What Is Stalkerware & How To Remove It From Your Device?

Urfa Sarmad

We live in a digital age, where executing cybercrimes and getting away with them has become ten times easier. Cybercriminals are getting smarter with time, always having new tricks up their sleeves to steal sensitive and confidential data of users without the user ever finding out. Stalkerware is no exception, and you need to be careful because if it gets installed on your device, it can monitor your location and online activities. It puts your privacy and security at risk, so you need to be able to detect it and remove it from your device immediately. If you’re unsure where to start, this guide is here to help. We’ll walk you through precisely what Stalkerware is, how to remove it, and what signs you need to look out for to detect it. So, if you’re ready, let’s begin.
Table of Contents
What Is Stalkerware & How Does It Get Installed?
So, what is Stalkerware? In 2023, 31,031 users were affected by stalkerware, an increase from 29,312 in 2022. Stalkerware is software installed on devices that let third parties sneakily track the device’s location and activities without the user’s consent or knowledge. It can monitor almost all aspects of your device’s activities, from typing to sending messages to browsing history. Stalkerware is mainly installed on smartphones and allows malicious actors to gain unauthorized access to your phone calls and camera and even take screenshots.
Stalkerware usage has been increasing at an alarming rate since 2021, when it was reported that smartphone stalkerware detections were at an all-time high, with up to a staggering 54,611 alerts having been reported. You will notice that stalkerware is mainly installed on smartphones as opposed to a laptop or PC because people take their smartphones with them everywhere they go. It also holds more valuable and personal user information than a laptop or PC.
The rise of stalkerware is becoming an ongoing issue. In a 2023 study, it was discovered that Russia, Brazil, and India were the top three countries with users who were most affected by stalkerware. However, it is a global issue. Stalkerware can be installed in many ways; however, it is mainly done when the stalker has physical access to your device. That’s why it’s essential never to leave your phone unattended, let someone borrow it, or give someone the password or PIN to your mobile device. You never know who may have malicious intentions.
Many stalkerware apps are available online and can be easily downloaded and installed. Stalkerware runs in the background without the user ever noticing or realizing they have it installed on their device until it is too late. The “stalker,” in this case, monitors the user’s activities through a website or another device. It should be noted that stalkerware is more of a threat to Android users than those with iOS devices. Since most apps on the iPhone have to be downloaded from the official App Store, it becomes challenging for someone to install malicious software. Since iOS is a closed system, the stalkers will need physical access to the iPhone by jailbreaking it and installing the software.
What Are The Common Types Of Stalkerware Apps?
Stalkerware apps are usually marketed as anti-theft or parental control apps for phones, laptops, and PCs. However, the reality is different. These get installed without the user’s knowledge or consent and don’t appear on the list of apps in the phone’s configuration, which makes them hard to detect. The Stalkerware’s capabilities depend on the type of app being used and whether it is a paid service. These are some of the common functions of stalkerware apps:
- Reading text messages and call logs.
- Tracking calendar events.
- Tracking your geolocation.
- Taking screenshots.
- Reading messages from popular social media networks, including WhatsApp, Facebook, Signal, Skype, Telegram, Gmail, Snapchat, Reddit, etc.
- Taking pictures from the front-facing camera.
Here are some common Stalkerware apps you need to be on the lookout for. These include:
1) mSpy
Although marketed as a parental control app, companies also use it to track the company’s devices. It is available on macOS, Windows, iOS, and Android and monitors text messages, call logs, and social media messages. It can also access your browsing history and emails and log your keystrokes.
2) FlexiSPY
FlexiSPY is a spyware app marketed as monitoring software. It offers extensive invasive tools, like monitoring iPhone and Android communications and everything happening on the PC or Mac. However, it is not the legitimate monitoring software it claims to be. Many security companies have FlexiSPY malware because it enables attackers to steal data and monitor devices and user activities without their knowledge.
