What is an Open Proxy? How It Affects Your Privacy and Security

Arsalan Rathore

Have you ever wondered why your IP address might get flagged as an open proxy? It’s frustrating and can impact your privacy, security, and online activities. An open proxy could make your connection vulnerable, allowing anyone to route traffic through your server, often without you even realizing it. In this guide, we’ll explain what an open proxy is, why your IP might get flagged, the risks involved, and how to fix it.
Table of Contents
What is Open Proxy?
An open proxy is a server that acts as an intermediary between a user’s device and the internet, allowing users to access the web indirectly by routing their traffic through the proxy server. Unlike private proxies that require authentication or are restricted to specific users, open proxies are accessible to anyone without credentials. This unrestricted nature makes them attractive to users seeking anonymity, bypassing censorship, or accessing geo-restricted content.
Open proxies work by receiving user requests, forwarding them to the target web server, and then returning the server’s response to the user. Because the user’s actual IP address is hidden, their online activities appear to originate from the proxy server’s IP. While this can provide a degree of anonymity, it also opens the door to several risks.
Typically, open proxies are operated without robust security measures, making them unreliable and, in some cases, unsafe. These servers are often exploited for malicious purposes, such as distributing spam or conducting cyberattacks, and their usage can expose users to significant privacy and security threats.
Advantages of an Open Proxy
Open proxies offer several appealing benefits, especially for users seeking to navigate the internet with fewer restrictions. Here are the key advantages:
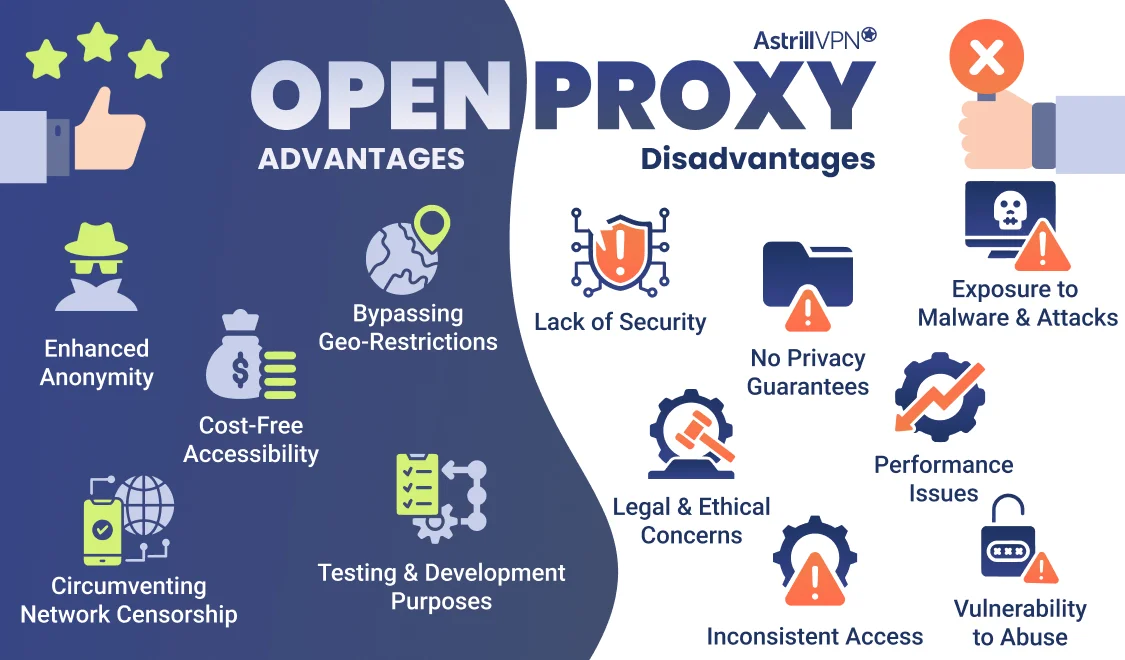
Enhanced Anonymity
Open proxies hide the user’s IP address by substituting it with the server’s IP. This allows users to browse the web anonymously, reducing the risk of being tracked by websites or advertisers.
Bypassing Geo-Restrictions
These proxies enable users to access content that might be restricted in their region by making it appear that their traffic originates from the proxy server’s location. This can be useful for accessing streaming platforms, websites, or services unavailable in certain countries.
Cost-Free Accessibility
Since open proxies are typically free, they are a cost-effective option for users seeking anonymity or bypassing restrictions without investing in paid solutions like VPNs.
Testing and Development Purposes
Web developers and researchers often use open proxies to test the accessibility of websites from different regions or to gather data for analysis.
Circumventing Network Censorship
In regions with strict internet censorship, open proxies serve as a tool to bypass network firewalls and access restricted websites or content.
Disadvantages of an Open Proxy?
