What is DDoS Blackhole Routing? How Does it Work?

Bisma Farrukh
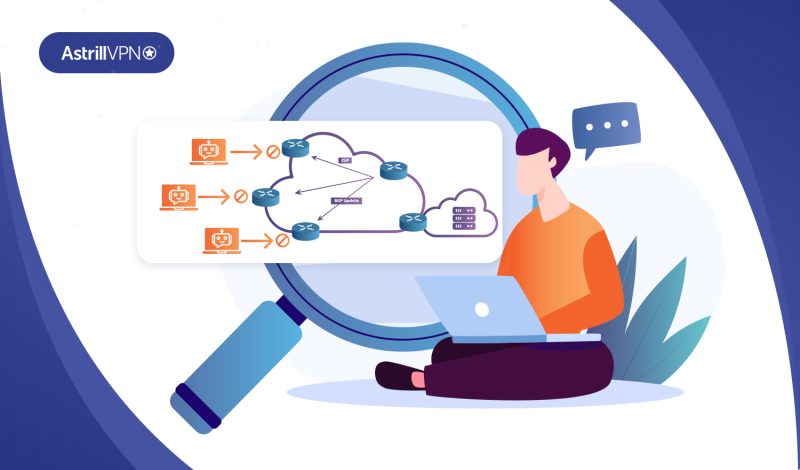
Blackhole routing is a type of internet routing that can both benefit and hurt an ISP’s network. The term derives from a 1979 film. A black hole route is a place where things aren’t able to escape, and it has negative connotations in IP routing.
Nevertheless, DDoS blackhole routing can be a helpful solution when it comes to blocking malicious traffic.It can be applied to a single router or an entire network of routers. You can refer to the term “internet blackhole” that’s why it’s giving negative vibes, and no traffic should be directed into it. Read on to learn more about this and how it works.
Table of Contents
What is a DDoS attack?
DDoS attack is a type of cyberattack in which a large amount of data is sent to a target network. A DDoS attack may be performed by multiple machines and can overwhelm a system. Some common forms of DDoS attacks are SYN floods and IP fragmentation attacks.
Network administrators need to know how to identify a DDoS attack. They need to monitor network traffic and note the IP addresses of suspicious traffic and the channels from which the traffic originates. They also need to be aware of what kind of devices are viewing their websites. If they notice any unusual traffic patterns, such as high-volume requests from a single IP address or unusual location, then it is likely that a DDoS attack is underway.
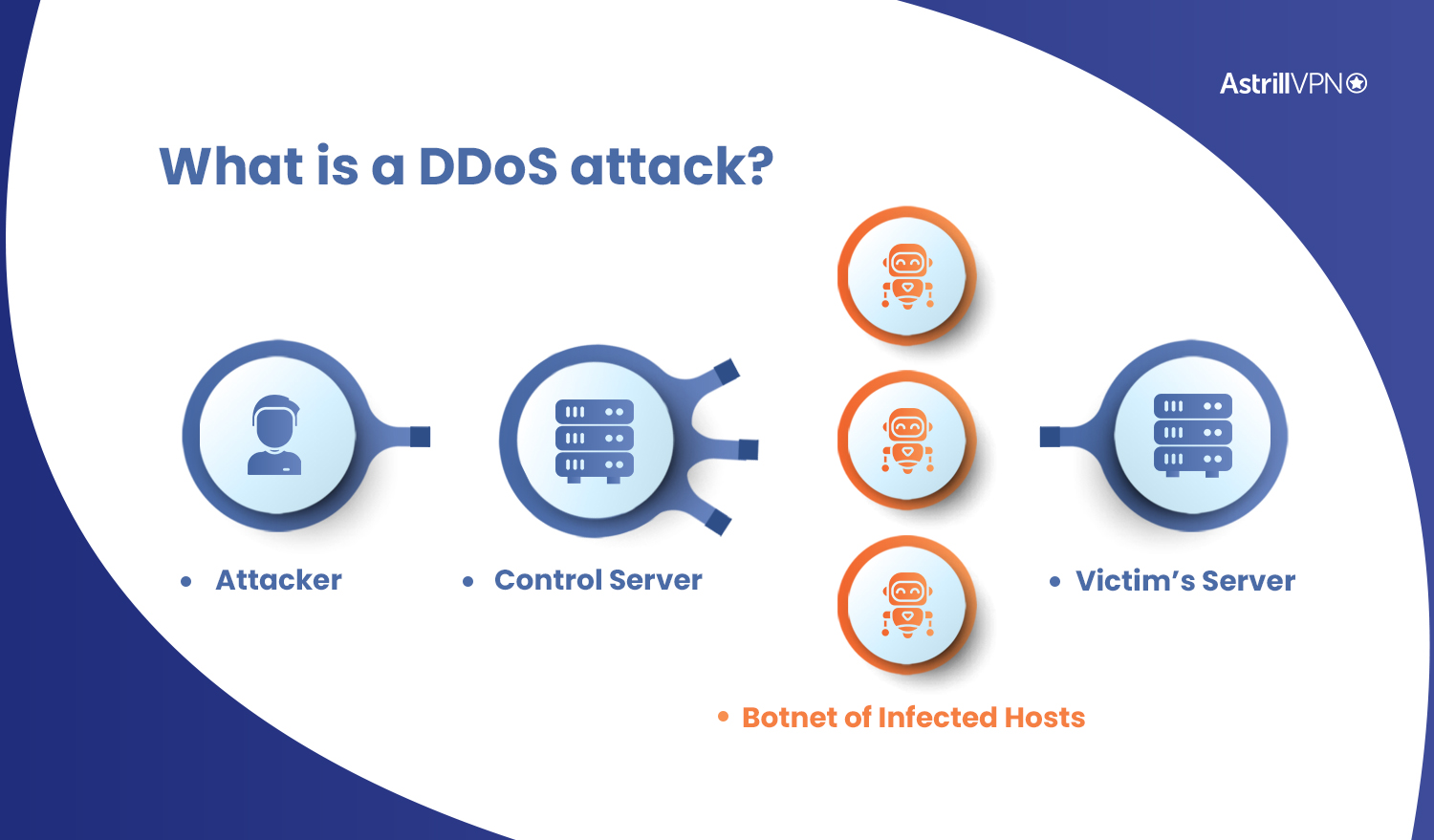
A DDoS attack can be harmful for an organization, especially if it affects vital business processes. These cyberattacks can slow down a company’s website or make a web application unavailable. The attacks use a network vulnerability to flood a system with large amounts of internet traffic. DDoS attacks are not easy to detect, so it is important to be proactive. The only way to combat a DDoS attack is to measure the damage it causes and take steps to protect your network. Fortunately, cloud-based tools are now available to measure the amount of damage caused by a DDoS attack.
