The Wacatac Trojan virus can cause severe damage to your device and compromise your data if action isn’t taken. This virus specifically targets Windows devices; once it enters your device, it can compromise sensitive and confidential data. Suppose you suspect your computer device has been infected with the Wacatac malware. In that case, you must remove it from your device immediately before any further damage is done. This guide is your one-stop shop for learning about the Wacatac trojan, how to detect it, and the most effective ways to remove it from your device.
Table of Contents
What Is The Wacatac Trojan?
The Wacatac trojan virus, also called Wacatac.b!ml or Trojan:Win32/Wacatac, is malware that infiltrates computer devices and performs various malicious actions. It pretends to be legitimate software but injects your device with malware to steal and compromise your data. Wacatac trojan malware can cause extensive damage. For fraud and identity theft, it can collect sensitive and confidential information, such as your logins, passwords, and financial details. Unfortunately, once the Wacatac trojan infiltrates your device, it can also record your keystrokes and steal your personal information, like your login credentials and Personally Identifiable Information (PII).
Trojan-type viruses like Wacatac malware also cause “chain infections” as they infiltrate computers and inject them with other malware, such as ransomware crypto miners. Ransomware infections are specifically created to encrypt data and only decrypt it unless the victim pays a specific ransom. Once your device is infected with malware, restoring it can sometimes be challenging, which is why their lingering presence can lead to permanent data loss.
Trojans can also introduce browser hijackers and adware, which can be annoying and disruptive, causing unwanted pop ups and advertisements. Trojans can also be used as Remote Access Tools (RATs), enabling cybercriminals to control hijacked devices. Cryptominers can also use infected devices to mine cryptocurrencies, and since this process consumes system resources, the computer hardware gets overheated, and the computer system can get permanently damaged. To put it simply, trojan-type infections like Wacatac malware can invade privacy, cause data loss, cause financial loss, and cause other issues.
How Did The Wacatac Trojan Get On Your PC?
One of the trickiest aspects of the Wacatac trojan is that it can’t be detected easily. You may never even realize your device is infected with the Wacatac trojan virus until it’s too late. However, there are some root causes for your device being infected with the Wacatac virus. Once you’re aware of the causes, you can take steps in the future to potentially avoid getting infected with the virus. Some of the ways your PC got infected with the Wacatac trojan virus include:
- The Wacatac virus can get distributed through phishing emails that contain suspicious attachments. Once you open these attachments, they inject malware into your device.
- You’ve downloaded and installed free software from untrustworthy and unknown third-party sources. Software from these sources can also come with bundled malware, including trojans like Wacatac.
- The trojan exploited vulnerabilities in outdated or unpatched software on your PC, allowing it to get injected into your device.
- Visiting malicious websites can result in drive-by downloads, which allow trojans to be automatically downloaded and installed without your consent.
- You clicked on a malicious ad or popup, thinking it was legitimate, but it infected your device with malware.
- You’ve downloaded fake updates for legitimate software, and this results in the installation of the malware.
- You might have inserted infected USB drives and removable media into your PC, introducing the trojan to your device.
How To Remove The Wacatac Trojan From Your Device?
The Wacatac trojan virus can cause a lot of damage to your devices. Therefore, it’s necessary to remove them from your device. Although removing the trojan isn’t easy, implementing some of the steps mentioned in this section is still possible. So brace yourself because if you’re wondering how to remove the Wacatan trojan virus, all you have to do is follow these steps:
1) Remove The Wacatac Virus With Antivirus Software
Installing reliable antivirus software is one of the easiest ways to remove the Wacatac virus. The software will detect real-time threats and immediately remove them from your device. Effective antivirus software like Bitdefender, McAfee, Norton and Avast One which are among some of the best will continuously scan for emerging threats in real-time and remove them from your device. When choosing antivirus software, you must ensure it meets specific criteria to do its job effectively. Some essential factors you need to consider include:
- It can effectively detect and remove any threats in real-time.
- It offers multiple layers of security, from email scanning, web protection and firewall integration.
- It has a high detection rate for malware and viruses.
- The software should not significantly slow down your computer’s performance or consume much of the system’s resources.
- The software should be user-friendly and intuitive and even work for someone who isn’t tech-savvy.
- It should be easy to set up and not require much technical knowledge.
- It should offer efficient customer support, including the ability to contact them through different modes of communication, such as email, phone, and live chat.
- The antivirus software should be compatible with various operating systems, including iOS, Android, Windows, macOS, and Linux.
- The software company does not share your personal data without your consent. Be sure to check the antivirus software’s privacy policy before purchasing it.
