What is IPsec VPN, and How Does It Protect Your Online Privacy?

Arsalan Rathore

Internet Protocol Security (IPsec) VPN is one of the most robust solutions for ensuring secure, encrypted communication between devices over an IP network. For businesses, government agencies, or individual users, IPsec VPN is critical in safeguarding sensitive information from interception and tampering.
In this guide, we will explain how IPsec VPN works, its key components, its advantages, and how it compares to other VPN technologies. Nevertheless, be advised that AstrillVPN no longer offers the IPsec protocol. We offer Wireguard, which is more powerful and faster than the IPsec protocol.
IPsec is a suite of security protocols that provides authentication, integrity, and encryption for network traffic. Unlike other VPN protocols, such as SSL/TLS, which operate at the application layer, IPsec functions at the network layer. This allows it to encrypt and secure all data packets transmitted over a network, making it highly effective for site-to-site and remote-access VPNs.
Organizations use IPsec VPNs for various purposes, including:
- Secure remote access: Employees working remotely can securely connect to corporate networks.
- Site-to-site connectivity: Businesses with multiple locations can establish encrypted tunnels between their networks.
- Data privacy and security: IPsec ensures that sensitive information, such as financial transactions and confidential communications, remains protected.
- Compliance with regulations: Many industries, including healthcare and finance, require encrypted communications to comply with standards like HIPAA, GDPR, and PCI-DSS.
Table of Contents
How Does IPsec Work
IPsec secures network communication by combining encryption, authentication, and key exchange mechanisms. It operates at the OSI model’s network layer (Layer 3), which allows it to encrypt and authenticate all IP traffic, regardless of the application or protocol used.
Here’s a breakdown of how IPsec functions:
Key IPsec Components
IPsec relies on several critical components to secure network communications:
1. Authentication Header (AH)
- AH provides authentication and integrity verification for IP packets.
- It ensures that data has not been tampered with but does not offer encryption.
- It is useful in scenarios where authentication is required but encryption is unnecessary.
2. Encapsulating Security Payload (ESP)
- ESP provides encryption, authentication, and integrity protection for data packets.
- It prevents data from being intercepted or altered during transmission.
- ESP is the most commonly used component of IPsec in VPN implementations.
3. Security Associations (SA)
- SA defines the security parameters for IPsec communication, such as encryption algorithms and authentication methods.
- Each IPsec session consists of two SAs: one for inbound traffic and one for outbound traffic.
4. Internet Key Exchange (IKE)
- IKE is responsible for securely exchanging cryptographic keys between devices.
- It ensures that both parties use the same security settings before establishing an IPsec connection.
- IKE operates in two phases:
- Phase 1: Establishes a secure channel between two endpoints.
- Phase 2: Negotiates the encryption and authentication settings for the actual data transfer.
IPsec Protocol Modes of Operation
IPsec supports two primary modes:
1. Transport Mode:
- Encrypts only an IP packet’s payload (data), leaving the original IP header intact.
- It is commonly used for securing end-to-end communication between two devices.
2. Tunnel Mode:
- Encrypts the entire IP packet, including the header, and encapsulates it within a new IP packet.
- Typically used in site-to-site VPNs where data must be securely transmitted between networks.
IPsec uses a combination of encryption and authentication mechanisms to secure data:
IPsec Encryption Algorithms:
- AES (Advanced Encryption Standard): Highly secure and widely used for encrypting VPN traffic.
- 3DES (Triple Data Encryption Standard): An older encryption standard that provides moderate security.
Hashing Algorithms (for Integrity Verification):
- SHA-2 (Secure Hash Algorithm): Generating a unique hash value ensures data integrity.
- MD5 (Message Digest Algorithm 5): Less secure but still used in some legacy systems.
Authentication Methods:
- Pre-shared keys (PSK): A shared password used for authentication between VPN endpoints.
- Digital certificates: Public key infrastructure (PKI) certificates for stronger authentication.
The IPsec Process: Step-by-Step
1. Negotiation and Key Exchange (Phase 1 – IKE SA Establishment)
- The two communicating devices establish a secure channel using the IKE protocol.
- Authentication occurs using PSK or digital certificates.
- Encryption and hashing algorithms are agreed upon.
2. Establishment of Secure Communication (Phase 2 – IPsec SA Negotiation)
- The IPsec Security Association (SA) is created to define encryption and authentication parameters.
- The devices agree on how to encrypt and authenticate the data.
3. Data Transmission
- Once the IPsec tunnel is established, encrypted data packets are securely exchanged between the devices.
- Each packet is encrypted using ESP (or authenticated with AH, if applicable).
4. Tunnel Termination
- The IPsec tunnel is terminated when the communication session ends, and encryption keys are discarded.
