What is a DDoS Attack? Risks, Types, and Prevention Strategies

Arsalan Rathore
A DDoS, or Distributed Denial of Service attack, is one of the most formidable threats in today’s digital arena. These attacks flood websites, servers, or networks with massive malicious traffic from thousands of compromised devices (botnets). As a target struggles to process the overload, legitimate users are denied access, services go offline, and damage to reputation and revenue quickly follows.
In the first quarter of 2025 alone, Cloudflare blocked 20.5 million DDoS attacks, reflecting a dramatic 358 percent year-over-year spike in volume.
While some DDoS attacks are launched for ransom, competitive disruption, or ideological reasons, recent campaigns show how attackers evolve in skill and scale. In this guide, we explore the most recent DDoS trends, key statistics, and how you can prevent falling prey to them.
Table of Contents
Recent Statistics about DDoS Attacks
The latest cybersecurity data paints a concerning picture of how quickly the DDoS threat landscape is evolving.
- More than 8 million attacks were recorded globally in the first half of 2025.
- The frequency of hyper-volumetric attacks exceeding 1 terabit per second has increased significantly, with thousands blocked every quarter.
- Application layer attacks (Layer 7) grew by over 70 percent year-over-year, targeting APIs and encrypted HTTPS connections.
- Gaming and financial sectors remain the top two industries affected, followed by e-commerce and telecommunications.
- Around 85 percent of attacks remain small in scale, often used as distraction tactics to mask data theft or ransomware deployment.
How DDoS Attacks Work?
A Distributed Denial of Service (DDoS) attack uses multiple compromised systems, often spread across various geographical locations, to flood a target with a massive volume of traffic. This flood of traffic overwhelms the target’s resources, causing it to slow down, crash, or become entirely unavailable to legitimate users. Let’s break down how these attacks are structured and executed:
1. Botnets and Compromised Devices
A network of compromised devices known as a botnet is at the core of a DDoS attack. Cybercriminals gain control of these devices, often computers, smartphones, or IoT devices, by infecting them with malware. The users of these devices typically have no idea that their devices have been compromised. Once controlled, the attacker uses these botnets to send massive amounts of data to the target.
Using botnets makes DDoS attacks highly distributed, as the traffic comes from many sources rather than one. This distribution makes it difficult for security solutions to identify and block malicious traffic since it mimics legitimate user activity.
2. Traffic Overload
Once a botnet is in place, the attacker instructs all the compromised devices to send overwhelming requests or traffic to the target’s server or network. This is often done through automated scripts or specialized software. Depending on the type of DDoS attack, the incoming traffic can come in different forms, including HTTP requests, UDP packets, or TCP connections.
There are three main types of traffic overloads commonly seen in DDoS attacks:
- Volumetric Attacks: These attacks flood the target’s bandwidth with large amounts of data, consuming the available bandwidth and preventing legitimate traffic from reaching the target.
- Protocol Attacks: These attacks exploit weaknesses in network protocols, such as SYN floods or Ping of Death attacks, overwhelming network resources like firewalls or load balancers.
- Application Layer Attacks: These attacks target specific applications or services, such as websites or APIs, and focus on exhausting the resources of the server hosting the application (e.g., HTTP floods).
3. Exhausting Target Resources
The main goal of a DDoS attack is to exhaust the target system’s resources, whether bandwidth, CPU power, memory, or database connections, so it can no longer handle legitimate user requests. As the system becomes overloaded, its performance degrades, resulting in a slowdown, intermittent service, or a complete shutdown.
For instance, a volumetric attack may consume all available network bandwidth, while an application layer attack could overwhelm a server’s CPU by sending thousands of resource-intensive requests. In either case, the result is the same: the target cannot function properly.
4. Smokescreens for Other Attacks
In some cases, DDoS attacks are not just standalone events; they are used as smokescreens to divert attention while a more damaging attack occurs. For example, while the IT team is focused on mitigating the DDoS traffic, attackers may simultaneously attempt to infiltrate the network to steal sensitive data or deploy ransomware.
