Internet Service Providers, or ISPs, provide internet access to homes, businesses, and other entities. They act as intermediaries, bridging the gap between users and the vast Internet infrastructure.
Since ISPs provide internet service, it’s obvious that they have access to certain things we do over the internet. But the question is, what do ISPs see? And what type of information do they have access to?
Understanding what ISPs see on our internet history is crucial for safeguarding our personal data, protecting our online privacy, and maintaining control over our digital footprint. Follow this guide to understand what ISPs can see and how much access to our information they have.
Table of Contents
Importance of Internet Privacy
Internet privacy has become critical as our online activities generate vast amounts of data. From search queries and website visits to communication and social media interactions, our internet history can reveal valuable insights into our preferences, habits, and personal details.
Protecting internet privacy is crucial to safeguarding individual freedoms, preventing identity theft, and maintaining a sense of autonomy in the digital age.
How ISPs Work
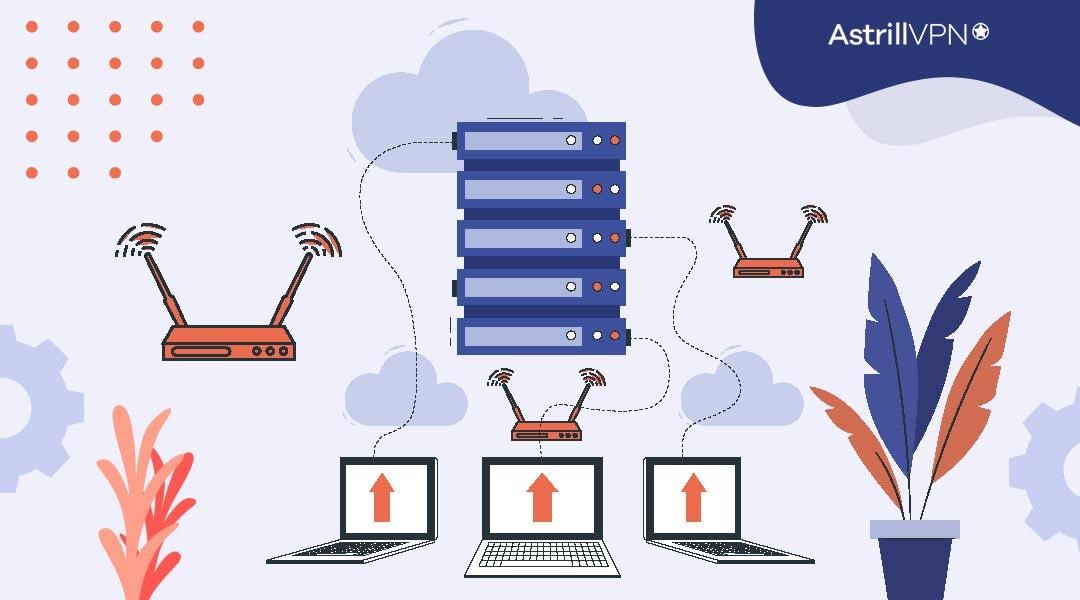
ISPs operate a complex network infrastructure that enables data transmission between users and the Internet. They connect to larger network backbones and data centers to access the World Wide web’s vast expanse. ISPs deliver internet services to homes and businesses through various technologies, offering different speed tiers and connection types to suit users’ needs.
Internet Traffic Routing
When you enter a website URL or search for information online, your data is divided into small packets and routed through the ISP’s network. The ISP’s routers direct these packets through the most efficient path to reach their destination, which may involve multiple hops through different networks before arriving at the desired website’s servers.
Data Collection and Storage Practices
As data packets flow through their network, ISPs have the technical capability to collect and analyze information about users’ online activities. This data can include IP addresses, visited websites, search queries, and even the duration of online sessions.
While some data is essential for network management and troubleshooting, the extent of data collected varies between ISPs and can raise concerns about user privacy.
What Do ISPs See?
Net neutrality has again come to the fore and shifted our focus from a more concerning issue that we, Internet users, deal with privacy. Although we have always known that ISPs can see some of what we do online, the idea of what exactly and to what extent was unclear.
Countless studies and actual disclosure by Internet providers have given us enough evidence about ISPs’ spying nature. Knowing what your ISP can see can help you make better decisions about your online activities, thereby safeguarding yourself from a bad scenario.