What is DDoS blackhole routing?
DDoS blackhole routing is a rudimentary approach to DDoS mitigation. It is designed to drop undesirable traffic into the blackhole before it reaches the protected network. It can also be configured to protect a particular network segment from DDoS.
This method is used by many ISPs to protect their networks from DDoS attacks. It blocks attackers from sending traffic to the target network or service, which knocks down hundreds of other customers. It can be effective but only when performed correctly. Therefore, it is crucial to consult an experienced network engineer before implementing this solution.
Why Blackhole routing/filtering is used?
Blackhole routing and filtering can be configured to block IP addresses that are frequently used for spam. To prevent spam, receiving mail servers will reject messages from these IP addresses. RBLs are DNS-based lists that keep lists of IP addresses that send spam. Each block list has different criteria for listing IP addresses as spam.
DDoS attacks can affect the entire network, causing significant damage. Fortunately, there are several effective solutions to prevent these attacks. One such approach is BGP Blackhole routing. By directing unwanted traffic to a specific interface, BGP blackholes can be configured to block traffic from a specific source. Blackhole routing is effective against DDoS attacks.
How does blackhole routing work?
Blackhole routing is a tool that is used to block unwanted traffic. The basic principle behind blackhole routing is simple: IP packets destined for a destination address will be discarded. When a network is subject to attacks, blackhole routes are particularly useful. They will discard IP packets that are destined for a particular address until the network can regain connectivity.
