What is Tor and is Tor browser safe to use?

Bisma Farrukh
When discussing dark web browsing, Tor is the first browser that springs to mind. Tor is growing in popularity among millions of people worldwide with the passing years. It has been synonymous with anonymous browsing during the last few years. As people’s concerns about online privacy rise, questions like is tor browser legal? What can be done with Tor? And is tor browser safe? If you are looking for the answers to the same questions, let’s find out.
Table of Contents
What is Tor?
To provide genuinely private web browsing, web traffic is anonymized using Tor (The Onion Router). To hide your IP address and browsing habits, the Tor Browser reroutes online traffic across several routers known as nodes. Tor is used by journalists, whistleblowers, and others who want to protect their online privacy since it hides browsing activity and turns off tracking.
How does the tor browser work?
Web traffic is encrypted and rerouted through Tor’s onion network using onion routing. Your online traffic is routed through a series of network nodes known as onion routers. However, your data is protected by many layers of encryption. Each router (or node) “peels away” a layer of encryption for the data to reach its destination fully decrypted.
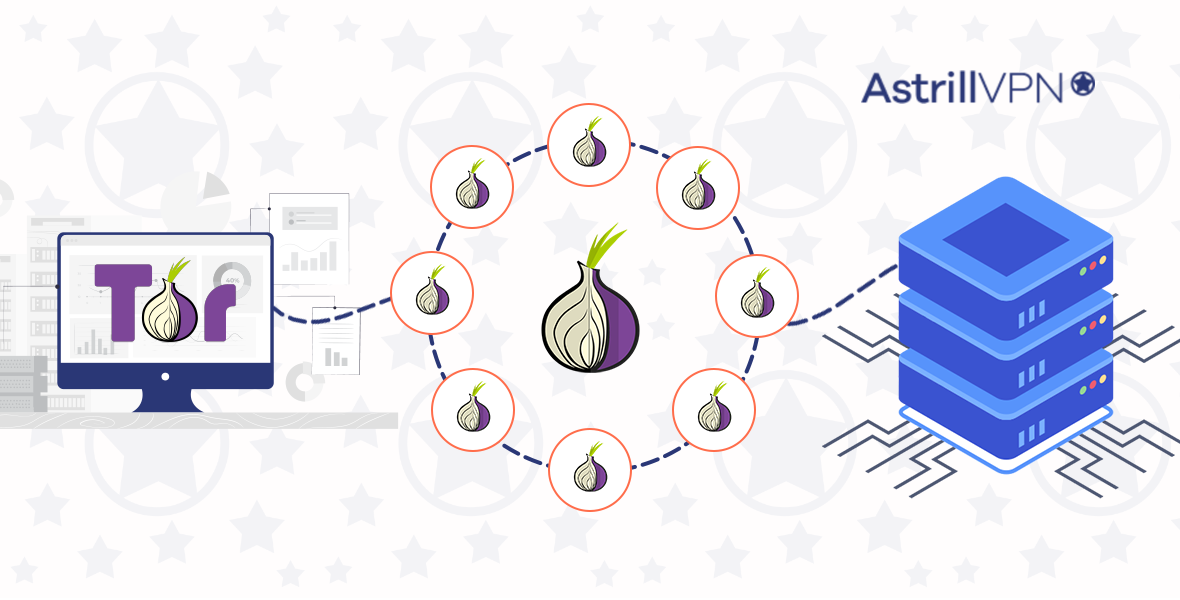
Encrypted data is sent anonymously through the three layers of global proxies that make up the Tor circuit.
Let’s examine the three types of network nodes in more detail:
1. Entry/Guard node:
A random entry node is the first node that Tor Browser connects to. Your data is introduced into the Tor network by the entry node.
2. Middle node:
Your data is entirely encrypted here. The data is then routed through several nodes that gradually decrypt it. Each middle node only knows the identities of the intermediate nodes that come before and after it, maintaining anonymity.
3. Exit node:
After the last layer of encryption has been removed, the decrypted data leaves the Tor network via an exit node and proceeds to its final server destination.
Yes, it does sound complicated, and it is complex in different ways. Still, using the Tor browser isn’t rocket science; it’s surprisingly easy and user-friendly.
Features of Tor browsers
The Tor Browser lacks several typical browser functions due to its privacy-first design and isn’t the most feature-rich browser (e.g., device sync). The Tor Browser is compatible with Firefox’s add-on collection because of its Firefox foundation.
Although Firefox’s add-on library is less extensive than Google’s, most users still have plenty of options.
- Two add-ons are activated by default: NoScript and HTTPS Everywhere. If HTTPS and HTTP are available, the former will compel websites to resolve their connection using HTTPS. Except for code from websites you trust, the later plugin automatically disables all JavaScript code (and other content).
