What Is a Data Security Breach and How to protect against it?

Urfa Sarmad

A data or security breach occurs when private, sensitive, and confidential data is exposed to unauthorized personnel. Cybercriminals find a way to get past the security measures to steal your sensitive and confidential data for identity theft, fraud, and other malicious intent. Security breaches can have severe ramifications for companies and individuals. There are many reasons why security breaches happen; however, once your sensitive data gets into the wrong hands, it’s game over. However, you need not worry because, in this guide, we will ease your worries and cover everything, from why a security breach happens, their different types, some well-known cases of security breaches, and what steps you can take to prevent them. So, if you’re ready, let’s begin.
Table of Contents
Did You Know?
- According to latest report: A data breach costs an average of $4.44 million globally, though this represents a 9% decrease from 2024’s all-time high of $4.88 million.
- 2024 saw over 3,200 data breaches globally, affecting more than 1.7 billion individuals. In the first half of 2025 alone, 1,732 data compromises were reported. Source: SecureFrame
- 67% of companies agreed to the fact that they may be susceptible to Insider Threats.
The cybersecurity skills shortage continues to be a critical factor that increases breach costs by $173,400 on average per incident
How Are Security Breaches Caused?
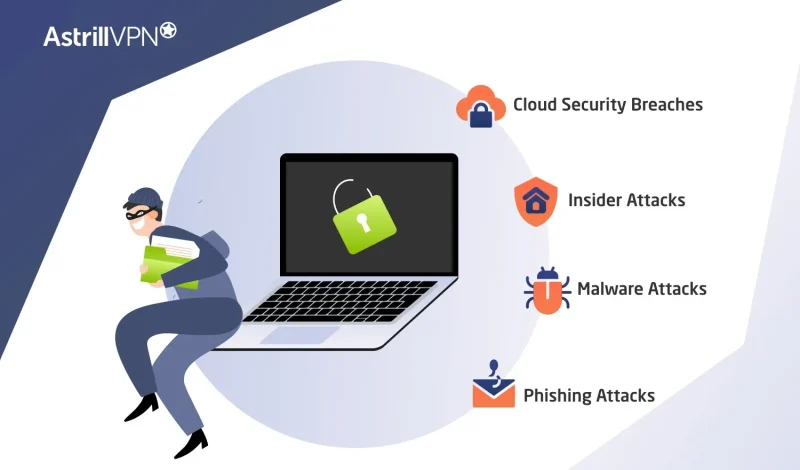
Although organizations can take multiple steps to enhance their security, you may wonder how data breaches happen in this case. Data or Information breaches usually occur because of an outside person or someone within the organization, with malicious actors and hackers targeting specific individuals with targeted cyber attacks. Here are some of the significant causes of security breaches:
1) Cloud Security Breaches
Cloud-based services have become the norm in this day and age, and the more cloud-based services and remote devices are used to gain access to your network, the fewer barriers to entry for hackers and cybercriminals to gain unauthorized access to your sensitive and confidential information. In a 2021 Survey by Gartner, it was reported that around 64% of employees were working from home, meaning more remote access and making it easier for malicious actors to infiltrate your network.
Remote work has become the new normal since the pandemic, and remote jobs and culture will not disappear anytime soon. Unfortunately, this makes it easier for malicious actors to access your devices illegally. Just because it’s risky doesn’t mean that companies shouldn’t implement cloud computing. It is the future, after all. However, they must effectively secure their cloud-native applications and data.
2) Insider Attacks
An Insider attack occurs when the security breach is caused by an employee revealing the company’s sensitive data to a third party. These individuals deliberately give away the company’s data to third parties. For example, these people may have a list of the company’s clients and their financial details, which they may have kept as leverage and sold to third parties. These people may also have valuable information about the higher-ups in the organization, and they are selling it to hackers and malicious actors to make a profit.
3) Malware Attacks
Data breaches can also result from Malware attacks. Malicious actors inject malware to steal your sensitive and confidential information. Some hackers encrypt the user’s data and demand payment from the user or the company to decrypt all the data. This is also referred to as a ransomware attack. Spyware and adware can also be injected into your online activities to snoop and steal sensitive and confidential information. They collect data on users without their knowledge.