It works by using a router’s forwarding power and performance to block packets that are bound for blacklisted sites. It is less expensive than ACL but requires more processing power. While blackhole routing is not perfect, it is an excellent solution for certain scenarios.
To implement blackhole routing, your service provider must have BGP peering with you, and you’ll need to configure static routes to a specific destination address. Then, your router must declare a matching prefix to the BGP community, which then triggers blackholing.
What is a blackhole routing attack?
A blackhole routing attack is a type of attack in which a malicious node intentionally misconfigures its router to offer a zero-cost route to every destination. When this occurs, every other router in the network will be unable to detect the failure and therefore will not be able to relay traffic. As the router is overwhelmed with messages, it will eventually fail, causing the network to collapse.
How can blackhole routing help you?
Blackhole routing/filtering helps you by allowing you to redirect malicious traffic to a specific route. This allows your network to be more secure and can also improve performance. This method has a negative connotation, but it can be beneficial for your network.
Blackhole routing can be done from two angles. Both of them are beneficial. One approach uses a trigger router, which advertises blackholed routes that go to the target IP address. The other method involves setting a permanent static route pointing to a null interface on the PE routers. This process is done from a trigger machine, which is part of the ISP’s infrastructure and has established internal BGP sessions with each PE router.
To prevent DDoS attacks, a network administrator must complete a risk assessment. A risk assessment includes testing a network’s setup and identifying vulnerabilities. Then, they can take corrective measures. Once the network has been assessed, blackhole routing can be used. In this method, the network admin produces a black hole route, which will remove traffic from the network. This process clears the network of unwanted DDoS traffic, but may cause legitimate traffic to be blocked.
How can DDOS blackhole routing harm you?
Although this method is effective in preventing DDoS attacks, there are side effects that you should know about.
When a website is under attack, it can be difficult to detect the source. The traditional methods of defense include SYN-cookies, proxies, redirects, and challenges. However, the more advanced techniques like blackhole routing can help protect your network from DDOS attacks. Moreover, this type of routing is effective against DDOS attacks because it affects websites that share the same routers and servers. If one website is attacked, it will negatively affect all other websites in the same domain.
In a DDoS attack, the attacker will make your web server unavailable. To mitigate this, you should first block any communication with that IP address using IPTables Rules or blackhole routing. Once the attack has stopped, you should be able to restore normal internet connectivity.
Blackhole IP addresses are often invisible to the source of traffic. This means that incoming and outgoing traffic is silently dropped, and the source cannot be identified. In addition, blackholes can’t be directly observed, which makes it difficult to detect their existence. The most common blackhole is an IP address. If you want to access a secure IP address then you should use a trusted VPN service. Astrill VPN is one of the most popular and trusted VPN having servers in more than 55 countries around the world.
How DDoS Blackhole Routing Differs from Traditional Routing
DDoS Blackhole Routing is a critical innovation in cybersecurity, particularly for combating Distributed Denial of Service (DDoS) attacks. Unlike traditional routing methods, which prioritize efficiently delivering data packets to their intended destinations, DDoS Blackhole Routing takes a proactive and defensive approach to deal with malicious traffic.
In traditional routing, packets are forwarded based on destination addresses, utilizing protocols like OSPF (Open Shortest Path First) or BGP (Border Gateway Protocol). The primary goal is to ensure the most efficient and reliable data transmission across networks. However, traditional routing mechanisms often prove inadequate to mitigate excessive traffic flooding when a network comes under a DDoS attack.
This is where DDoS Blackhole Routing steps in. Instead of directing the incoming traffic to its intended destination, it is diverted to a ‘blackhole’ – a null route leading to a non-existent or unused IP address. In simpler terms, malicious traffic is isolated and dropped, preventing it from overwhelming the targeted network. This divergence from the norm allows network administrators to contain the impact of a DDoS attack by mitigating its effects on legitimate traffic flow.
Implementation of DDoS Blackhole Routing
BGP (Border Gateway Protocol) Manipulation
The Border Gateway Protocol (BGP) is the backbone of internet routing. It allows autonomous systems (ASes) to exchange routing information to determine the optimal paths for data to travel between networks. In the context of DDoS Blackhole Routing, BGP manipulation plays a pivotal role.