- It uses the same PDF reader as Firefox. It provides a straightforward user interface with all the usual controls for page layout, navigation, and document interaction. The PDF reader has settings for viewing individual attachments, layers, and the document outline, in addition to a side panel showing thumbnails of each page in a vertical orientation.
All in all, you can surf around using Tor and be safe if you use it with the VPN. So, learn more, install and browse accordingly.
What is the Tor Browser Used For?
Every layer of the internet, including the dark web, may be accessed with Tor Browser. Its several layers such as surface, deep web, and dark web with onion websites and all these are accessible with Tor Browser. You may still access popular websites from the surface web, such as YouTube and Wikipedia because Tor is built on Firefox or Chrome. Tor can access onion sites on the dark web, unlike conventional browsers.
The most contentious and scary area of the internet is the dark web. You run the danger of unintentionally discovering disturbing or illegal material, such as human trafficking, drug or weapon trades, and more because it is not monitored.
This explains why using The Onion Router to reach the dark web has a negative reputation. It is frequently portrayed as a location where criminals congregate and converse covertly.
Pros:
- Excellent privacy and security.
- Utilizes Firefox add-ons.
Cons:
- Slow and erratic speeds.
- Rogue nodes cause security problems.
- Tor users can’t access some websites.
Advantages of Using Tor
Tor offers several key benefits for users who value privacy and anonymity online. Here are some of the main advantages of using the Tor network:
Privacy and Anonymity
Tor routes your internet traffic through a series of relays run by volunteers all around the world. This means your traffic is encrypted and bounced through multiple nodes, obscuring your actual IP address and location. This makes it difficult for anyone observing your network traffic, like your internet service provider or a hacker, to identify you or track your online activity. Tor helps protect your privacy and keep you anonymous while browsing the web.
Circumvent Censorship
Since Tor encrypts your traffic and hides your true IP address, it can help you circumvent censorship from repressive governments that try to block certain websites. If a government blocks access to a website, you may still be able to access it through the Tor network. This makes Tor a valuable tool for activists, journalists, and citizens in countries with heavy internet censorship.
Access the Dark Web
While most people use Tor for legitimate purposes, it also enables access to the dark web, the part of the internet that exists on encrypted networks and is not indexed by search engines. The dark web includes hidden sites used for illegal activities and the sale of illicit goods. However, the Tor network itself is not illegal and simply provides the anonymity needed to access these dark web sites.
Those are some of the key benefits and advantages that Tor offers through its anonymous network and encryption technology. Tor can be a useful tool for those seeking privacy and anonymity online, but it also comes with some risks that users should be aware of.
Disadvantages of Using Tor
Slow Connection Speed
One of the major drawbacks of using Tor is the slow connection speed. Since your internet traffic is routed through multiple nodes before reaching its destination, it takes more time for data to travel through the network. This means that everyday tasks like loading webpages, streaming videos, and downloading files will be noticeably slower when using Tor. The slow speed can become frustrating for users who depend on fast internet for their work or entertainment.
Security Risks
While Tor aims to enhance privacy and anonymity, it is not immune to security risks. Hackers and bad actors also use the Tor network to carry out illegal activities anonymously. This means there is a higher risk of encountering malware, phishing scams, and other threats when browsing the web using Tor. Tor’s anonymity features make it difficult for network administrators to filter out malicious traffic. So users need to practice caution and have proper security software when using Tor.
Government Surveillance
Governments and intelligence agencies around the world consider Tor a tool for criminals and terrorists. As a result, they actively monitor Tor traffic to identify potential threats. While Tor’s encryption and anonymity network make it difficult for mass surveillance, government agencies have found ways to deanonymize and track certain Tor users.
This means there are limitations to the anonymity that Tor provides, especially against well-resourced actors like governments.
Those are some of the major disadvantages of using the Tor network in terms of speed, security and anonymity. While Tor aims to provide privacy and censorship resistance, users need to weigh the trade-offs and risks against the benefits for their specific needs and threat models.
Is tor illegal in the US?
The US has legalized Tor. The mere fact that you use the Tor browser will likely avoid getting you into trouble. You cannot use this browser for unlawful activity, though, as Tor is not an ungoverned area. You violate the law if you use Tor to purchase narcotics or weapons.
How do people use TOR?
Tor is a free software that allows users to improve their anonymity and privacy online. It does this by routing internet traffic through a network of relays run by volunteers from all over the world. This makes it difficult for anyone observing the Tor network to track users’ locations or identities.
- People use Tor for many reasons, but the main ones are to keep their browsing habits private from advertisers, websites, internet service providers, and even governments. Tor is especially useful for people who live in countries with censorship and internet surveillance.
- When you use Tor, your internet traffic is encrypted and passes through multiple relays before reaching its final destination. This makes your browsing activity untraceable to anyone observing your connection, whether that’s your ISP, a corporate network administrator, or a government agency.