4) Phishing Attacks
Phishing attacks are another common cause of data breaches. This can be seen as getting deceptive emails where the user pretends to be an authority figure in the company or someone else the employee trusts. They pretend to be a specific person in the company and then trick vulnerable employees into divulging sensitive and confidential information by clicking suspicious links and attachments. The damage is done once the employees click on them, and their data gets compromised because there’s malware in the system.
What Are The Different Types Of Security Breaches?
There are different types of security breaches that you need to be aware of, with the most common ones being:
- Malware attacks, such as malicious software and viruses, can replicate and spread to other systems, causing damage and stealing sensitive and confidential data.
- Phishing attacks are deceptive emails sent to employees to trick them into divulging sensitive information about the company.
- Credential theft involves unauthorized access gained through dictionary attacks, brute force, and credential stuffing. It also includes keyloggers that capture sensitive information, such as passwords.
- Man In The Middle Attacks intercept and monitor communications between the two parties without their knowledge or consent.
- DDoS (Distributed Denial of Service) attacks that overwhelm a system with unnecessary traffic to make it unavailable for legitimate users.
- Social engineering tactics involve creating fake scenarios to persuade someone to reveal sensitive and confidential information.
- Physical breaches, like stolen laptops, smartphones, and other devices, contain sensitive and confidential information.
- Zero-day exploits occur when malicious actors exploit unknown vulnerabilities before they can be patched. In addition, malicious actors take advantage of and exploit vulnerabilities in unpatched software.
Prominent and Massive Data Security Breaches
Here are some information security breaches that struck some of the biggest companies in recent years:
AT&T Data Breach
The U.S. Phone giant confirmed earlier this month that it will notify its millions of users about the latest data breach, which will enable cybercriminals to steal the phone records of nearly all of its customers. In a statement, AT&T stated that the stolen data contains the phone numbers of mobile and landline customers, as well as their calls and records from May 1st, 2022, and October 31st, 2022.
Some of these stolen records also include cell site identification numbers associated with calls and text messages, which can be used to determine the exact location of where a call was made or where the text message was sent. AT&T stated that it would notify over 100 million customers about the data breach and published a website with information for customers regarding the data breach.
Disney Data Breach
Disney also suffered a significant data breach this year, with its internal Slack channels hacked. A hacker group called Nullbulge claimed to have obtained and leaked more than one terabyte of data from Disney’s internal Slack channels. All this data was illegally obtained through cookie hacking. The hacktivist group shared screenshots of the documents and posted details about the traffic and revenue data for Disneyland Paris. The hacking group’s latest blog post claimed that the full scope of leaked data includes details about unreleased projects, computer code, and raw images. Disney is still investigating this entire issue.
Other Well-Known Cases Of Security Breaches
Some famous security breach examples mentioned here reflect how they devastate companies and can cause reputational damage and financial loss.
1) X (Formerly Twitter)
In 2018, Twitter urged its 300+ million users to change and update their passwords after a bug exposed all of them. This resulted from an issue with the hashing process, which Twitter used to encrypt their users’ passwords. Although Twitter has fixed the bug, this shows that even the most prominent social media giants can be victims of security vulnerabilities and breaches.
Unfortunately, Twitter was also affected by another potential data breach in 2020 when an issue with its issue made the social media platform admit that it was possible that some of their user’s email addresses, passwords, phone numbers, and credit card details could have been accessed by malicious actors.
2) Yahoo
In 2013, Yahoo became a victim of one of the biggest data breaches in history. Initially, it was reported that a hacker stole the user’s data from one billion accounts, but years later, it was confirmed that it was 3 billion accounts. The security breach compromised the user’s privacy and security, compromising many of their sensitive and confidential data, such as their names, email addresses, birth dates, phone numbers, and other security questions.
3) Equifax
In 2017, Equifax lost the personal details of over 145 million Americans because of a vulnerability in the website application. This included their Personally Identifiable Information (PII), such as their names, SSNs, and driver’s license numbers. These attacks were made over three months, from May to July, but the company officially announced the attacks in September.
