PPTP VPN protocol – What is it and How to use it?

Bisma Farrukh
To suggest that tunneling protocols are what stand between hassle-free, secure B2B transactions and complete anarchy is not an exaggeration. As data travels through Virtual Private Networks, these crucial protocols build secure “tunnels” that include encrypted data (VPNs).
Theoretically, they protect private information from prying eyes by wrapping it. However, it isn’t always the case.
Let’s examine PPTP, the Protocol for Point-to-Point Tunneling. How does it work and what is it? Once you know the answers to these queries, you will be able to decide whether or not to use it for corporate security.
Table of Contents
What Is a PPTP VPN Protocol?
PPTP is the most established and widely used VPN protocol. The cornerstone of PPTP is the Point-to-Point Protocol (PPP), which is often utilized for dial-up connections. PPTP converts PPP frames into IP packets and encrypts the data before transmitting it over the Internet.
PPTP enhanced the previous PPP standard, which lacked the tunneling feature. A protocol that was initially only used on Windows PCs quickly spread to other platforms and developed into a standard VPN protocol.
How PPTP Works?
Generally speaking, this protocol was frequently utilized by enterprises to allow customers or staff members to access their company’s servers from their homes over the internet. Today, businesses and individuals looking for a rapid VPN solution both frequently utilize it.
The second (data) layer of the OSI model is where PPTP operates. Transmission Control Protocol (TCP) port 1723 is used for the connection between the two devices (TCP). Together with and for the Internet Protocol, this protocol was developed (IP). TCP provides orderly information packet delivery so that the information is recorded.
After that, the GRE (General Routing Encapsulation) technique is used to create the data packets. Cisco’s GRE tunneling technology enables the encapsulation of a wide range of network-layer protocols into port-to-port virtual links. An IP (internet protocol) network is used for this. Data packets that are sent to and received from the client device and VPN server fundamentally form the tunnel.
General Technical Details About PPTP
- In order to connect to a server, PPTP only needs a username and password in addition to the server address.
- Platform neutrality is extremely high for PPTP connections. Numerous devices and operating systems, including Windows, Linux, macOS, iOS, Android, Tomato, and DD-WRT, are compatible with the protocol.
- PPTP uses GRE (General Routing Encapsulation), IP port 47, and TCP port 1723.
- PPTP uses MPPE and supports encryption keys up to 128 bits (Microsoft Point-to-Point Encryption).
Tunneling Types Supported by PPTP
To establish remote access to Windows PPTP VPN servers, PPTP depends on Microsoft RAS (Remote Access Service). A modem bank can be used by the server administrator as a connecting point for remote users. All RAS-supported connection protocols, including TCP/IP, NetBEUI, and IPX/SPX, can be carried across the connection because PPTP depends on the PPP protocol (more on that later).
The PPTP simply needs the server IP, username, and password to create a connection. In addition, this protocol supports two different PPTP tunneling types:
- Voluntary Tunneling
The client or user starts this kind of tunneling. It may operate without any additional hardware or network equipment, such as a router. The only form of tunneling that will occur when you use VPN services as a customer is voluntary tunneling.
- Compulsory Tunneling
The server, not the client, is the one who starts mandatory tunneling. With forced tunneling, a router and remote access rights are needed for the VPN server to work. The primary purpose of compulsory tunneling is in corporate settings to require that all company devices be secured by the VPN network.
Pros and cons of PPTP VPN protocol
PPTP is one of the oldest and most basic VPN protocols. While it gets the job done by establishing a secure tunnel for your data, it has some limitations you should be aware of.
Pros:
- PPTP is easy to set up and use. It works with nearly all devices and operating systems, so compatibility is high.
- It also requires few resources, so performance impact tends to be minimal.
- PPTP VPNs can be fast, especially for basic web browsing and streaming needs.
Cons:
- PPTP has some security weaknesses. The encryption used, MPPE, has been found to have flaws that make it relatively easy to crack. This means a PPTP connection may not be as private as you want. PPTP also does not support multi-factor authentication for added security.
- Another downside is that PPTP does not mask your actual IP address well. Your VPN provider’s IP is used, which can allow your activity to be tracked back to you. PPTP also cannot tunnel certain types of traffic like P2P file sharing.
- It is considered an outdated protocol with security and privacy flaws.
For most users, a more robust VPN protocol like OpenVPN, IKEv2 or WireGuard is recommended to ensure a truly secure and private connection. These newer protocols offer stronger encryption, IP masking, multi-factor authentication support and better tunneling of all traffic types. However, they tend to be more difficult to set up and may impact device performance more. So the decision comes down to balancing ease of use with security and privacy needs.
