, or suppliers associated with the victim. This could create a ripple effect, forcing organizations to comply with attackers to protect their broader network.
Expansion of RaaS into IoT and Critical Infrastructure
As the Internet of Things (IoT) grows, RaaS groups will likely target connected devices, from smart homes to industrial systems. Additionally, critical infrastructure, such as healthcare facilities and energy grids, may face increased ransomware risks due to their reliance on interconnected systems and the high stakes of operational downtime.
FAQs
In the Ransomware-as-a-Service (RaaS) model, access brokers specialize in identifying and exploiting vulnerabilities in organizations’ networks. They sell this unauthorized access to ransomware operators, allowing attackers to bypass initial intrusion stages and deploy ransomware directly. This division of labor streamlines the attack process and makes RaaS operations more efficient.
Ransomware attacks have surged due to factors like the rise of the RaaS model, which lowers entry barriers for cybercriminals, and increased digitization, which expands attack surfaces. Additionally, using cryptocurrencies facilitates anonymous ransom payments, while remote work trends expose organizations to vulnerabilities in less secure networks.


No comments were posted yet