IPsec vs. Other VPN Protocols
| Feature | IPsec | OpenVPN | L2TP/IPsec | PPTP | WireGuard |
| Security | High, AES-256, SHA for data integrity | High, customizable encryption methods | High, uses IPsec for encryption | Low, weak encryption (MPPE) | High, uses modern cryptography like Curve25519 and ChaCha20 |
| Performance | It can be slower due to encryption overhead | Slower than IPsec, uses SSL/TLS | Slower, requires 2 tunneling layers | Faster, but low security | Fast, optimized for lower latency and better performance |
| Compatibility | Widely supported on routers, firewalls, OS | Requires third-party software but is widely supported | Supported by most OS, integrates easily | Universally supported but deprecated | Supported on modern systems, but not as widely as IPsec |
| Complexity | Moderate, requires configuration of encryption, keys, and policies | High, requires configuration of SSL/TLS and certificates | Moderate, simpler than pure IPsec but more complex than PPTP | Low, simple setup, but insecure | Low, simple setup and easy configuration |
| Scalability | Highly scalable, suitable for both small and large networks | Scalable but may require additional configuration | Scalable but with overhead | Limited scalability due to weak security | Highly scalable, suitable for modern networks |
| Use Case | Site-to-site, remote access, enterprise | Client-to-site, remote access | Site-to-site, remote access | Mainly for personal use, not recommended for secure connections | Site-to-site, client-to-site, modern VPN deployments |
Why Choose Wireguard Over IPsec
Although IPsec has been used for decades, WireGuard is a newer, faster, and more efficient alternative. This is why WireGuard is often viewed as a better option than IPsec:
1. Better Performance and Speed
WireGuard is faster and more efficient because of its lightweight codebase and modern encryption methods. It reduces computational overhead, resulting in quicker speeds and lower latency, which is especially beneficial for high-traffic activities like gaming and streaming. In contrast, the complex design of IPsec often leads to slower speeds and increased latency.
2. Simpler Configuration
Setting up WireGuard is much easier than IPsec, which requires complex configurations like tunnel modes, NAT traversal, and encryption settings. WireGuard’s configuration involves simple key pairs and a straightforward setup, making it more accessible for both beginners and experienced users.
3. Modern Cryptography
WireGuard uses advanced cryptographic protocols like ChaCha20 and Curve25519, offering better security and performance than IPsec’s older AES encryption and RSA key exchange methods. WireGuard’s encryption is secure and more efficient, reducing system load.
4. Lower Latency and Faster Connection Setup
WireGuard’s simplified architecture allows for quicker connection establishment and lower latency, making it ideal for real-time applications such as video conferencing and streaming. In contrast, IPsec’s more complex setup leads to longer connection times and increased latency.
5. Cross-Platform Support
WireGuard is compatible with various platforms, including Linux, Windows, macOS, iOS, and Android, and it offers easy integration along with native applications. In comparison, IPsec can be more challenging to implement across different devices, often necessitating additional software or configuration steps.
6. Open-Source and Transparent
WireGuard’s open-source nature fosters transparency and allows for rapid updates, while community-driven development guarantees ongoing improvements. In contrast, IPsec implementations may lack active maintenance and flexibility.
How to Use AstrillVPN’s Wireguard Protocol
- Go to the AstrillVPN website and download the app for your platform (Windows, macOS, iOS, Android, etc.).
- Install the app on your device following the on-screen instructions.
- Open the app and log in using your AstrillVPN account credentials.
- In the app, tap/ click the protocols drop-down menu.
- Select WireGuard from the list of available protocols.
- Select a server location from the list of available AstrillVPN servers.
- Once you’ve selected the server and WireGuard protocol, click/ tap the power button.
- The app will establish a secure VPN connection using WireGuard.
Enjoy Secure and Fast Browsing with AstrillVPN
Signup NowTypes of IPsec VPNs
IPsec VPNs can be categorized into two primary modes based on how they encrypt and transport data: Tunnel Mode and Transport Mode. These modes define how the data is encapsulated, encrypted, and transmitted across the network.