What is PPTP Passthrough?
PPTP necessitates a VPN Passthrough to connect, just like other outdated protocols like IPSec and L2TP. Data packets from VPN clients can “pass through” routers thanks to a router function called VPN Passthrough to reach the VPN server.
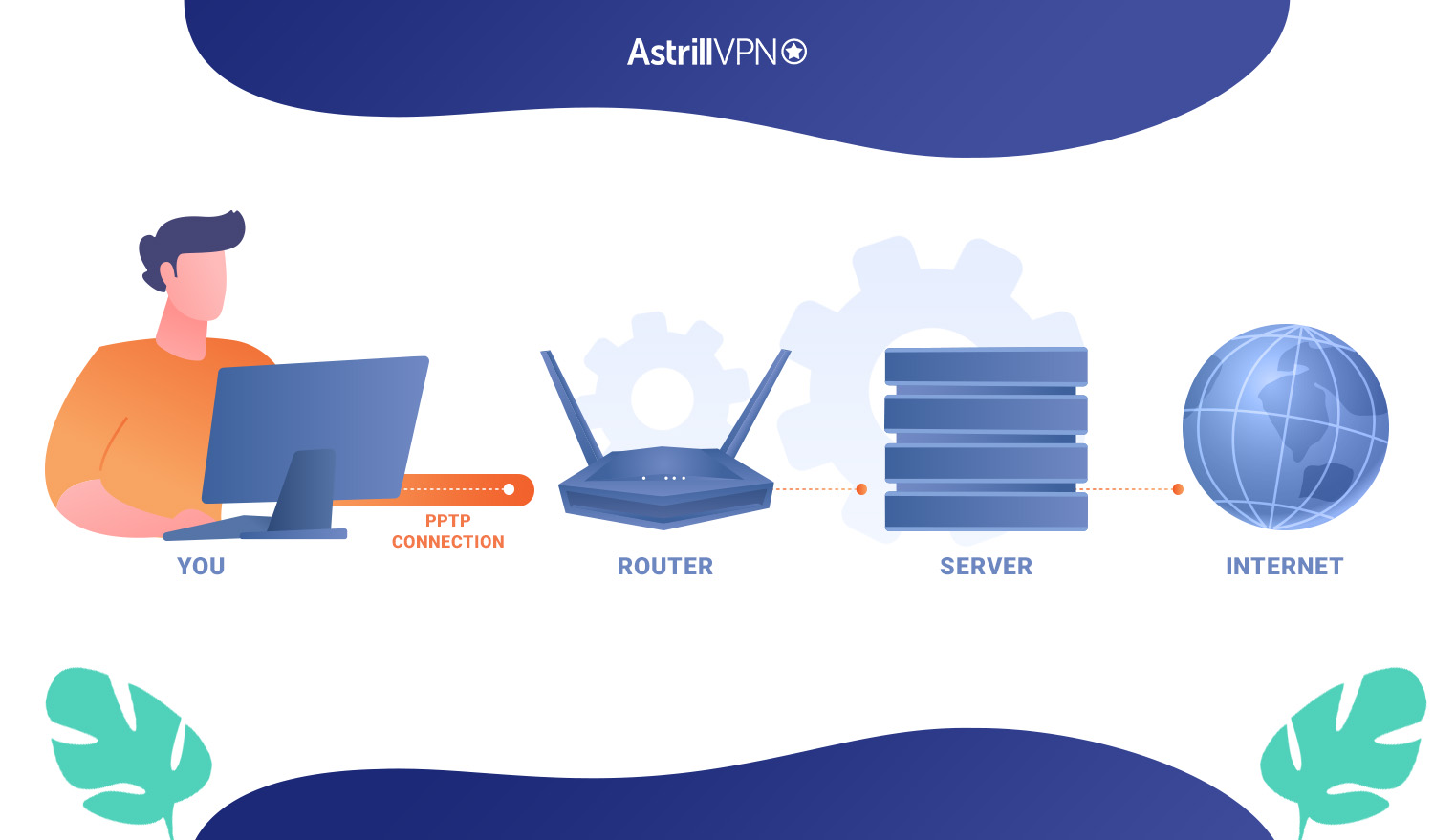
The aforementioned protocols require the VPN Passthrough feature because they don’t naturally work with NAT (Network Address Translation). Thanks to NAT, all devices on a single network can share a single internet connection and IP address. As a result, to connect to a PPTP VPN server, the used router needs to have the Passthrough feature.
You can enable or disable passthrough options in your router’s settings. You must accomplish this by entering your IP address, which for most routers is 192.168.1.1, in the browser’s URL bar. Typically, the Passthrough feature of each protocol will have a unique toggle button.