3) Eyezy
Eyezy is a surveillance app that tracks text messages, calls, GPS, browsing history, and keystrokes. It offers extensive monitoring features but compromises the user’s privacy and can risk your online safety. Attackers can use this app to spy on your online activities and steal your data.
4) Cocospy
Cocospy is an app that monitors Android smartphones and tablets. It offers advanced features that track your child’s online activities and monitor employee activities, behavior, and performance management during working hours. However, it may be less impactful than other apps mentioned on this list, as it can manage contacts. It also has geofences to alert you if the phone goes out of bonds.
5) AndroidLost
This Android stalkerware app can read text messages and control devices remotely. This includes taking pictures, sending text messages, and forwarding calls. Developers refer to it as an anti-theft app, as it allows you to control your Android device in case it gets stolen. However, it also gives stalkers the ability to gain control of their victims’ phones and track their activities. It was removed from the Google Play Store since it was considered unsafe.
How To Identify Stalkerware On Your Device?

You need to pinpoint the exact signs that stalkerware has been installed on your device. This will allow you to take timely action and remove it before your sensitive and confidential data gets compromised. So buckle up, since in this section, we’ll explain how to detect stalkerware on iPhone and Android. Here are some of the essential signs you need to be on the lookout for:
- Your phone’s battery drains faster than usual, even when you aren’t using it and no other apps are running in the background.
You’ve noticed that your phone settings have changed, and you don’t recall ever changing them.
- You’ve noticed suspicious apps installed on your device and don’t recall ever installing them. Be cautious and remove them from your device.
- You’re noticing increased data usage, even though you use your phone normally.
- Someone has displayed unusual knowledge about you, including your location, text, and social media messages.
How To Remove Stalkerware On iOS?
Here’s how to remove stalkerware on iPhone. Follow these steps to remove stalkerware from your iOS device effectively.
1) Scan & Remove Unfamiliar Apps
One of the most effective ways to check for stalkerware on your phone is to check for unfamiliar applications on your iPhone and remove them from your device. If you’re unsure whether this app is stalkerware, you can look up it online to see if it’s stalkerware. Regardless, if you find a suspicious-looking app on your device, removing it from your iPhone is the best course of action. Here’s how you can do it:
- Touch and hold the app on the Home Screen.
- Click Remove App.
- Then click Remove From Home Screen to keep it in the App Library.
- Or click Delete App to delete it from the iPhone.
2) Look For Signs Of Jailbreaking
While it can be challenging for attackers to install stalkerware on an iPhone because of Apple’s many limitations, malicious actors can still jailbreak an iPhone and install malware. A significant sign that your iPhone has been jailbroken is that an alternative app store, instead of the official Apple App Store, is installed on your device.
3) Perform A Factory Reset
You can also factory reset your iPhone because it will completely reset your device and remove the stalkerware. However, only consider this an option if nothing else seems to work. Ensure you’ve backed up your important data and files before performing the factory reset. Here’s how you can do it:
1. Go to Settings > General and then Transfer or Reset iPhone.
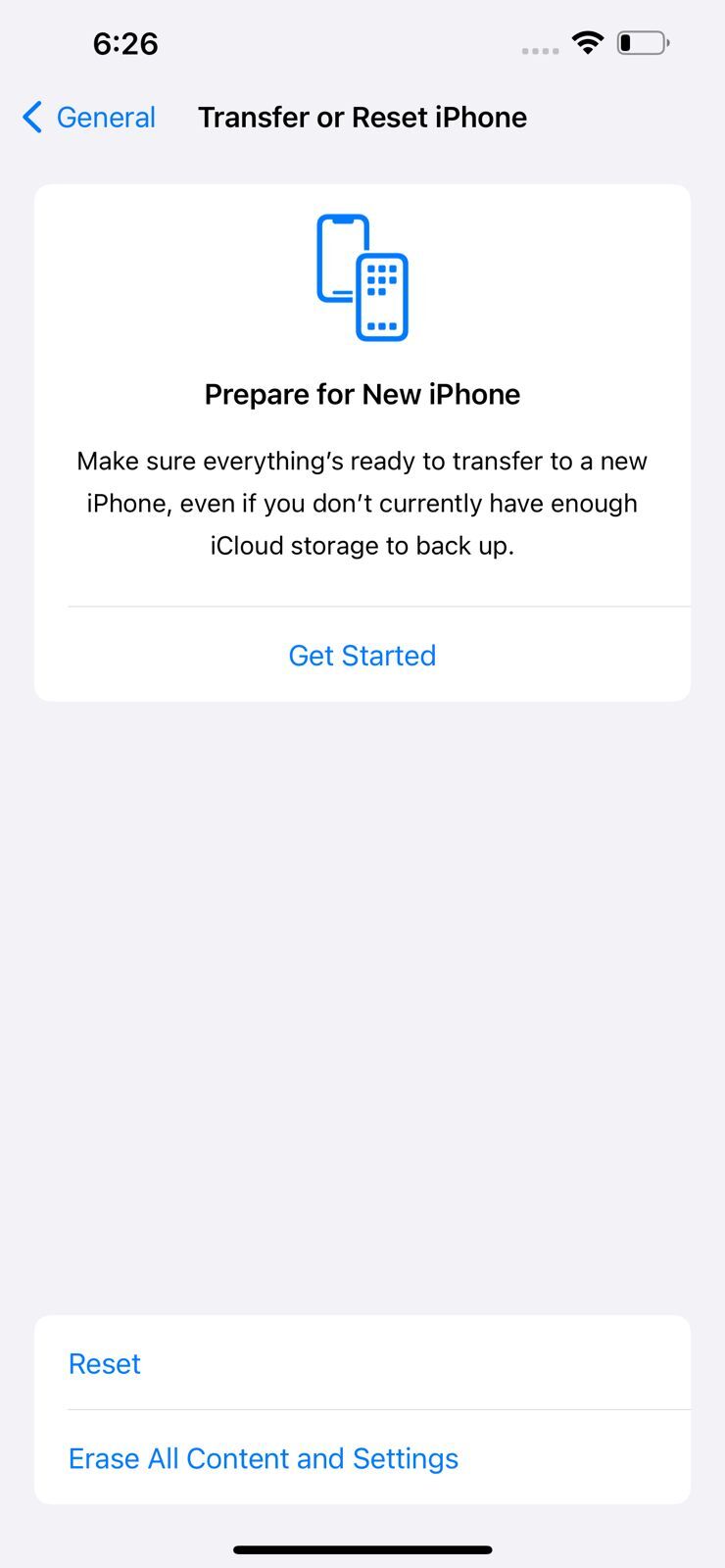
2. Then tap Erase All Content and Settings.
4) Ensure Your Device Is Updated
Ensure your iPhone is up to date with the latest security updates. This ensures that all your phone’s vulnerabilities are addressed and malicious actors cannot exploit them. Turn on automatic updates and update your iPhone to the latest version.
5) Ensure iCloud Is Locked
If your sensitive and confidential data gets compromised because of stalkerware, you should reset your iCloud password to protect your sensitive and confidential data; also, be sure to enable Two Factor Authentication for your Apple ID, making it challenging for malicious actors to access them.
How To Remove Stalkerware On Android?
Here’s how to remove stalkerware on Android. Follow these steps to remove all traces of Stalkerware from your Android device.
1) Use Google Play Protect
Google Play Protect is an essential tool for your Android device. Before you download and install any suspicious apps with stalkerware on your Android device, Google Play Protect runs a safety check on any apps downloaded from the Google Play Store before they are downloaded on your phone. It also checks your device for any harmful apps that can compromise your sensitive and confidential data. Google Play Protect can help detect stalkerware apps and remove them from your device.
2) Check If Device Administrator Is Installed
Device administrator access is given to pre-installed applications on Android devices. This access allows apps to write, transfer, or erase data from the device if it is stolen or missing. Stalkerware apps will require access to administration settings to write and transfer data from one device to another.