This tactic adds another layer of complexity, making DDoS attacks a significant component of modern cyber warfare and cybercrime. Attackers can use them for extortion, sending ransom demands to restore the target’s services, or as part of coordinated attacks for political or competitive reasons.
Common Types of DDoS Attacks
Distributed Denial of Service (DDoS) attacks come in various forms, each designed to target specific vulnerabilities in a network or server. While the goal remains the same—overwhelm the target’s resources to deny service to legitimate users—the methods used can vary greatly. Understanding the different types of DDoS attacks is crucial for defending against them effectively. Here are the most common types:
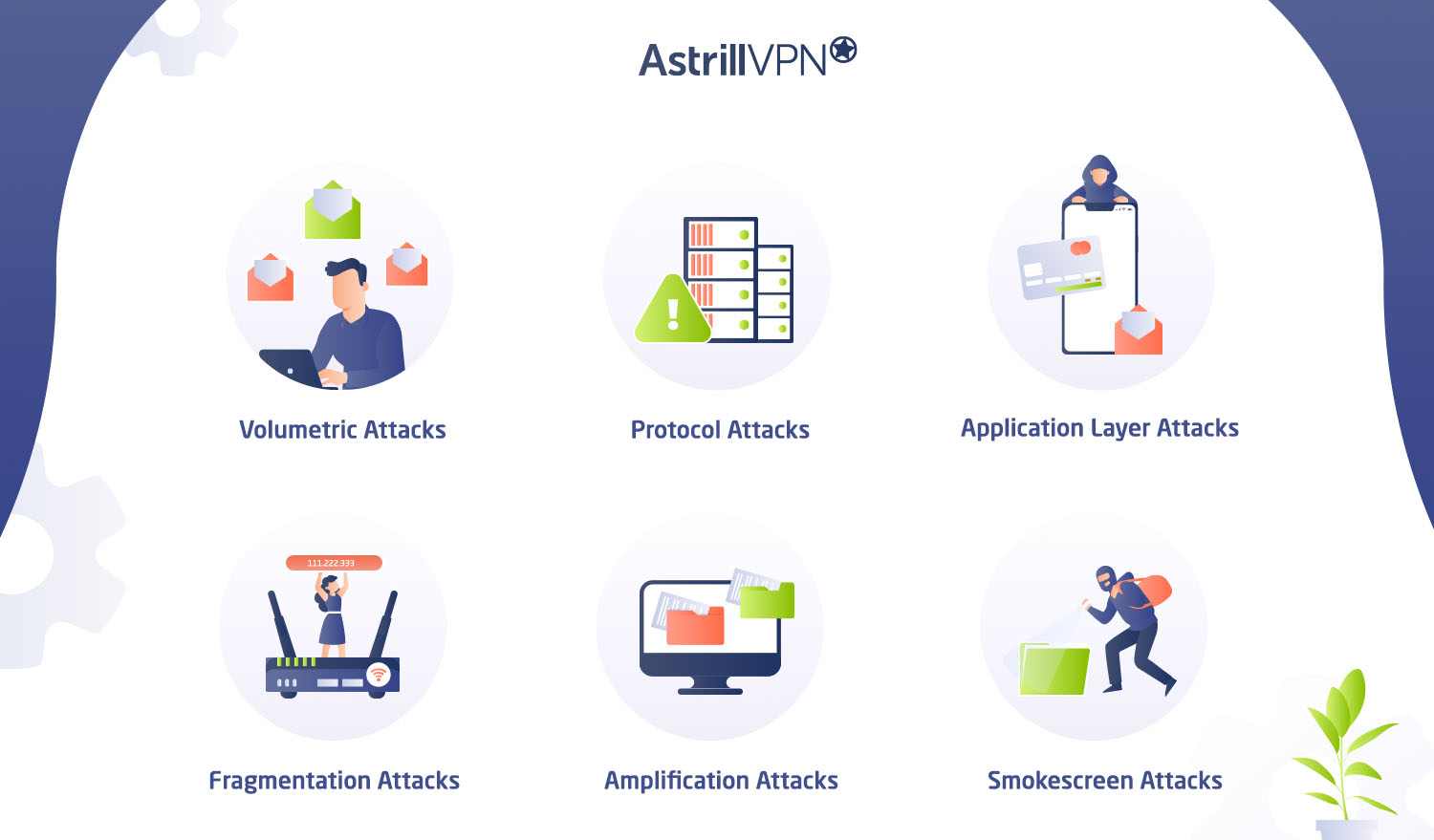
1. Volumetric Attacks
Imagine trying to enter a store, but a huge crowd blocks the entrance, making it impossible for anyone to get in. That’s essentially how a volumetric attack works. Volumetric DDoS attacks aim to saturate the target’s bandwidth by overwhelming it with massive traffic.