Despite their advantages, open proxies come with numerous risks and limitations that make them less desirable for users concerned about privacy, security, and reliability. Below are the primary disadvantages:
Lack of Security
Open proxies rarely implement encryption or other security protocols to protect user data. This makes any information transmitted through them, such as login credentials or personal data, vulnerable to interception by hackers or malicious actors.
Exposure to Malware and Attacks
Untrustworthy entities operate many open proxies or are deliberately set up to harvest user data. They may inject malware or spyware into your system, exposing your device to cyberattacks.
Performance Issues
Due to high traffic loads or inadequate infrastructure, open proxies often experience slow speeds and poor reliability. This can result in frequent disconnections and a subpar browsing experience.
No Privacy Guarantees
While open proxies hide the user’s IP address, they do not offer the comprehensive privacy protections of a VPN. Moreover, some open proxies log user activities, which can lead to data breaches or tracking by third parties.
Legal and Ethical Concerns
Using open proxies to bypass restrictions or access copyrighted material may violate laws or terms of service agreements. This could result in legal consequences or account bans.
Vulnerability to Abuse
Malicious users often exploit open proxies for spamming, launching distributed denial-of-service (DDoS) attacks, or conducting fraudulent transactions. This can result in the proxy server being blacklisted, rendering it unusable for legitimate users.
Inconsistent Access
Due to their public nature, open proxies are frequently blocked by websites and services, limiting their effectiveness for accessing content.
Open Proxy vs Closed Proxy
| Feature | Open Proxy | Closed Proxy |
| Accessibility | Publicly accessible to anyone without authentication. | Restricted access; requires authentication. |
| Security | Low security; vulnerable to data interception and cyber threats. | High security; better protection against threats. |
| Reliability | Often unreliable due to heavy traffic and lack of maintenance. | Reliable with consistent performance. |
| Performance | Slow speeds and frequent downtime. | Optimized for faster speeds and stability. |
| Privacy | Limited privacy; some may log user activity. | Better privacy; user activity is typically protected. |
| Cost | Free to use in most cases. | Paid services with premium features. |
| Use Cases | Suitable for occasional and non-sensitive tasks like bypassing geo-restrictions. | Ideal for sensitive tasks like business operations or secure browsing. |
| Risk of Abuse | High; often exploited for malicious activities. | Low; controlled access prevents misuse. |
| Ease of Use | Easy to access without setup or registration. | Requires setup and authentication. |
| Target Audience | Casual users or developers needing temporary solutions. | Businesses or individuals prioritizing security and performance. |
How to Detect an Open Proxy
Detecting an open proxy involves analyzing its characteristics and behavior. The following methods can help you identify if a proxy is open:
1. Test for Authentication Requirements
One of the easiest ways to identify an open proxy is by checking if it requires authentication. Open proxies typically allow unrestricted access without asking for credentials.
Configure your device or browser with the proxy’s IP address and port to test this. Attempt to visit a website. The proxy is open if you can connect without entering a username or password.
2. Check Proxy Listings
Public proxy lists are a reliable resource for identifying open proxies. Websites like Free Proxy Lists and ProxyScan regularly update databases of open proxies, detailing their IP addresses, ports, and locations.
You can cross-reference these lists with the proxy you’re analyzing. You can confirm its status if it’s listed as an open proxy.
3. Analyze Proxy Behavior with Testing Tools
Proxy testing tools like Proxy Checker or ProxyScrape allow you to examine a proxy’s accessibility and functionality. They can also verify whether the proxy allows unrestricted connections.
Simply input the proxy’s IP address and port into the tool, and review the results. Open proxies generally accept connections without additional validation.
4. Scan for Common Proxy Ports
Open proxies often operate on well-known ports such as 8080, 3128, or 80. Using port scanning tools like Nmap, you can identify whether these ports are open and actively accepting connections.
Scanning the proxy’s IP address lets you determine if it’s configured as an open proxy.
5. Inpect Traffic and Anonymity
Open proxies often behave like transparent proxies, meaning they don’t hide the user’s original IP address. You can verify this by using the proxy to access an IP-checker. If your original IP is visible instead of the proxy’s, it’s likely an open proxy with low anonymity.
6. Examine HTTP Headers
HTTP headers can reveal whether a proxy is open. When you connect through a proxy, it may insert specific headers like X-Forwarded-For or Via into the traffic. Tools like Wireshark or Burp Suite can inspect these headers and confirm whether the proxy is open and transparent.
7. Analyze Network Logs
Analyzing the network traffic logs of a proxy can provide clues about its openness. Open proxies generally do not restrict incoming requests and respond indiscriminately. Logs can reveal patterns of unrestricted access that are characteristic of open proxies.
8. Check Geographic Location
Sometimes, an open proxy’s geographic location can indicate its accessibility. Open proxies often come from countries with lax regulations on internet usage or servers operated by anonymous entities. Services like MaxMind GeoIP can help determine the location of a proxy server.