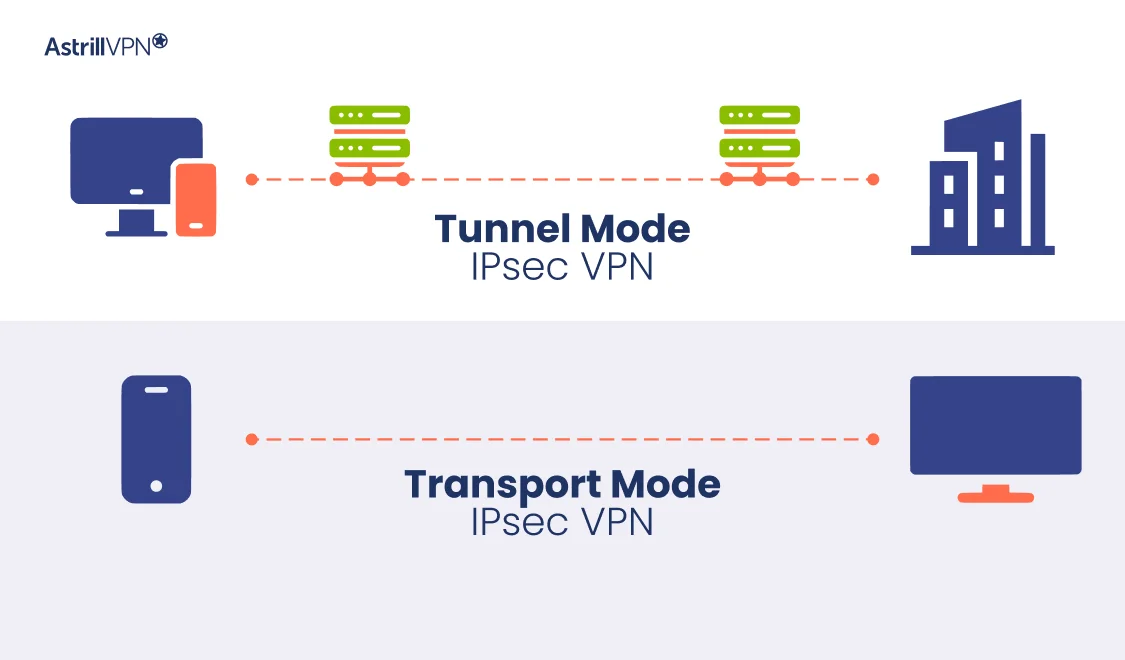
1. Tunnel Mode IPsec VPN
In Tunnel Mode, the entire IP packet (including the header and payload) is encrypted and encapsulated within a new IP packet. This mode is most commonly used for site-to-site VPNs, where the communication between two gateways, such as routers or firewalls, requires secure transmission over an untrusted network, typically the Internet.
- Encapsulation: The original IP packet is encapsulated within a new outer packet that is then encrypted. The original IP header is hidden, and only the encrypted payload is transmitted across the network.
- Encryption: The entire packet, including the original IP header, is encrypted, ensuring confidentiality and integrity during transit.
- Routing: The outer IP header, which is part of the encapsulated packet, contains the routing information necessary for the packet to be forwarded across the network, and this header is encrypted to prevent interception.
2. Transport Mode IPsec VPN
In Transport Mode, only the IP packet’s payload (the actual data) is encrypted, while the original IP header remains intact. This mode is commonly used in end-to-end communications, where two devices like hosts or servers must securely exchange data directly.
- Encapsulation: The original IP packet is not fully encapsulated; only the payload, or the data section, is encrypted. The original IP header remains unmodified and visible, including source and destination information.
- Encryption: Only the data (payload) of the IP packet is encrypted, which means that the routing information (contained in the header) is still visible during transmission.
- Routing: Since the original IP header is preserved, the packet can be routed by intermediate devices (such as routers) without decrypting the header. This model is efficient for direct communication between devices within a secure network.
Advantages and Disadvantages of IPsec VPNs
| Aspect | Advantages | Disadvantages |
| Security | High security with AES-256, SHA, and IPsec protocols | Configuration complexity can lead to security flaws if misconfigured |
| Support | Widely supported across routers, firewalls, and OS | Can require vendor-specific configurations, leading to lock-in |
| Performance | Strong performance with hardware acceleration | Encryption and tunneling can cause overhead, reducing speed |
| Compatibility | Supports a variety of devices and platforms | Can have issues with NAT (Network Address Translation), requiring extra setup |
| Flexibility | Supports both tunnel and transport modes for various use cases | More rigid compared to newer protocols like WireGuard |
| Scalability | Highly scalable, good for both small and large networks | More resource-intensive and complex setup for large deployments |
| Ease of Configuration | Can integrate easily with existing network infrastructure | Configuration can be complex, especially with advanced features |
| Efficiency | Offers a secure method of data transmission | Not as efficient as lightweight protocols like WireGuard |
Conclusion
IPsec is one of the most secure and reliable VPN protocols, providing robust encryption and privacy for users. By setting up AstrillVPN with IPsec, you can protect your internet connection against various online threats, including hackers, snoopers, and data breaches. Whether you’re using a desktop mobile device or even setting up a router, the process is straightforward and offers the peace of mind that comes with secure online activity.
With its widespread support across devices and platforms and its ability to work seamlessly with AstrillVPN, IPsec is an excellent choice for anyone looking to enhance their privacy and security online. By following the easy-to-understand steps in this guide, you’ll be ready to leverage the full power of IPsec and AstrillVPN for a safer and more private online experience.


No comments were posted yet