4) LastPass
LastPass has been affected by security breaches in the past, and unfortunately, bad luck struck them once again in 2022 when the same attacker caused another security breach. The DevOps Engineer’s computer got hacked, allowing the attacker to implant keylogger malware. The hacker then captured the engineer’s master password when it was being entered and gained unauthorized access to the customer’s vault data.
5) Facebook
In 2019, a server with phone numbers of up to 419 million Facebook users was exposed. The server wasn’t password protected, meaning the database was easily accessible to any outside party. Three months after this incident, hackers exposed a database containing approximately 300 million Facebook users’ names, phone numbers, and user IDs. The database was left unprotected on the Dark Web for two weeks.
6) Uber
In 2022, a hacker gained unauthorized access to Uber’s internal databases. Some significant theories were circulating trying to decipher what could have happened: the hacker could have gained access to Uber’s corporate password through the dark web or implemented social engineering tactics, pretending to be working at Uber and then tricking an Uber contractor into divulging the password.
7) eBay
eBay also experienced a significant security breach in 2014. Though PayPal users’ credit card information wasn’t at risk, many customers’ passwords had been compromised. The company immediately emailed its users and instructed them to change their passwords to remain secure, and no further damage was done.
How Should You Protect Yourself From Security Breaches?
Companies must adopt reliable and efficient security measures against data breaches to ensure their sensitive and confidential data aren’t compromised. Here are some strategies they can implement to ensure they don’t fall victim to data breaches, protect their sensitive data, and prevent financial loss or reputational damage before it is too late. Here are some practical steps they can take:
1) Use AstrillVPN
AstrillVPN encrypts your internet traffic and masks your IP address, ensuring that third parties and malicious actors cannot gain unauthorized access to your sensitive and confidential data. AstrillVPN offers a host of excellent security features, allowing you to protect your sensitive data from a breach in case it occurs. It offers a Kill Switch feature, Smart Mode, Split Tunneling, AES 256 encryption, the industry standard, DNS leak protection, and robust encryption protocols like Wireguard, StealthVPN, and Open VPN.
AstrillVPN also adheres to a strict No Logs policy, which means it does not track your online activities when you use the VPN. Your data and online activities are automatically deleted when you log out of the VPN. These are all top-notch security features you must look for when upgrading your security strategy. AstrillVPN also keeps you secure when you’re on a public network since public networks are the most vulnerable to interception by malicious actors.
2) Use Strong Passwords
Weak passwords are a significant reason for data breaches, enabling hackers and cyber criminals to access corporate networks. Ensure that you’re using strong passwords for all your online accounts. Strong passwords are complex and difficult to guess, making it challenging for hackers and malicious actors to infiltrate your accounts and gain unauthorized access.
When choosing a strong password, ensure it has an uppercase letter, a lowercase letter, special characters, and numbers. This will make it harder for malicious actors to access your accounts and compromise sensitive and confidential information. Companies should also use a password manager to manage their different passwords.
3) Enable Two Factor Authentication
Because weak passwords can compromise data, it’s a good idea to have an additional security measure. Organizations and individuals should not rely on strong passwords alone. Multi-factor authentication (MFA) means people must provide additional verification before accessing their online accounts. This makes it challenging for hackers to access your online accounts. For instance, to access online accounts, you will be asked to verify, for example, a one-time password that gets sent to you through text or email. You may also be required to provide biometric verification to access online accounts. Additional verification
4) Keep Software Updated
Companies should always use the latest software systems to prevent malicious actors from exploiting vulnerabilities within the system. Ensure that all automatic updates for software and applications are enabled, and constantly update and patch software whenever required. This ensures that hackers cannot exploit any vulnerabilities, keeping your data safe and secure.
5) Use HTTPS Websites
When browsing websites, be sure that their URLs are secure. For example, use HTTPS websites at the beginning of their URLs. HTTPS websites are beneficial because they encrypt the data between your browser and the website. This means all your data, such as your emails, passwords, and credit card numbers, is protected from eavesdropping and interception. HTTPS also verifies that you are communicating with the intended website.