Types of Information Collected
ISPs typically gather metadata and usage data as users navigate the internet. Metadata includes information about the source and destination of data packets, timestamps, and session durations.
Usage data encompasses the websites visited, search terms used, and the types of content accessed. ISPs may also collect device information, such as MAC addresses and device identifiers, for network management purposes.
ISP Tracking and Monitoring

ISPs have the technical capability to track and monitor their users’ internet activities. This monitoring process can involve various methods, each providing valuable insights into user behavior. Some of the key tracking and monitoring techniques employed by ISPs include:
1. Deep Packet Inspection (DPI)
Deep Packet Inspection is a sophisticated technique used by ISPs to inspect the content of data packets passing through their network. DPI allows ISPs to analyze the actual data being transmitted, including website content, emails, and file downloads. While DPI has legitimate applications for network management, it raises concerns about user privacy as it can reveal sensitive information about users’ online activities.
2. Metadata Collection
Metadata refers to the data about data, and ISPs often collect metadata related to users’ internet usage. This includes information such as IP addresses, timestamps, websites visited, and the duration of online sessions. Although metadata may not reveal the exact content of the data transmitted, it can still provide valuable insights into users’ online behavior and patterns.
3. Behavioral Tracking and Profiling
ISPs can create user profiles based on browsing habits, preferences, and online interactions through the data they collect. This behavioral tracking enables ISPs to offer targeted advertisements and services to users. However, it also raises concerns about the level of user surveillance and the potential for sharing this data with third-party advertisers or other entities without users’ explicit consent.
Types of Information ISPs collect
Here are the main types of information ISPs can see and collect:
1. IP Addresses
Every device connected to the internet is assigned a unique identifier called an IP address. ISPs can see both the public IP address assigned to the user’s router and the private IP addresses assigned to individual devices on the local network. IP addresses are crucial for routing internet traffic to the correct destination.
2. Website Visits
ISPs can see the websites users visit, including the specific URLs or domains. This information is typically collected through DNS (Domain Name System) requests made by users’ devices to translate human-readable website addresses (e.g., www.example.com) into IP addresses that computers can understand.
3. Search Queries
When users perform online searches, their search terms are sent to the search engine’s servers for processing. ISPs can intercept and see these search queries, giving them insights into users’ interests and intentions.
4. Online Communication
ISPs can observe communication conducted over the internet, including emails, instant messaging, and VoIP (Voice over Internet Protocol) calls. Although the content of encrypted communications remains unreadable, ISPs can still see the metadata, such as the source and destination addresses and timestamps.
5. Device Information
ISPs can gather information about the devices users connect to the internet, including their MAC (Media Access Control) addresses, unique device identifiers, and operating systems. This data helps ISPs manage network traffic and troubleshoot connectivity issues.
6. Connection Timestamps
ISPs log timestamps of when users connect to and disconnect from the internet. This data allows ISPs to monitor network usage and ensure stable service delivery.
7. Bandwidth Usage
ISPs can track the amount of data users upload and download, known as bandwidth usage. This information is crucial for billing users according to their data plans and managing network capacity.
8. Location Information
Based on the user’s IP address and other available data, ISPs can infer the user’s approximate location. This information is useful for providing geographically targeted services and complying with legal requirements, such as local data protection laws.
9. Traffic Source and Destination
ISPs can see the source (i.e., user’s device) and destination (i.e., the server or website) of internet traffic. This information is essential for routing data packets efficiently across the internet.
10. App and Service Usage
ISPs can analyze the apps and online services users access, including streaming platforms, social media sites, and online gaming services. This data helps ISPs understand network traffic patterns and user preferences.
Potential Risks and Concerns
1. Privacy and Surveillance Issues
ISP tracking and monitoring raise significant privacy and surveillance concerns. Users may feel uncomfortable knowing that their online activities are being monitored and that their internet history is being stored. This data could be accessed by ISPs, government agencies, or unauthorized third parties, compromising user privacy and civil liberties.