These attacks flood the target with more traffic than it can handle, clogging its network pipes and preventing legitimate traffic. They are measured in bits per second (bps). These attacks are the most common because they are relatively easy to execute and can cause significant damage by consuming the target’s available bandwidth.
1. UDP Floods
A volumetric attack is when the attacker sends many User Datagram Protocol (UDP) packets to random ports on the target machine. This forces the target to check for non-existent applications, consuming its resources repeatedly.
2. DNS Amplification
A reflective attack is where an attacker exploits open DNS servers to flood a target with DNS response traffic, amplifying the size of the data and maximizing the attack’s impact.
2. Protocol Attacks
Protocol attacks, also known as state-exhaustion attacks, target weaknesses in network protocols by consuming server or network resources like firewalls and load balancers. These attacks overload the infrastructure by taking advantage of protocol-specific weaknesses.
1. SYN Flood
In a SYN flood attack, the attacker sends a rapid succession of TCP/SYN requests (used to initiate a TCP connection) to the target but never completes the handshake. This leaves the target’s server waiting for responses, consuming all its available resources and preventing legitimate connections.
2. Ping of Death
This attack involves sending malformed or oversized ping packets to the target system. When the target attempts to reassemble the packets, it crashes or becomes unstable.
Protocol attacks are effective because they directly interfere with the network infrastructure’s ability to manage connections, causing devices like firewalls or load balancers overwhelmed.
3. Application Layer Attacks
Application layer DDoS attacks (also known as Layer 7 attacks) specifically target the application or service running on a server rather than the network itself. These attacks are more sophisticated, as they aim to exploit vulnerabilities in the software or applications the server is running. Application layer attacks are measured in requests per second (RPS).
Application layer attacks can be harder to detect because they mimic legitimate user behavior, making it more difficult for traditional security measures to filter out malicious traffic. Here are the two sub-types of Application layer attacks:
1. HTTP Floods
In an HTTP flood, the attacker sends many HTTP requests to the web server, overwhelming it with requests to retrieve web pages or perform actions. The high volume of seemingly legitimate traffic can cause the server to slow down or crash.
2. Slowloris
This attack opens multiple connections to the target web server and sends partial HTTP requests. It deliberately leaves connections open for an extended period, tying up resources on the server and preventing it from handling legitimate connections.
Application layer attacks can be harder to detect because they mimic legitimate user behavior, making it more difficult for traditional security measures to filter out malicious traffic.
4. Fragmentation Attacks
Fragmentation attacks, such as IP fragmentation, involve sending fragmented packets to the target. The system becomes overwhelmed while attempting to reassemble the fragmented packets, leading to performance degradation or a complete shutdown. There’s only one type of fragmentation attack:
● Teardrop Attack
This attack involves sending malformed IP fragments that the target cannot reassemble properly, causing it to crash. In this attack, the offset fields in the fragmented packets overlap, making reassembly impossible.
5. Amplification Attacks
Amplification attacks take advantage of the increased volume of response traffic compared to the request traffic. Attackers send a small request to a vulnerable server, which responds with a large amount of data to the victim, overwhelming its resources.
● NTP Amplification
This attack abuses the Network Time Protocol (NTP), sending small queries to NTP servers that respond with significantly larger data packets. By sending the responses to the target, the attacker can flood the target with massive traffic without requiring much bandwidth.
Why Are DDoS Attacks Dangerous?
