Android is one of the most popular operating systems in the world, powering millions of smartphones and tablets. However, as with any popular technology, there are always those who seek to exploit it for their own gain.
If you suspect your Android phone has been hacked, it’s important to take action as soon as possible to protect your personal information and device. In this blog post, we’ll cover how to fix a hacked Android phone and discuss some Android operating system security flaws.
Table of Contents
Security Flaws of Android
Android is an open-source operating system, meaning anyone can access its source code and modify it. While this allows for great flexibility and innovation, it also means that the system is more susceptible to security flaws. Here are some of the common security flaws of Android:
- Malware: Malware is a type of software that is designed to harm or exploit your device. Android’s open-source nature makes it easier for attackers to create and distribute malware. This is one of the major reasons why maintaining privacy on Android is a big challenge.
- Vulnerabilities: Vulnerabilities are weaknesses in the system that attackers can exploit. Android has had several vulnerabilities over the years, including the Stagefright vulnerability in 2015.
- Outdated Software: Android updates are crucial to patching security flaws and vulnerabilities. However, many Android devices do not receive timely updates, leaving them vulnerable to attack.
- Unverified Apps: Android allows users to install apps from third-party sources, which can increase the risk of downloading malicious apps.
Android Hacking: What does it mean?
The term “Android hacking” generally refers to the act of exploiting vulnerabilities or security weaknesses in the Android operating system or applications running on Android devices in order to gain unauthorized access, steal data, or control the device for malicious purposes.
Android hacking can take many forms, such as:
- Rooting or jailbreaking the device to gain access to privileged system functions and settings.
- Exploiting vulnerabilities in Android apps to gain access to sensitive data or device functions.
- Installing malware on the device to control it remotely or steal data.
- Intercepting or manipulating data transmitted over the network, such as through a Wi-Fi or cellular connection.
- Social engineering attacks, such as phishing or spear-phishing, trick users into revealing their passwords or other sensitive information.
Android Hacking Cases in the Past
There have been several high-profile cases of Android hacking in the past. Here are a few notable examples:
- Stagefright (2015): Stagefright was a major vulnerability discovered in Android’s media playback engine, which allowed an attacker to execute code remotely on an Android device by sending a specially crafted multimedia message (MMS). This vulnerability affected millions of Android devices worldwide and was considered one of the biggest security threats to the Android ecosystem.
- HummingBad (2016): HummingBad was a malware campaign that infected millions of Android devices, primarily in China and India. The malware was distributed through fake apps and malicious ads, and once installed, it gave the attackers complete control over the infected device, enabling them to install other malware, steal personal data, and display unwanted ads.
- Judy (2017): Judy was a malware campaign that infected over 36 million Android devices worldwide. The malware was distributed through over 40 malicious apps on the Google Play Store and allowed attackers to generate fraudulent clicks on ads, generating revenue for the attackers.
- Skygofree (2018): Skygofree was a highly sophisticated spyware campaign that targeted Android devices in Italy. The malware was capable of taking screenshots, recording audio, and intercepting messages and calls, and was believed to be developed by a nation-state actor.
- Simjacker (2019): Simjacker was a vulnerability discovered in the SIM card technology used in many mobile phones, including Android devices. The vulnerability allowed attackers to remotely take control of the device by sending a specially crafted SMS to the SIM card, enabling them to track the device, steal sensitive data, and eavesdrop on calls and messages.
These are just a few examples of Android hacking cases that have been reported in the past. It is important to stay vigilant and keep your Android device updated with the latest security patches to protect against these threats.
How to Know that Your Android is Hacked
If you suspect that your Android device has been hacked, here are some signs to look out for:
1. Unusual behavior
If your device behaves erratically, such as frequent crashes or freezes, or if you notice apps opening or closing on their own, this could be a sign that your device has been compromised.
2. Strange text messages or calls
If you receive strange text messages or calls from unknown numbers, it could indicate that someone has gained access to your device.
3. Battery drains quickly
If you notice that your device’s battery is draining faster than usual, even when you’re not using it, it could be a sign that a malicious app or program is running in the background.
4. Unexplained data usage
If you notice a sudden increase in your data usage, it could signify that your device is sending or receiving data without your knowledge.
5. Pop-up ads
If you see pop-up ads on your device even when you’re not using any apps or browsing the internet, it could be a sign that your device has been hacked.
6. Antivirus alerts
If your device’s antivirus software flags certain apps or files as malicious, it could indicate that your device has been compromised.
If you suspect your Android device has been hacked, it’s important to take action immediately to protect your personal information and prevent further damage.
How to Fix your Hacked Android phone
Now you would be wondering how to remove a hacker from my phone. Well, there are many ways a hacker may access your device, which is why there are many ways to fix the hacking problem. Here’s what to do if your phone is hacked or you even suspect it:

1. Disconnect your phone from the internet
If you suspect that your phone has been hacked, disconnect it from Wi-Fi and cellular data immediately. This will prevent the attacker from accessing your device and personal information.
2. Enter Safe Mode
Entering Safe Mode will disable all third-party apps on your device, allowing you to detect any malicious apps. To enter Safe Mode, press and hold the power button, then press and hold the “Power Off” option until you see the Safe Mode option. Follow these steps to put your phone in safe mode:
- Keep holding down the power button until the screen goes black.
- Simply tap and hold Power Off when the power menu appears.
- A safe mode restart can be triggered by selecting it when prompted.
- If it doesn’t work, turning off the device might help. As soon as it restarts, press and hold the power button until you see the “Safe mode” screen appear, and then release both buttons.