2) Remove The Wacatac Virus Manually On Windows
Besides investing in reliable antivirus software, you can manually remove the virus on your Windows device. Remember that the Wacatac trojan virus is more susceptible to infiltration on Windows devices, so you must take extra steps to ensure your Windows device remains protected. Here’s how you can manually remove the virus from your PC:
- Go To Task Manager
If you detect malware on your device, the first step is to stop the process of malware on your computer. You can do this by going to the Task Manager on your PC.
- Click the Windows icon on the bottom left of your PC and then search for the Task Manager.
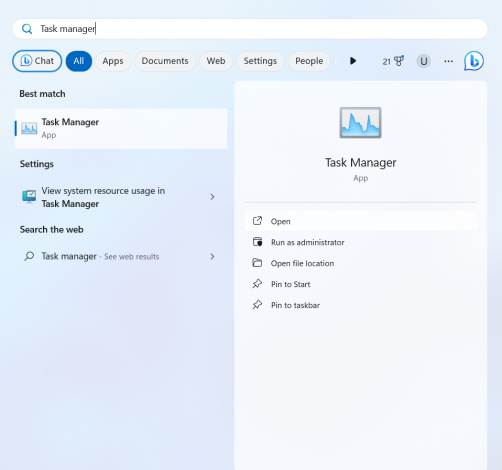
- Once you’ve entered the Task Manager, click on any suspicious-looking programs you don’t remember installing, or that appear sketchy.
- Once you find the apps, click on them and select End task. They will be removed from your device.
- Put Your PC On Safe Mode
Another way to remove malicious software from your device is first to put your PC on Safe Mode and then remove any dangerous apps from your device. Trojans like the Wacatac virus can cause further damage to your devices by installing different types of software without your consent. So, put your PC on Safe Mode and remove any suspicious programs from your device. Here’s how you can do it:
- Press the Windows logo key + R.
- Type msconfig in the Open box and then select OK.
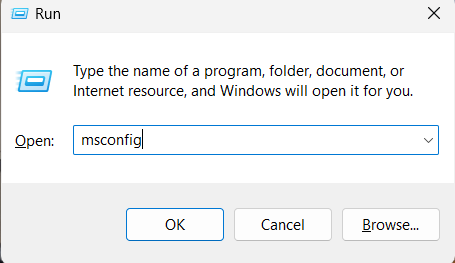
- Select the Boot tab.
- Under Boot options, clear the Safe boot checkbox.
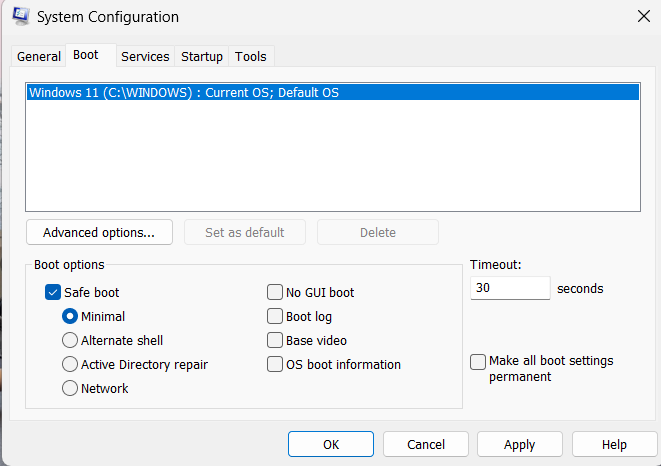
- You will then be prompted to restart your computer. Confirm and click on Restart.
- Once you’re back, go to Settings by going to the search bar.
- On the left side, click on Apps and then click Installed Apps.
- Look for any suspicious programs that you don’t ever remember installing.
- If you find a malicious app, click on the three-dotted line and select Uninstall.
3) Reset Your Browser Settings
Another way to effectively remove malware from your device is to reset your browser’s settings. This is important because if your device has a virus, browser hijackers and adware could lurk in the background, waiting to steal your sensitive and confidential data. Resetting your browsers ensures that adware and browser hijackers are effectively removed from your device. Here’s how you can reset your browsers:
Reset Google Chrome
Here’s how you can reset Google Chrome:
- Go to Chrome, and click the three-dotted menu in the top right corner.
- In Settings, click Reset settings.
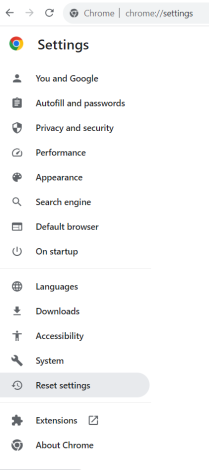
- Then click Restore settings to their original defaults.