Click “Enable” for PPTP Passthrough to enable the use of a VPN client for PPTP connections, and you’re ready to go.
Why is PPTP beneficial?
Easy to Set up:
Since PPTP does not use data encryption, the setting is straightforward. It is not essential to install public key infrastructure or computer certificates. The procedure is, therefore completely user-friendly.
Ease of use:
Because of its age and ease of usage, PPTP should be used by everyone who values effectiveness and speed. Because PPTP has been around for more than 20 years, it won’t affect the performance of even the oldest, slowest current machine.
Compatibility:
PPTP is supported by the majority of modern computers because it is the de facto standard for a basic encryption protocol. Anyone who has even a basic understanding of technology may quickly and easily set up PPTP.
As we mentioned in the first point, PPTP does not use data encryption which means it can be harmful for data security. So, regardless of the above benefits, the use of it with the latest demands of security may not be a wise choice.
PPTP Encryption
Data is encrypted via MPPE in PPTP. Cybercriminals employ MPPE’s numerous documented vulnerabilities to launch bit-flipping, brute-force, and DDoS (Distributed Denial of Service) attacks.
Since most cybercriminals and governments are now aware of PPTP’s security flaws, it is a simple target for attacks and surveillance operations. Stay away if you have any concerns about your safety.
There could be ways to increase the security of current PPTP implementations in certain situations. You may, for instance, move from MS-CHAP to EAP-TLS (Extensible Authentication Protocol). This employs a certificate-based mechanism to authenticate data using Public Key Infrastructure (PKI).
First, MS-CHAP-v1 (Microsoft Challenge-Handshake Authentication Protocol) can be used by PPTP to confirm that it is connecting to the right devices. However, MS-CHAP-v21 is no longer secure. A CHAP exchange can be used by cybercriminals to extract NT Password hashes.
Once they acquire the password hashes, they can fully decrypt your traffic using a Data Encryption Standard (DES) cracker. Cybercriminals currently have unrestricted access to anything you do online, and they have simple access to your accounts and personal information.
PPTP compatibility
As Microsoft incorporated PPTP into its products, it became the choice of many people. Not only are Windows computers frequently pre-installed with the protocol, but also Mac, Android, Linux, and iOS devices are frequently so as well.
Those looking for a quick and easy VPN service used their most convenient choice, PPTP. Unfortunately, despite having certain advantages, it is no longer the best choice, despite still having some advantages.
PPTP VPN setup
In addition to speed, PPTP’s strength rests in its simplicity of configuration and setup due to the protocol’s native support across a variety of operating systems. Downloading the client and entering the credentials provided by the VPN provider constitutes the installation process.
Although PPTP was first designed for Windows, PPTP VPN clients are now available for Linux and iOS. You won’t need to fiddle with any other options when connecting to PPTP servers; all you’ll need is the server address, username, and password.
However, PPTP VPN’s security is still questionable and in the digital age of today, encryption is most significant. So, companies with a huge amount of data to manage need secure VPNs like Astrill VPN services. It is not only secure but also offers several features such as a kill switch, split tunneling, ad blocker, DNS leak test and a lot more. You can view its pricing plans here.
PPTP comparison with other Protocols
Let’s compare it with other protocols.
PPTP vs OpenVPN
When it comes to choosing a VPN protocol for your needs, two popular options are PPTP and OpenVPN. Both offer encryption and anonymity for your online traffic, but they differ in key areas.
Point-to-Point Tunneling Protocol is an older VPN protocol that is still widely used. It is built into Windows operating systems by default, so it is easy to configure. However, PPTP has some weaknesses. The encryption it uses is relatively weak by today’s standards, making it more vulnerable to hacking. PPTP also has issues with speed, performance, and reliability. Connections can drop unexpectedly or have latency issues.
OpenVPN is a more modern, open-source VPN protocol that offers stronger security and better performance. OpenVPN uses AES-256 encryption, the current gold standard for VPN security. AES-256 is virtually unbreakable with today’s computing power. OpenVPN also tends to be faster than PPTP and more stable, with fewer connection drops. It works across multiple operating systems like Windows, Mac, Linux, Android, and iOS.
The downside to OpenVPN is that it requires additional software and configuration. It is not built into operating systems by default like PPTP. However, once setup, OpenVPN tends to “just work” reliably in the background.
PPTP vs IKEv2
PPTP and IKEv2 are two popular VPN protocols with some key differences. PPTP is an older protocol while IKEv2 is newer and more secure. PPTP transmits data unencrypted which makes it less secure. It relies on weaker encryption algorithms like MPPE that can be cracked. PPTP is also known to have issues with compatibility and speed stability.