Now that you know what does DDoS mean and what its types are, let’s talk about why it’s dangerous. DDoS attacks pose a significant threat to individuals, businesses, and even governments because they can disrupt services, cause financial losses, and damage reputations. Here’s why these attacks are so dangerous:
1. Disruption of Critical Services
One of the primary dangers of a DDoS attack is its ability to bring down essential services. Whether it’s a government website, online banking, healthcare services, or any business relying on web-based systems, a successful DDoS attack can make these services unavailable. This can have serious consequences:
- When medical services are disrupted, patients may not receive the care they need in time.
- Online banking services becoming unavailable can prevent people from accessing their funds or making crucial transactions.
- Public services, tax portals, and other government platforms can be targeted, causing widespread disruption for citizens.
2. Financial Losses
Businesses that rely on their online presence to generate revenue (like e-commerce stores or subscription-based services) can suffer immense financial losses during a DDoS attack. Every second a website or service is down, companies may lose customers and sales. According to studies, companies can lose thousands of dollars per minute during a DDoS attack, especially in industries like retail, where downtime can impact sales directly.
In addition to direct revenue loss, there are also indirect costs, such as:
- Customers who experience a service outage may turn to competitors or lose trust in the affected company’s reliability.
- After an attack, businesses must invest in mitigation measures, IT support, and potential system overhauls to prevent future attacks.
3. Smokescreen for Other Attacks
A DDoS attack can often serve as a distraction, hiding more damaging activities like data breaches, malware insertion, or hacking attempts. While the IT team is busy managing the overwhelming traffic from a DDoS attack, hackers can exploit other vulnerabilities and gain access to sensitive data.
For example:
- Attackers might use the cover of a DDoS attack to steal personal information, intellectual property, or financial records.
- Hackers might install ransomware or spyware, causing further damage after the attack subsides.
4. Easy to Launch, Hard to Defend
DDoS attacks are dangerous because they are so easy to carry out. With the rise of botnets (networks of compromised computers), attackers can launch large-scale DDoS attacks using relatively simple tools. These attacks are also cheap to rent or purchase on the dark web, allowing cybercriminals with limited resources to wreak havoc on large targets.
5. Legal and Regulatory Consequences
Organizations that experience DDoS attacks may also face legal or regulatory consequences if sensitive data is compromised or services that need to remain online (such as critical infrastructure) go offline for extended periods. In certain sectors, such as finance or healthcare, businesses must follow stringent regulations regarding the security and availability of services. A DDoS attack that results in a data breach could lead to significant fines or lawsuits.
6. Long-Term Reputation Damage
Beyond the immediate impact on operations, DDoS attacks can damage a company’s reputation. Customers who experience downtime or need help accessing services may become frustrated and lose trust in the business. The perception that a company is vulnerable to attacks can deter future customers from engaging with them. Restoring customer confidence after such an incident can take a long time, and some companies never fully recover their reputations.
What Is the Number One DDoS Target in 2025
The gaming and online entertainment industry is the most heavily targeted sector in 2025. Gaming servers are always online, attract millions of concurrent users, and require low latency, making them ideal targets for disruption. Attackers often exploit the visibility of such platforms to gain attention, cause chaos during major tournaments, or extort companies through downtime threats.
Other highly targeted industries include financial services, government agencies, and cloud providers. As businesses move more services online, the potential impact of a DDoS attack increases, especially when digital infrastructure underpins global communication, finance, and entertainment.
AI-Powered DDoS: The Emerging Threat
The integration of artificial intelligence into DDoS strategies is reshaping how attacks unfold. AI systems can now analyze defensive patterns in real time and modify attack methods instantly to evade detection. This level of adaptability allows hackers to sustain longer, more efficient, and far more destructive campaigns.
- Automated decision-making: AI-driven botnets can switch between attack vectors without human input.
- Target prediction: Machine learning models identify vulnerable servers before launching an attack.
- Defense evasion: AI tools help attackers recognize traffic filtering patterns and adapt packet structures on the fly.
The Cost of DDoS Attacks
The financial impact of DDoS attacks continues to rise, affecting both large and small businesses.