3) Use Reliable Antivirus Software
Use reliable antivirus software to remove emerging threats and PUPs (potentially unwanted programs from your device.) The antivirus software will scan for emerging threats in real time and immediately remove them from your device. When choosing antivirus software, make sure it can scan for malware and threats in real-time and remove them from your device, it does not impact the system’s performance when using it, it is compatible with multiple operating systems, and it is easy to use, even for someone who isn’t that tech-savvy. It also offers additional security tools.
4) Uninstall Apps You Don’t Recognize
You should manually check all of the Android apps on your device to see which ones you downloaded and which you don’t recall downloading or look suspicious. Check through the apps individually because many stalkerware apps don’t appear on smartphones’ home screens. Still, they will appear on your device’s app list, so make sure you go through that and remove anything that looks malicious or you don’t remember ever installing.
What To Do Immediately If You Find Out You’ve Been Affected With Stalkerware?
Unfortunately, you’ve been hit with stalkerware, and you fear that your sensitive and confidential data will be compromised. Here are some steps you need to take immediately to ensure that no further damage is done and that you can secure your data.
- Install AstrillVPN on your device. AstrillVPN encrypts your internet traffic and masks your IP address, ensuring that hackers and malicious actors cannot intercept your data. With its Kill Switch feature and secure protocols like StealthVPN and Wireguard, all your sensitive data remains in safe hands.
- Protect your phone using a strong and unique password. This makes it challenging for attackers to access your phone and install stalkerware. When choosing a strong password, ensure it has uppercase letters, lowercase letters, special characters, and numbers.
- Make sure you don’t share your phone password with anyone, and keep your phone safe, secure, and out of reach of anyone who can use it to install stalkerware.
- Ensure you only download apps from trusted sources, such as Google Play and the Apple App Store.
- Reach out to local support organizations that can help you combat stalkerware. The Coalition Against Stalkerware website is a great place to start and can help you find one.
- Don’t remove the stalker app or change any settings on your phone before developing a safety plan. The app can alert the attacker, which can escalate their malicious plans. Removing the stalker app can also remove essential evidence that can be used in persecution. Take some time to think of the most effective strategy that fits your current situation.
- Ensure that you also set up Multi-Factor Authentication on all your accounts. This means you will need to provide additional verification before accessing your account. This verification can be a one-time password sent to your email, phone number, or even biometric verification.
- Avoid rooting if you’re an Android user and jailbreaking if you’re using an iPhone. These actions can put the security of these operating systems at risk, making it easier for malicious actors to install stalkerware on your devices.
- Never leave your smartphones unattended, and always be mindful of who you’re giving your phone to. Physical access to your phone is the first step to ensuring that your device gets installed with stalkerware, so always be careful.
Conclusion
Having stalkerware on your device seriously risks your privacy and security. Stalkers with access to your sensitive and confidential data can use it to spy on you or carry out fraudulent activities such as identity theft or stealing your financial details. They can even have access to your actual location, which is not a good sign as this enables creepy people to stalk you and cause you harm. Luckily, this guide outlines the most effective ways to remove stalkerware from your device and the exact signs you must look for to identify and detect stalkerware on your device.
Frequently Asked Questions (FAQs)
A reliable antivirus software can easily detect stalkerware and remove it from your device. You can also look for other signs to pinpoint stalkerware and remove it from your device.
Performing a factory reset can easily remove stalkerware from your Android and iPhone. It restores the device to its original state, erasing all data and applications.
The term stalkerware was created because people started using this commercial spyware to spy on their spouse’s partners. Stalkerware has received criticism because abusers, stalkers, and employers widely use it.
If your battery drains faster than usual, your phone’s performance is lagging, and there’s a high surge of mobile data usage, these red flags point to spyware on your phone. This malicious software gets installed without your knowledge and remains hidden while stealing your sensitive and confidential data.
Spyware snoops on your online activities collects your personal and confidential data, and spreads it to third parties. They steal your sensitive data, opening doors for other cyber-attacks and identity theft.

No comments were posted yet