2. Data Breaches and Hacking Threats
ISP databases that store user data become attractive targets for hackers and cybercriminals. A successful data breach could expose sensitive user information, including login credentials, financial data, and browsing history. Such breaches can lead to identity theft, financial fraud, and other cyberattacks against users. Over the years, there have been several cases in which data breaches have ruined people’s lives.
3. Third-Party Sharing of Data
ISPs, especially in countries with fewer privacy regulations, may share or sell user data to third-party companies for advertising and other purposes. Users often have limited control over how their data is used once it leaves the ISP’s domain, leading to potential misuse and unwanted targeted advertising.
Protecting Your Internet History
Here are some effective methods and best practices to safeguard your internet history:
Encryption and HTTPS
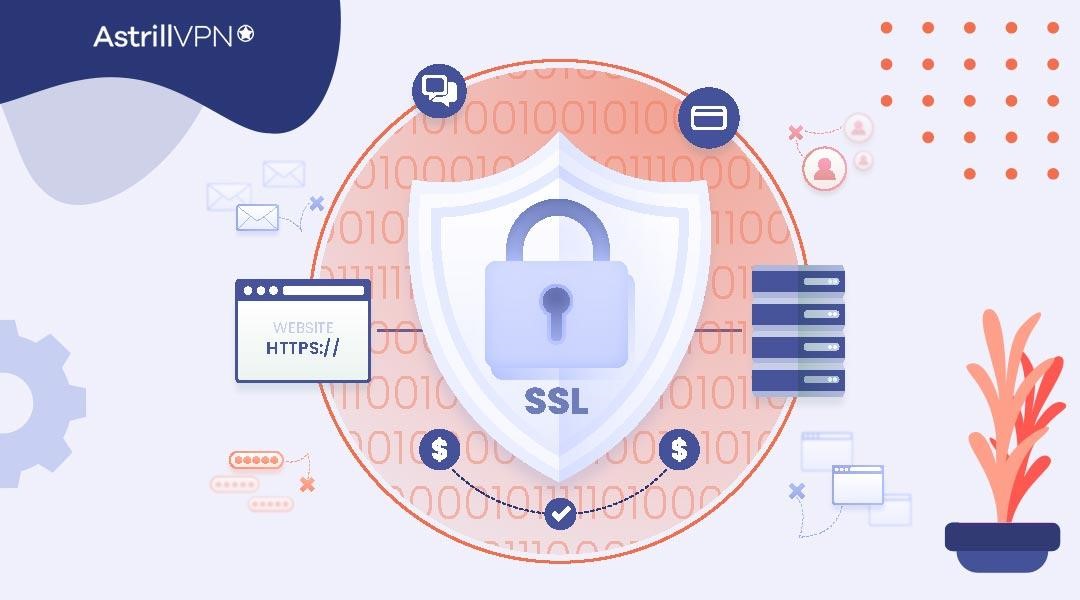
Ensure your online communications are encrypted using HTTPS (Hypertext Transfer Protocol Secure). HTTPS encrypts the data exchanged between your browser and websites, making it challenging for ISPs or malicious actors to intercept and decipher your internet activities.
Virtual Private Networks (VPNs)

VPNs offer an additional layer of privacy by encrypting your internet traffic and routing it through secure servers located in different geographic locations. This shields your online identity and browsing history from your ISP and potential eavesdroppers.
AstrillVPN ensures the anonymity of its users through AES 256-bit encryption. Also, Astrill has highly optimized servers that enable users to bypass ISP throttling.
Clearing Browsing History and Cookies

Frequently clearing your browsing history and cookies can help reduce the amount of data ISPs store about your internet activities. This minimizes the potential for unauthorized access to browsing habits and personal information.
ISP Policies and Transparency
Review your ISP’s privacy policy thoroughly to understand what data they collect, how long they retain it, and how they use or share it. Being informed about your ISP’s practices empowers you to make informed decisions about your online behavior.
Some ISPs may offer opt-out options for certain data collection practices. If available, exercise your right to opt-out to limit the data your ISP gathers from your online activities.
Participate in advocacy efforts to promote stronger privacy regulations and legislation. Engaging with lawmakers and supporting organizations that champion internet privacy can contribute to meaningful changes in data protection policies.
Legal and Regulatory Requirements
The data collection practices of ISPs are subject to legal and regulatory frameworks that vary by country. Some countries may have stringent data protection laws that require ISPs to obtain user consent or anonymize collected data. However, other regions may have fewer restrictions, allowing ISPs to retain and use customer data for longer periods.