- The average cost of downtime during a DDoS incident now exceeds $300,000 per hour for large organizations.
- E-commerce platforms face heavy losses in sales and customer trust when outages occur during high-traffic periods.
- Financial institutions risk service interruptions that can impact global transactions and market operations.
- Brand reputation and customer confidence are often the hardest-hit areas, taking months or even years to recover.
How to Identify a DDoS Attack
Identifying a DDoS attack early is crucial to minimize its impact. However, distinguishing a DDoS attack from regular network congestion or a temporary spike in traffic can be challenging. Here are some key indicators that a DDoS attack may be happening:
1. Unusually Slow Network Performance
One of the most common signs of a DDoS attack is extremely slow or unresponsive services. This could include:
- Websites taking a long time to load.
- Slow responses from applications, particularly those hosted online.
- Lag in network performance across internal systems.
2. Website or Service Unavailability
If your website or online service suddenly becomes unreachable for users, it could be due to a DDoS attack. In particular, if your infrastructure (web servers or databases) is functioning correctly but users are still unable to access your site, the issue could stem from an overwhelming amount of malicious traffic aimed at overloading your servers.
Signs of complete service unavailability due to a DDoS attack include:
- Frequent timeout errors for users trying to access your site.
- Intermittent service availability (services going down and then coming back up).
3. Unexplained Traffic Spikes
A major sign of a DDoS attack is a massive, unexpected spike in traffic that doesn’t align with your usual user behavior or marketing activities. Legitimate traffic spikes, such as those during a product launch or flash sale, can usually be predicted based on business events or seasonal changes. However, a DDoS attack will cause sudden, sharp traffic increases without any clear reason.
Key indicators:
- Anomalies in website analytics showing traffic coming from unusual locations or IP ranges.
- Traffic requests coming from a single source or a large number of unknown or suspicious IP addresses (botnet activity).
4. Increased Load on Specific Resources
DDoS attacks are designed to overwhelm specific parts of your system, whether it’s the network bandwidth, application servers, or even your DNS infrastructure. You may notice resource utilization metrics shooting up:
- CPU and memory usage skyrocketing on servers.
- Excessive disk read/write activities.
- Network bandwidth being used up at unusually high rates.
5. Multiple Unusual IP Addresses or Geographic Locations
A clear sign of a DDoS attack is when you see traffic flooding in from suspicious or uncommon IP addresses. If the traffic is coming from regions where you don’t typically have a customer base or notice multiple requests from the same IP address within a short time, this is a strong indicator of a DDoS attack.
Additionally, DDoS attacks are often carried out by botnets, networks of compromised devices spread across the globe. This results in traffic from diverse locations, often unrelated to your target audience.
6. Disruption in Specific Protocols
Certain types of DDoS attacks focus on exploiting specific communication protocols, like SYN flooding or DNS amplification. If you’re monitoring your network and notice unusual activity within specific protocols (such as a flood of DNS requests or a high number of SYN packets), it could be a sign of a DDoS attack targeting that protocol.
7. Alerts from Monitoring Systems
If you have a network monitoring system, it can help you detect unusual behavior that may indicate a DDoS attack. Alerts from intrusion detection/prevention systems (IDS/IPS) or DDoS mitigation tools can notify you of excessive or suspicious traffic. These systems can sometimes automatically trigger responses, such as blocking traffic from known malicious IPs or rerouting traffic to minimize the attack’s impact.
How to Stay Protected from DDoS Attacks
Protecting yourself or your business from DDoS attacks requires a multi-layered DDoS security approach, combining preventive strategies, proactive monitoring, and rapid response techniques. Here’s how you can stay safe from DDoS attacks:
1. Use a Reliable DDoS Protection Service
One of the most effective ways to protect against DDoS attacks is to use a dedicated DDoS protection service. These services monitor traffic and mitigate attacks in real time by absorbing or blocking malicious traffic before it reaches your network. Popular solutions include:
- Content Delivery Networks (CDNs): CDNs distribute traffic across multiple servers, reducing the likelihood of an attack overwhelming any one server. CDNs like Cloudflare or Akamai offer built-in DDoS protection.