Strategic Alteration of BGP Announcements
Network administrators collaborate with ISPs to modify BGP route announcements when a DDoS attack is detected or imminent. By announcing a more specific route for the target IP addresses that points to a null route (blackhole), routers across the internet are instructed to send traffic destined for those addresses to the blackhole. This rerouting prevents the malicious traffic from reaching the target, mitigating the attack’s impact.
Null Routing vs. Blackhole Routing
Null Routing
Null routing is a related technique that directs traffic destined for a specific IP address to a null interface, effectively discarding the packets. While straightforward, null routing can inadvertently block legitimate traffic if not configured accurately. This might lead to unintended service disruptions.
Blackhole Routing’s Strategic Isolation
Blackhole routing takes null routing a step further by routing malicious traffic not to a null interface but to a non-existent IP address—an IP that does not correspond to any real device. This isolation ensures that the malicious traffic is definitively dropped without causing potential collateral damage to legitimate traffic.
Anycast Networks and Load Distribution
Distributing Traffic Across Multiple Points
Anycast is a networking technique that involves routing data packets to the nearest server or router in a group of potential destinations. In the context of DDoS Blackhole Routing, anycast networks can be employed to distribute incoming traffic across multiple points of entry.
Reducing Congestion and Enhancing Resilience
By distributing traffic across various nodes, anycast networks help mitigate the risk of congestion at a single entry point. This improves the network’s capacity to handle increased traffic loads during DDoS attacks and enhances overall network resilience.
Collaborative Configuration with ISPs
Implementing anycast for DDoS Blackhole Routing requires close coordination with ISPs to ensure traffic is correctly routed to the most suitable node. It’s important to consider factors like network latency and geographical proximity for effective anycast deployment.
Challenges and Limitations in DDoS Blackhole Routing
False Positives and Negatives
One of the primary challenges in DDoS Blackhole Routing is the potential for false positives and negatives. False positives occur when legitimate traffic is inaccurately identified as malicious and redirected to the black hole. This can result in service disruptions for legitimate users, leading to frustration and business implications.
Impact on Legitimate Traffic
While effective in diverting malicious traffic, DDoS Blackhole Routing can inadvertently impact legitimate traffic. The indiscriminate nature of rerouting traffic to a black hole can lead to service disruptions for users trying to access legitimate resources hosted on the same network.
Evolving DDoS Attack Techniques
As DDoS mitigation techniques advance, so do the tactics employed by attackers. Attackers constantly innovate to circumvent existing defenses, making it a challenge for DDoS Blackhole Routing to remain foolproof against all forms of attack.
Attackers are leveraging botnets, amplification attacks, and even exploiting vulnerabilities in Internet of Things (IoT) devices to generate massive traffic volumes. These techniques often involve traffic resembling legitimate data, making it challenging to discern malicious from benign traffic.
Is blackhole routing a concern for an ISP?
Blackhole routing can be implemented easily and is used by many ISPs to protect their network from DDoS attacks. Unlike other forms of network security, blackhole routing prevents traffic from traveling through a certain network and drops it at the destination. Currently, the blackhole routing approach is used to combat saturation of networks caused by DDoS attacks.
Blackhole routing can be a valuable security tool for an ISP, but there are some downsides to remote-triggered blackhole filtering. One major drawback is that it limits the ability to receive traffic from customers. It can also cause collateral damage to adjacent customers, forcing the ISP to respond with remote-triggered black hole filtering, which blocks traffic from reaching the customer’s network.
Conclusion
Although blackholing is a cheap and scalable mitigation method, it suffers from some major drawbacks. First, it drops all traffic that would normally go to the target site, including legitimate traffic. Additionally, it suffers from high signaling complexity, which limits its effectiveness.
Another network layer protection method is Access Control Lists (ACLs). These are distributed to individual nodes. They are effective against DDoS attacks. They can be deployed at the edge of an ISP’s network. However, ACLs can have issues with scalability, especially at low packet inspection speeds.

No comments were posted yet