Data Retention Policies
ISPs often have data retention policies that dictate how long they keep user data in their systems. Retention periods can vary significantly, ranging from a few days to several years. While data retention helps ISPs with troubleshooting and customer support, it can also create potential risks if this data falls into the wrong hands or is misused.
Internet Privacy Laws Worldwide
Different countries have implemented various legal frameworks to address Internet privacy concerns and regulate how Internet Service Providers (ISPs) collect and handle user data. Let’s take a closer look at internet privacy laws in different countries and the international efforts aimed at safeguarding user privacy in the digital realm.
1. European Union – General Data Protection Regulation (GDPR)
The GDPR, implemented in 2018, is one of the world’s most comprehensive and far-reaching internet privacy laws. It applies to all EU member states and governs the processing and handling of personal data by companies and organizations, including ISPs. The GDPR emphasizes user consent, data transparency, and the right to access and delete personal information. ISPs operating in the EU are required to adhere to strict data protection principles, ensuring a higher level of privacy for users.
2. United States – Various State and Federal Laws
The United States has a patchwork of internet privacy laws at the state and federal levels. Some states, like California, with its California Consumer Privacy Act (CCPA), have introduced privacy laws that provide certain rights and protections to consumers, including their internet data.
At the federal level, various laws and agencies regulate specific aspects of internet privacy, such as the Children’s Online Privacy Protection Act (COPPA) and the Federal Trade Commission’s (FTC) enforcement of unfair and deceptive practices.
3. Canada – Personal Information Protection and Electronic Documents Act (PIPEDA)
PIPEDA is Canada’s federal privacy law that governs the collection, use, and disclosure of personal information in commercial activities. It applies to ISPs and other entities that handle personal data. PIPEDA sets out principles for obtaining user consent, limiting data collection, and ensuring data security and accuracy.
4. Japan – Act on the Protection of Personal Information (APPI)
Japan’s APPI was revised in 2020 to strengthen protections for personal data. It regulates how personal information is collected, used, and shared by ISPs and other organizations. The revised APPI introduced stricter penalties for violations and emphasizes user rights in controlling their data.
5. Australia – Privacy Act 1988
Australia’s Privacy Act governs the handling of personal information by both public and private organizations, including ISPs. The Act includes provisions for user consent, data security, and access to personal information. It was amended in 2020 to include the Notifiable Data Breaches (NDB) scheme, requiring organizations to notify users in the event of certain data breaches.
International Efforts to Protect User Privacy
In addition to country-specific laws, several international efforts aim to promote internet privacy and data protection on a global scale. Some noteworthy initiatives include:
1. The Global Privacy Enforcement Network (GPEN)
GPEN is an international network of privacy enforcement authorities from around the world. Its mission is to promote cooperation and information sharing among data protection authorities, leading to a more consistent and effective approach to privacy enforcement globally.
2. The Organization for Economic Cooperation and Development (OECD) Privacy Guidelines
The OECD provides privacy guidelines that member countries can adopt to ensure the protection of personal information while facilitating international data flows. These guidelines help create a common framework for privacy laws and practices across different countries.
3. The United Nations’ Universal Declaration of Human Rights (UDHR)
While not specific to internet privacy, the UDHR upholds the fundamental human right to privacy. It serves as a guiding principle for countries and organizations to respect and protect individuals’ privacy rights, including in the digital realm.
Conclusion
As responsible internet users, it is crucial to be proactive in safeguarding our online privacy. ISPs possess the technical capability to see and collect various types of data about our internet activities, from IP addresses and website visits to search queries and online communication.
This data, if misused or inadequately protected, can potentially compromise our personal privacy, lead to targeted advertising, or even fall into the wrong hands through data breaches.
Yes, your ISP can see your history even if you delete it from your device because the browser you use stores the data of the sites you visit.
No, ISPs cannot see the specific content or data transmitted while users are browsing in incognito or private browsing mode but it does not hide your online activity completely from your ISP.
Yes, an ISP can block a VPN by using techniques like port blocking, deep packet inspection (DPI), IP address blocking, or DNS filtering


No comments were posted yet