- VPNs with DDoS Protection: A reliable VPN like AstrillVPN provides added layers of security by encrypting traffic and shielding your IP address from attackers, making it harder for them to target you.
- DDoS Mitigation Tools: Some advanced tools, like Arbor Networks or AWS Shield, offer specific DDoS protection for websites and networks by filtering out malicious traffic.
2. Increase Bandwidth Capacity
A simple yet effective strategy is to ensure that your network infrastructure has sufficient bandwidth to handle large traffic volumes. While this won’t prevent a DDoS attack, it can make it more difficult for an attack to overwhelm your servers, buying you valuable time to mitigate the attack. This is especially important for businesses that rely heavily on online services.
3. Implement Traffic Filtering
By using firewalls, IDS, and IPS, you can filter out malicious traffic. These systems work by inspecting incoming traffic and identifying patterns typical of DDoS attacks, such as multiple requests from the same IP or unusual traffic spikes. Some techniques include:
- IP blacklisting: Blocking known malicious IP addresses from accessing your network.
- Rate limiting: Restricting the number of requests from specific IP addresses in a given time period.
4. Use a Load Balancer
A load balancer helps distribute incoming traffic across multiple servers. By spreading traffic over a wider area, you reduce the chances of a DDoS attack overwhelming any single point in your network infrastructure. Cloud-based load balancers can dynamically allocate resources in real time, adjusting to traffic surges or potential attacks.
5. Employ Redundancy and Failover Systems
For businesses, redundancy is essential. This means hosting your services across multiple data centers or geographically distributed servers. If a DDoS attack targets one location, the traffic can be rerouted to another, ensuring your service remains available. Failover systems automatically divert traffic to backup servers or data centers, helping minimize an attack’s impact.
6. Regularly Monitor Network Traffic
Proactively monitoring traffic is one of the best defenses against a major DDoS attack. Monitoring tools, such as SolarWinds or Nagios, can help you track traffic patterns and identify anomalies that might signal the beginning of a DDoS attack. This allows for faster response times to mitigate the damage. Real-time monitoring can detect:
- Traffic surges from unusual locations or IP addresses.
- Excessive requests targeting a specific web service or application.
7. Implement DNS Security
DNS (Domain Name System) services are often targeted by DDoS attacks. To protect your DNS from such attacks, consider the following:
- Using a managed DNS provider with built-in DDoS protection, such as AWS Route 53 or Google Cloud DNS.
- Distributing DNS requests across multiple servers and data centers reduces the risk of your DNS infrastructure being overwhelmed.
- DNS rate-limiting restricts the number of queries a single IP address can make in a given period.
8. Stay Prepared with a DDoS Response Plan
Having a response plan in place before an attack happens can significantly reduce downtime and damage. A well-thought-out plan should include:
- Clear roles and responsibilities for your IT and security teams.
- Immediate steps to be taken once an attack is identified (e.g., alerting your DDoS protection service or switching to backup servers).
- Communication strategies for informing customers and stakeholders about service interruptions.
- Regular drills and simulations to ensure everyone knows how to respond to an actual DDoS event.
9. Secure IoT Devices and Networks
Ensure your IoT devices are secure by:
- Changing default usernames and passwords to strong, unique credentials.
- Updating device firmware regularly to patch known vulnerabilities.
- Isolating IoT devices from your main network, reducing the risk of them being compromised and used in a DDoS attack.
Recent DDoS Attack Cases
1. OVHcloud Struck by Record DDoS Attack (2024)
In July 2024, OVHcloud, a prominent cloud service provider, was the victim of a record-setting DDoS attack that peaked at 840 million requests per second (fps). This incident, reported by The Hacker News, highlights the escalating scale and intensity of cyber threats targeting major cloud services.
The attack disrupted OVHcloud’s services and raised alarms about the potential vulnerabilities of cloud infrastructure in the face of such overwhelming traffic. OVHcloud confirmed its quick response to mitigate the attack, showcasing the need for continuous improvements in cybersecurity measures to protect against future threats.