- While Tor does provide anonymity, it is not a magic cloak of invisibility. Your level of anonymity depends on how you use it. Simply using Tor does not fully hide your identity, so you still need to practice good “net hygiene. For the highest level of anonymity, you should avoid logging into accounts while using Tor and refrain from sharing any personally identifying information.
People use Tor to improve their privacy and anonymity online. This allows users to access blocked content, communicate secretly, and protect themselves from pervasive internet tracking and surveillance. As with all security tools, Tor is most effective when used correctly and with an understanding of its limitations.
How can I access TOR?
There are a few easy ways to access and use TOR, the anonymity network that allows you to browse privately and securely on the internet.
- The simplest method is to download and install the TOR Browser by visiting https://www.torproject.org/ . The TOR Browser is free, open source software that routes your web traffic through a worldwide network of relays to conceal your location and usage from your ISP and websites you visit.
- You can download the TOR Browser for Windows, Mac, or Linux from the TOR Project website. Once installed, the TOR Browser functions similarly to Chrome or Firefox where you can browse the open web anonymously.
- For even more privacy and security, you can route your entire internet connection through TOR instead of just your web browser. To do this, you will need to install TOR software on your device and configure it.
- The TOR software acts as a proxy that intercepts your internet traffic and routes it through the TOR network before accessing the final destination. You can install TOR software and configure it manually or use a preconfigured package like Tails, a Linux distribution designed to be used from USB or DVD.
Whichever method you choose, using TOR can help provide you a more secure and private web browsing experience. Just keep in mind that total anonymity is impossible to achieve, and you should still exercise caution online regarding what information you share. But the extra layers of privacy that TOR provides can help prevent others from learning your physical location or browsing habits based solely on your IP address.
Which Risks Do I Face When I Use Tor?
The reality is that Tor is only partially secure. It contains flaws, just like any other system.
Although leaks are frequently corrected, you can never be sure that these fixes are applied promptly. In addition to this, there are other causes for concern regarding Tor’s level of security. Here is a couple.
- Hackers can target tor users:
To begin with, hackers frequently target Tor users. Usually, Tor isn’t to blame for this. Instead, there are other security loopholes in the user’s device that needs to be addressed. Everyone should be aware of this since it could happen to them. When you browse the dark web, criminals, viruses, and other harmful content can track you on the websites you visit. As a result, it’s crucial to think carefully before clicking.
- You can be tracked online:
Another risk is that even when utilizing Tor, you might still be followed online. Bad exit nodes are one scenario where this may occur. Tor is unable to block tracking at the entrance and exit nodes of its network. The entry node’s owner and the operator will be able to see your actual IP address.
How to be safe when using the Tor browser?
The foremost solution to this problem is to use a VPN. For most individuals, safety hazards frequently outweigh the advantages of the browser because serious flaws could jeopardize their safety and privacy.
Instead, if you’re a casual user, we advise pairing a secure private browser with our VPN software. AstrillVPN has excellent features, like VPN leak test, DNS leak test, and Password leak test, to keep you secure beyond your imagination. Subscribe to AstrillVPN by selecting one of its plan that suits you best and enjoy true online privacy and security.
What are the safety benefits of using Tor?
There are several reasons to use the Tor Browser to strengthen your security, even though there are some risks (no more significant than those of ordinary browsers):
- Since it is free, using Tor is far superior to using a free proxy or free VPN;
- It is simple to use: all you need is the Tor Browser, which is 1) cost-free, 2) not particularly difficult to use compared to other browsers, and 3) instructs you on how to use it;
- It’s more challenging to compromise since Tor’s network is decentralized and your circuit is constantly changing.
- Your data is encrypted by Tor, which hides your browser activity from your ISP and masks your IP address.
Faqs
- Is it safe to use tor without a VPN?
Tor is still entirely secure on its own, making it impossible for anyone to identify an individual Tor user. Using a fast VPN and Tor together can help prevent any of the nodes from seeing your IP address.
- Is tor safe to use on iPhone?
For iOS devices, the Onion Browser is available in the App Store. Mike Tigas, the leading developer of the Tor Browser, created this open-source application. Using Tor on an iPhone or iOS device is riskier than using it on other devices, even with caution. The app’s JavaScript feature cannot be turned off.
- Can you be tracked on Tor?
Your ISP can still know that you’re connected to Tor even though Tor encrypts all of your internet data. Additionally, Tor cannot block tracking at its network’s entrance and exit nodes. The entry node’s owner and the operator can see your IP address.
- Is the Tor browser safer than Chrome?
Tor has a “signature” or “fingerprint,” and you can identify its users by looking at their internet usage. Certainly, yes. Tor browser is safer to use than chrome.
Bottom line
Hopefully, you got the answer; how secure is tor? Sadly, Tor is not a practical option for regular use. Since of the network’s volunteer structure, connections are of varying quality, and Tor Browser is slow because it must hop between three nodes.
However, there are methods to improve it if you’re utilizing it for good reasons that call for safety, such as using a VPN software.


No comments were posted yet