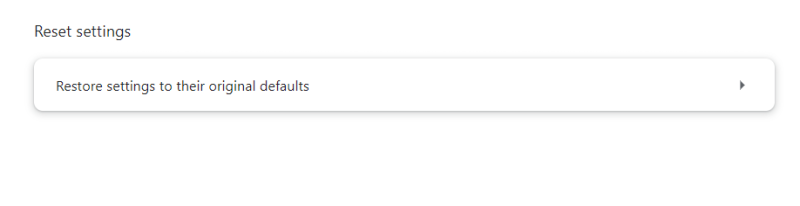
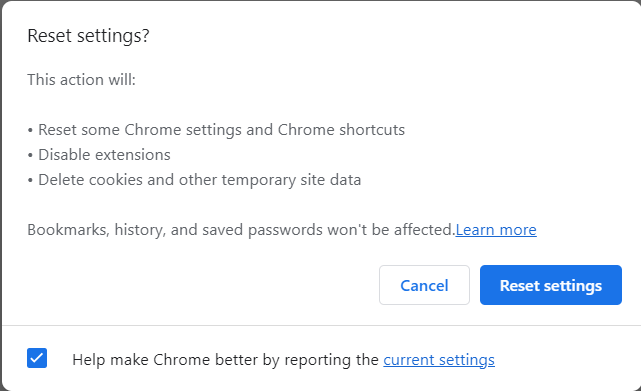
- You will then receive a Reset settings verification screen that explains what the reset does. Once you’ve agreed, click the Reset settings button.
Reset Mozilla Firefox
Here’s how you can reset Firefox to its default settings:
- Go to Firefox and click the three-dotted menu.
- Click Help and then click More troubleshooting information.
- Click Refresh Firefox, and then confirm by clicking the Refresh Firefox button in the window that pops up.
- Once the process is complete, click Finish.
Reset Microsoft Edge
Here’s how you can reset your Edge browser:
- Click the three dots at the top right corner of the screen.
- Click Settings.
- After that, click Reset Settings on the left menu.
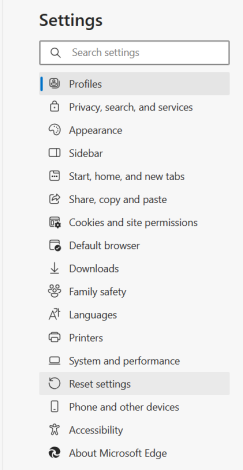
- Click the Reset settings to their default values box.
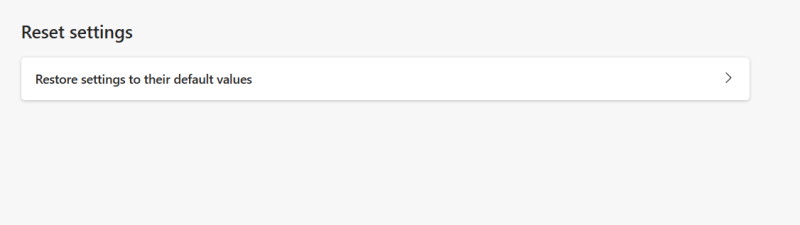
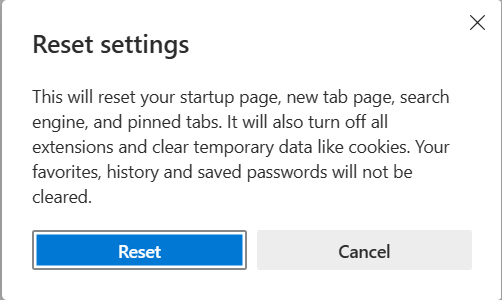
- Confirm Reset by clicking the Reset button. That will enable Edge to reset completely.
Reset Safari
Here’s how you can reset the Safari browser:
- Save all your work and then exit Safari.
- Open Finder, then select Go > Go to Folder from the menu bar. Then, visit the ~/Library/Preferences/ directory.
- Search for com.apple.Safari.plist file and delete it.
- Return to the Go to Folder box and visit ~/Library/Safari/. Delete each item from the folder except for the Bookmarks.plist file.
- Visit ~/Library/Containers/, search for Safari, and then delete all files and folders that appear in the search results.
- Open Safari and visit its Preferences pane to reactivate necessary extensions.
4) Update Your Window’s Software
Keeping your Windows up to date ensures that you will be equipped with the latest security patches, keeping your PC safe and secure from malware and viruses. You need to enable automatic updates to ensure that you have 24/7 protection. Here’s how you can update your PC:
- Click the start icon, and go to Settings.
- Go to Windows Updates and switch the toggle to on.