2. Pennsylvania Court System Disrupted by DDoS Cyberattack (2024)
In 2024, Pennsylvania’s court system was targeted by a DDoS cyberattack, causing significant disruptions to operations. As reported by StateScoop, the attack resulted in temporary outages of various online services, affecting court filings and access to legal information.
The state quickly mobilized to restore systems and mitigate the impact, implementing measures to bolster cybersecurity in response to the incident. Officials emphasized the importance of maintaining the integrity and availability of court services, especially in the face of such cyber threats.
3. DDoS Attacks Cause Major Internet Disruptions in Crimea
In 2024, Crimea experienced significant internet disruptions attributed to DDoS attacks targeting telecommunications infrastructure in the region. According to The Record, these attacks led to widespread outages, severely impacting residents and businesses reliant on online connectivity.
Telecom companies reported increased traffic and malicious activity aimed at crippling their services, suggesting a coordinated effort to disrupt internet access in Crimea. The ongoing geopolitical situation has intensified such cyber threats, with DDoS attacks becoming a common tool for entities seeking to undermine the stability of digital services in conflict zones.
4. Italian Bank Disrupted by DDoS Attack (2023)
As reported by The Record, in early 2024, a series of DDoS attacks attributed to Russian hackers targeted multiple organizations across Italy. This wave of cyberattacks aligns with the ongoing geopolitical tensions, highlighting how hacktivism has escalated in response to international conflicts.
The attackers claimed to utilize extensive botnets, which are networks of compromised devices, to launch overwhelming traffic at targeted websites, causing significant service disruptions. Notably, these attacks affected essential services, disrupting operations for various businesses and public institutions. The scale and precision of the attacks indicate a sophisticated level of planning, raising concerns about the vulnerability of critical infrastructure to similar threats in the future.
5. GitHub Faces Major Attack (2024)
GitHub’s security team reported that in early 2024, the platform faced a sophisticated DDoS attack that peaked at 40 million requests per second (rps). This attack caused partial outages, affecting many developers relying on GitHub for their projects. The quick response from GitHub’s security team helped mitigate the damage.
6. Cloudflare’s Mitigation of a Record-Breaking DDoS Attack (2023)
Cloudflare successfully mitigated a massive 3.8 terabits per second (Tbps) DDoS attack, the largest ever recorded in history. The attack targeted the company’s network infrastructure, using amplification techniques and volumetric traffic floods. The malicious traffic primarily originated from compromised IoT devices and botnets.
Despite the record-breaking scale, Cloudflare’s security infrastructure managed to thwart the attack without service disruption, showcasing the growing intensity of modern DDoS attacks.
7. Microsoft Azure Targeted in Massive Attack (2023)
The Microsoft Azure Security report reported that in June 2023, Microsoft Azure was hit by a DDoS attack peaking at 3.47 terabits per second (Tbps), one of the largest in history. The attack primarily targeted cloud infrastructure in Europe, causing temporary service disruptions for businesses relying on Azure. The attack highlighted the growing complexity and size of DDoS incidents targeting cloud services.
FAQs
Yes, DDoS attacks pose a significant risk to businesses and organizations of all sizes. They can lead to extensive downtime, financial losses, and damage to an organization’s reputation.
Hackers use DDoS attacks for financial gain, political activism, competitive advantage, or personal vendettas. The motivations can vary, but the end result is often a significant disruption of services and potential financial damage.
A VPN can help protect against DDoS attacks by masking your IP address and potentially offering some mitigation, but it is not a foolproof solution. A multi-layered security strategy is recommended for optimal protection.
The duration of DDoS attacks can vary widely based on several factors, including the attack’s intensity, the methods used, and the target’s defenses. Generally, these attacks can last from just a few minutes to several days.
Yes, DDoS attacks are illegal in most countries around the world. They fall under various cybercrime laws designed to protect the integrity and availability of computer systems and networks. DDoS attacks involve intentionally overwhelming a target’s servers or network infrastructure, rendering them inaccessible to legitimate users. This disruption is considered unauthorized access and interference with computer systems, which is a criminal offense in many jurisdictions.


No comments were posted yet