IKEv2 or Internet Key Exchange version 2 is a newer VPN protocol developed by the IETF. IKEv2 offers stronger encryption methods like AES-256 and uses two-factor authentication for added security. It also has better compatibility with different devices and operating systems. IKEv2 has a more stable connection with higher speeds and lower latency.
While PPTP is an easy-to-use protocol, it lacks security and stability compared to IKEv2. If security is the main concern, IKEv2 is the better choice due to its stronger encryption, two-factor authentication and more robust design. However, IKEv2 can be harder to configure for beginners. If ease of use is more important, PPTP may be sufficient for basic needs as long as you don’t transmit sensitive data. But for optimal security, reliability and speed, IKEv2 is the better VPN protocol.
PPTP vs L2TP
PPTP and L2TP are both VPN protocols that allow you to securely connect to a private network over the public Internet. They differ in how they encrypt data and establish connections.
PPTP, or Point-to-Point Tunneling Protocol, was one of the earliest VPN protocols developed. It uses basic encryption to encrypt data that travels between your device and the VPN server. While easy to set up and use, PPTP’s encryption has been criticized for being insecure. This means a hacker could potentially intercept your data while you’re connected to a PPTP VPN.
L2TP or Layer 2 Tunneling Protocol was created as a more secure alternative to PPTP. It uses stronger encryption methods, making intercepted data much harder to decrypt. L2TP also authenticates users before establishing a connection, adding an extra layer of security. However, L2TP is often used together with IPSec, another VPN protocol, to provide the strongest encryption.
L2TP is generally considered the more secure VPN protocol compared to PPTP. While PPTP is easier to configure, its weak encryption makes your data and online activity more vulnerable when using a PPTP VPN. So for most users seeking a secure VPN connection, an L2TP or L2TP/IPSec VPN is recommended over PPTP. The added security of L2TP typically outweighs its slightly more complex setup.
FAQs
- What is the internet connection type for PPTP?
A technique for setting up virtual private networks is the Point-to-Point Tunneling Protocol (PPTP). PPP packets are encapsulated by PPTP using a GRE tunnel and a control channel via TCP. Virtual private networks are supported by the tunneling protocol known as L2TP, or Layer 2 Tunneling Protocol (VPN).
- What kind of encryption with a 40-bit key is utilised for dial-up and PPTP-based VPN connections?
This 40-bit session key is generated using the RSA RC4 standard based on the client password. The remote connection is kept private and safe by using this key to encrypt all data sent over the Internet. PPP packets contain encrypted data.
- Is PPTP a TCP or UDP?
PPP packets are encapsulated by PPTP using a Generic Routing Encapsulation tunnel and a TCP control channel. Several types of UDP are used by many contemporary VPNs to provide this similar job.
- Does PPTP use TCP?
IP protocol 47 Generic Routing Encapsulation and TCP port 1723 are used by the Point-to-Point Tunneling Protocol (PPTP) (GRE). Through the Internet, PPTP offers a low-cost, private connection to a corporate network.
- Can we consider PPTP the same as L2TP?
While L2TP has poor speed but robust encryption, PPTP offers high-speed but weak encryption. PPTP, the first VPN protocol ever supported by Windows, provides simple encryption but requires a quick internet connection. While L2TP has the highest level of encryption, it also results in slower internet speeds.
- What is PPTP used for?
PPTP is used to access intranets (the internal network of a corporate office building) as well as the internet.
PPTP is one of the quickest VPN protocols because of the lower encryption standard.
- Is PPTP tunneling used for protocol?
Yes. To create VPN tunnels between open networks, a network protocol known as Point-to-Point Tunneling Protocol (PPTP) is employed. PPTP servers are often referred to as Virtual Private Dialup Network (VPDN) servers. PPTP is preferred over other VPN protocols because it is quicker and mobile-friendly.
Conclusion
No doubt, PPTP is one of the fastest VPN protocols. As a VPN protocol, it ought to enable safe online access to hosts, servers, and other resources on a private network. Sadly, this protocol is one of the oldest ones still in use. It may not be obsolete till now, but as technology ages, security demands vary with time. It might have been helpful back then. However, it contains several weaknesses according to today’s security requirements. Therefore, it is unfit for any situation that is facing a threat.
Avoid using antiquated protocols like PPTP if you need to build a VPN. Utilizing contemporary VPN protocols of Astrill VPN will make you a lot safer. As the Astrill VPN secures you by using OpenWeb, StealthVPN, WireGuard, and OpenVPN. So, rest assured, your safety is always intact with it. If you love this piece of content, don’t forget to share it with your family and friends!

No comments were posted yet