How to Turn Off an Open Proxy
If you’ve discovered an open proxy on your system, it’s essential to turn it off or secure it to protect your network. Here are the steps to either disable or secure an open proxy:
1. Disable the Proxy in Device Settings
To quickly stop the proxy from working, disable it directly in your device’s settings. Here’s how you can do that:
On Windows:
- Open the Control Panel and go to Internet Options.
- Click on the Connections tab, then LAN Settings.
- Uncheck the box that says Use a proxy server for your LAN.
On macOS:
- Go to System Preferences, then select Network.
- Choose your active connection, click Advanced, and go to the Proxies tab.
- Uncheck any enabled proxy settings.
2. Turn Off the Proxy Service on the Server
If the open proxy is running on a server, you’ll need to disable the service on the server itself:
On Linux/Unix (e.g., Squid Proxy):
To stop the proxy service, run:
sudo systemctl stop squid.service
sudo systemctl disable squid.service
On Windows Server:
- Open the Services app (type services.msc in the Run dialog).
- Find the proxy service (e.g., Squid, Microsoft Web Proxy) and click Stop.
- Right-click on the service, choose Properties, then set the Startup type to Disabled.
3. Secure the Proxy with Authentication
If you don’t want to disable the proxy completely, consider securing it by requiring a username and password. This prevents unauthorized access.
For Squid Proxy (Linux):
- Edit the Squid configuration file (/etc/squid/squid.conf) to add authentication settings.
- Set up a user/password file to control access.
- Restart Squid using the command:
sudo systemctl restart squid
For Windows Proxy:
Enable authentication (e.g., set up usernames and passwords) in your proxy software settings to restrict access.
4. Block Proxy Ports with a Firewall
You can also block the ports used by open proxies to prevent them from functioning:
On Linux (using iptables):
Block common proxy ports (like 8080 or 3128) with this command:
sudo iptables -A INPUT -p tcp –dport 8080 -j DROP
sudo iptables -A INPUT -p tcp –dport 3128 -j DROP
On Windows (using Windows Firewall):
- Open Windows Defender Firewall and click on Advanced Settings.
- Create a new Inbound Rule to block ports like 8080 or 3128.
5. Consider Using a VPN for Added Security
After turning off or securing an open proxy, it’s crucial to replace it with a more secure solution like a VPN (Virtual Private Network). Unlike open proxies, which expose your online activity to data interception and tracking risks, a VPN encrypts your internet connection, ensuring your data remains private and secure. A VPN also masks your real IP address, providing anonymity and preventing websites or third parties from tracking your online activities. Furthermore, VPNs offer robust protection on public networks, such as Wi-Fi in cafes or airports, where open proxies are vulnerable to hacking.
Using a VPN like AstrillVPN keeps your browsing safe and offers additional benefits, such as the ability to access geo-restricted content and secure online transactions. With AES 256-bit encryption and a no-logs policy, a reliable VPN service protects your data from malicious actors. Using a VPN allows you to enjoy a secure, private browsing experience without the risks associated with open proxies.
Why is Your IP Address Flagged as an Open Proxy?
Your IP address can be flagged as an open proxy for various reasons, typically related to misconfigurations or intentional actions that allow others to use your server or network as a proxy without proper security. Here’s why this might happen:
1. Misconfigured Proxy Server
If you run a proxy server, it could be unintentionally configured to allow open access to external users. This is one of the most common reasons for an IP address being flagged. An open proxy allows anyone to route their traffic through your server, which makes it visible to third-party organizations that monitor proxy servers. If you don’t authenticate your proxy or limit access, it can be exploited by others, resulting in your IP being flagged.
2. Lack of Access Control
With no access restrictions (such as firewalls or authentication protocols), your server becomes an open gateway for anyone looking to anonymize their traffic. Attackers or malicious users may utilize your server for activities like web scraping, illegal activities, or launching DDoS attacks, which can lead to your IP being flagged by security services or websites that monitor proxies.
3. Unintentional Proxy Exposure
Sometimes, your IP address could be flagged as an open proxy without your knowledge if your computer or network has been infected with malware. Malicious software can turn your device into a proxy server and use it to route illicit traffic. If this occurs, websites or security services that track open proxies may identify your IP address and flag it as vulnerable or being used for malicious activities.
4. Publicly Accessible Proxy Listings
Some open proxies are deliberately listed on proxy directories or services, which are databases used by various entities to identify proxy servers. If your proxy is listed in these directories without your consent or knowledge, it will inevitably get flagged as an open proxy, damaging your reputation online.
5. Proxy Misuse by External Parties
In some cases, attackers may intentionally abuse your open proxy for their purposes, such as conducting cyberattacks, spamming, or hiding their identity while performing malicious actions. When these activities are detected, your IP address is flagged and blacklisted by security organizations, making it harder for you to access certain websites or services.


No comments were posted yet