6) Use Reliable Antivirus Software
Protection from data breaches is incomplete without investing in reliable antivirus software. Antivirus software ensures that it will detect viruses and malware in real-time and immediately remove them from your device. Antivirus software can protect you from data breaches because if hackers and malicious actors infiltrate your devices and inject malware to compromise your sensitive and confidential data, the antivirus software will be able to detect it in real-time and then remove it from your device. This will remove malware and viruses before they cause further damage.
When choosing antivirus software, ensure that they can detect threats in real-time and remove them, they don’t impact the system’s performance, it includes an integrated firewall that adds an extra layer of protection from unauthorized access, offers email protection, is easy to use for someone who isn’t that tech-savvy, and is compatible with various operating systems like iOS, Android, Windows, macOS, and Linux.
7) Employee Training
Organizations must educate employees on the best cybersecurity practices to protect themselves from data breaches. They should be taught how to detect a data breach from the start and what steps to take to protect themselves if it happens. Companies should invest in regular training sessions, the latest cybersecurity trends, and emerging threats to keep employees vigilant. Training employees and creating awareness about cyber attacks and how to curb them is one of the most effective ways to prevent the effects of cyber-attacks and data breaches.
8) Be Cautious Of Suspicious Links & Attachments
Phishing scams are one of the most common ways in which data breaches occur. The scammer would pretend to be an essential figurehead of the company or someone you trust and trick you into divulging sensitive and confidential information. Sometimes, you may also receive emails or messages appearing too good to be true, and the minute on any links or attachments to claim a prize or for some other purpose, all of your sensitive and confidential data gets compromised.
That’s why it’s essential that you remain cautious and not fall for these scams. When you suspect something, don’t open links or attachments, and confirm with the person whether they’ve sent the email. Many malicious actors pretend to be higher-ups in the company to get employees to divulge sensitive information, so confirm if it’s them before taking any action and clicking on the links and attachments they’ve sent.
What Should You Do If You’ve Been Victim Of A Security Breach?
So you’ve been hit with a security breach, and the damage has been done. Here are some steps that you need to be taking immediately to mitigate some of the risks of a data breach:
- If the breach has compromised your financial information, call your bank immediately and ensure that your credit cards and bank accounts get frozen so that no one can steal your money.
- Change the passwords on all your online accounts, and ensure that you have different passwords for all your accounts so that it is harder for malicious actors to intercept your sensitive and confidential information.
- Run an anti-virus scan. It will detect any emerging threats in real-time and immediately remove the malware or virus from your device.
- Be vigilant when it comes to social engineering attacks. If it’s a person you trust who’s sending you emails or someone in your company, reach out to them personally and verify if they sent these requests before clicking on any suspicious links that they sent.
- Try to determine exactly what data has been stolen. This will give you an idea of how best to handle the situation. If your Personally Identifiable Information (PII) gets stolen, you’ll need to act faster before you become a victim of identity theft.
Wrapping Up
Security breaches can cause actual harm to companies and individuals alike. It can compromise their privacy, and for companies, it can go on to ruin everything they’ve worked so hard to build. It can cause reputational damage, financial loss, and loss of trust among employees and customers since they can’t protect their data. We live in a day and age where data breaches and security threats are growing by the minute. Therefore, strict action is needed to prevent these threats. This guide contains all the strategies you must implement to protect yourself from security threats so you’re in good hands. Your data will remain safe and secure.
Frequently Asked Questions (FAQs)
Data breaches are caused by malware attacks, social engineering tactics, and weak passwords, making it easier for malicious actors to gain unauthorized access to sensitive data.
It depends on the security measures in place. If they’re not that strict, malicious actors can easily intercept sensitive and confidential data.
Security breaches are caused by system vulnerabilities, weak passwords, malware attacks, phishing attacks, insider threats, and DDoS attacks. Companies need to adopt strategies to curb these threats.
Yes, security breaches are a major threat. They compromise the sensitive and confidential data of millions of users and harm businesses and individuals.


No comments were posted yet