- You can also turn on the option “Get the latest updates as soon as they’re available.”
- This ensures that your device remains updated and protected from malware and viruses.
How To Determine If The Wacatac Trojan Virus Isn’t A False Positive?
So you’ve scanned your PC with Windows Defender, and a pop-up window states that one program on your device has the virus Wacatac.B!ml. The Wacatac trojan virus is malware that Windows Defender Security protects you from by default. However, if you’re continuously alerted regarding its presence, it’s a surefire sign that the virus alert is a false positive.
You can prove this by downloading the Microsoft Safety Scanner and scanning your PC. If it’s not detecting Wacatac, then you can be sure it is a false positive. You can remove that false positive by deleting Wacatac from Defender’s Protection History. You can do this by following these steps:
- Open File Explorer and check the “Hidden Items” box on the View Tab.
- Then navigate this path C:\ProgramData\Microsoft\Windows Defender\Scans\History\Service.
- Open the Service folder, and if you find a folder called Detection History, delete it. The false notification regarding Wacatac will end.
What Additional Steps Can You Take To Protect Your Device From Viruses?
You can take additional steps to get rid of trojan:win32/wacatac.b!ml malware and other nasty viruses to ensure your devices remain protected and your sensitive and confidential data is never compromised. Here are a couple of things that you can do:
1) Use AstrillVPN
AstrillVPN encrypts your internet traffic and masks your IP address, ensuring that malicious actors and third parties cannot intercept your online activities. Although AstrillVPN will not necessarily protect you from viruses, it will ensure that your online presence remains safe and secure. AstrillVPN has many excellent security features, including a Kill Switch feature, Smart Mode, DNS leak detection, AES 256 encryption, and robust encryption protocols like StealthVPN, OpenVPN, and Wireguard. This assures you that even if your device gets malware, your data online remains safe and secure.
Public networks are also the most vulnerable to cyber-attacks and malware attacks. Hence, using AstrillVPN ensures that your sensitive and confidential data remains safe and protected when using a public network. AstrillVPN also adheres to a strict No Logs policy, ensuring that all your data and browsing sessions get deleted as soon as you log out of the VPN provider.
Protect Your Data from Online Scams with AstrillVPN
Get AstrillVPN Now2) Be Cautious Of Phishing Scams
Phishing scams are some of the easiest ways for users to get malware injected into their devices. They’ll get emails and messages from someone pretending to be someone the person trusts, and they’ll send links or attachments, asking them to open them. Vulnerable users fall for this trap; before they know it, all their sensitive and confidential data has been compromised. It would help if you were cautious, as malicious actors often employ social engineering tactics to steal the user’s sensitive and confidential data. Always confirm with the sender whether they sent the emails and messages, and learn to pinpoint the signs of fraudulent emails and messages.
3) Download Software From Trustworthy Sources
Downloading software from third parties and untrustworthy sources can lead to malware on your PC. When downloading software, ensure you’re doing it from a legitimate source. Downloading apps from unknown sources means installing software with viruses and malware, which will sneakily infiltrate your device once you download them. So always download apps from trustworthy sources and check the reviews and ratings of the software you’re downloading for a clearer picture of whether it’s safe.
4) Use Strong Passwords & Enable 2FA
Make sure that you implement strong passwords for all your online accounts. Choosing a strong and complex password ensures that malicious actors and cybercriminals cannot easily infiltrate your accounts and will find it challenging to gain unauthorized access. When choosing a strong password, ensure it has an uppercase letter, a lowercase letter, special characters, and numbers.
You should also enable two-factor authentication (2FA) on all your online accounts. Two-factor authentication means that additional verification is required before you can access your online accounts. This extra verification can be in the form of a one-time password (OTP) sent to your email or phone number or biometric verification.
Wrapping Up
The Wacatac trojan virus can be hard to detect, damage your devices, and compromise your sensitive data if you don’t take timely action. However, the good news is that this guide outlines some of the most effective steps to get rid of the trojan for good.
Frequently Asked Questions (FAQs)
Wacatac is a trojan that locks files and affects Windows devices. It can download and install other malware on your computer and steal your personal information, such as your Personally Identifiable Information (PII).
Yes, the Trojan virus can be removed by installing antivirus software, resetting your browser to default settings, and removing malicious apps from your PC.
There can sometimes be a false positive, where safe files are incorrectly identified as threats. However, there are ways to resolve this issue: if you think your file is safe and it’s being incorrectly identified as a threat, you can send it to Microsoft for analysis.
Once malware gets executed, it can start damaging your computer, but the amount of damage that happens depends on how the hacker has designed the trojan.




No comments were posted yet