3. Uninstall suspicious apps
Malware and adware (ad-supported malicious software) can be put on your phone through an uninstalled app or an outdated app that is no longer supported by the developer. If you detect any suspicious apps in Safe Mode, uninstall them immediately. If you are unable to uninstall an app, try disabling it.
Here’s how you can uninstall any suspicious apps on your phone:
- Open Settings on your phone.
- Go to the Apps menu.
- Check for any new, suspicious apps.
- Delete or Disable the app when you find it.
4. Run a malware scan
Check your device’s security by scanning it with an antivirus program. However, before downloading anything, double-check that it is not a pirated app. A reliable antimalware program will both safeguard your phone from contaminated files and remove any viruses that may already be there. If a suspicious computer tries to access your account, it will immediately shut down all connections from that machine.
5. Reset your device
If all else fails, consider resetting your device to its factory settings. This will erase all data on your device, including any malware or suspicious apps. This is the ultimate Android hack fix as it’ll clean the system from any malware or hacker that is accessing your device.
How to Prevent Your Phone From Being Hacked
Preventing future hacks is crucial to protecting your Android device and personal information. Here are some steps you can take to prevent future hacks:
- Keep your software up to date: Make sure to update your Android software as soon as updates become available. This will patch any security flaws and vulnerabilities.
- Install apps from trusted sources: Only download apps from the Google Play Store or other trusted sources. Avoid downloading apps from third-party sources.
- Use strong passwords: Use strong, unique passwords for all your accounts and change them regularly.
- Enable two-factor authentication: Enable two-factor authentication on all of your accounts. This adds an extra layer of security by requiring a second form of verification to log in.
- Use Astrill VPN: Astrill VPN encrypts your internet connection and keeps your data secure, especially when using public Wi-Fi. It’ll also make sure that your IP address and DNS are masked so that no one can trace your actual location. You can install AstrillVPN on Android by simply following these steps:
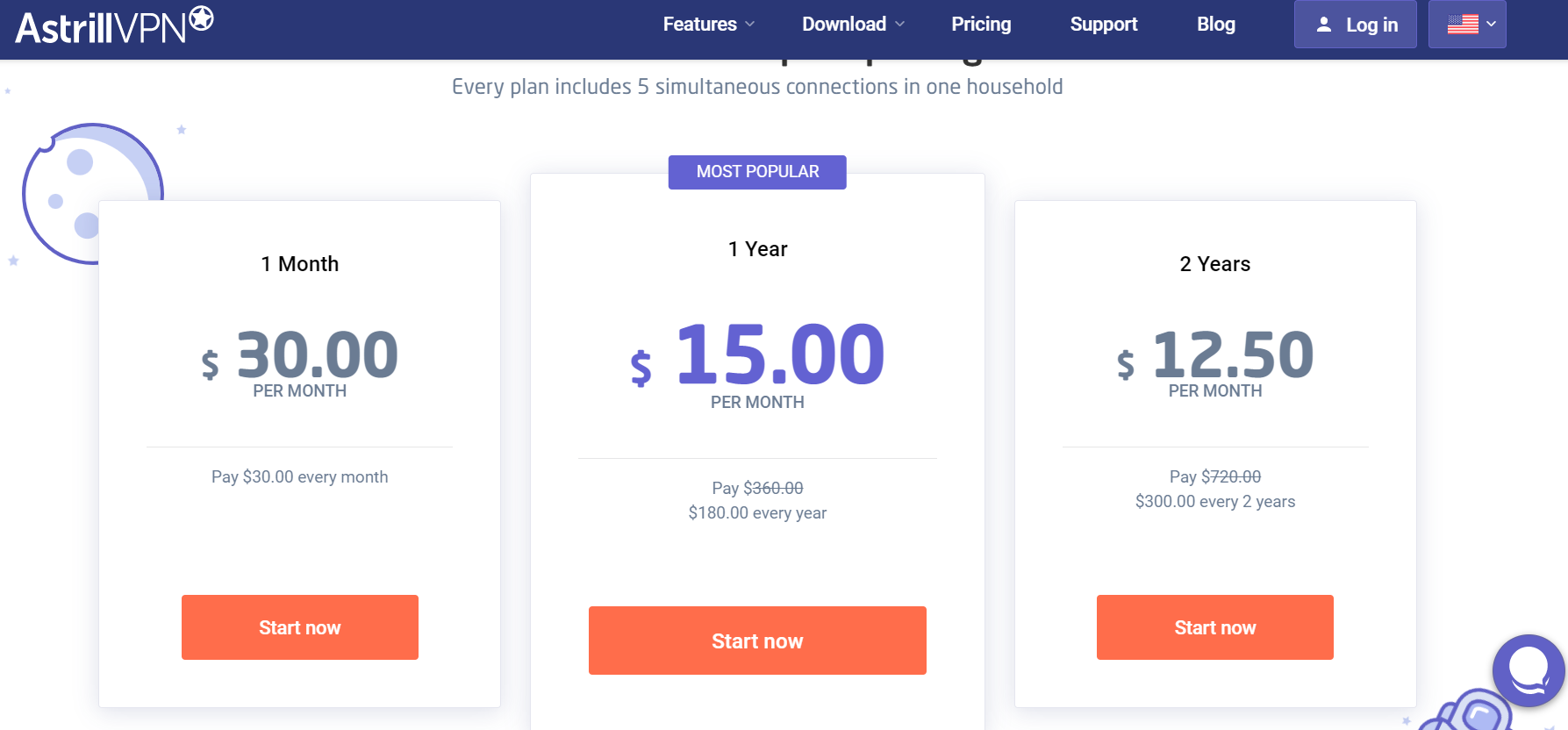
- Go to the AstrillVPN website and subscribe to it.
- Download the Android app and install it.

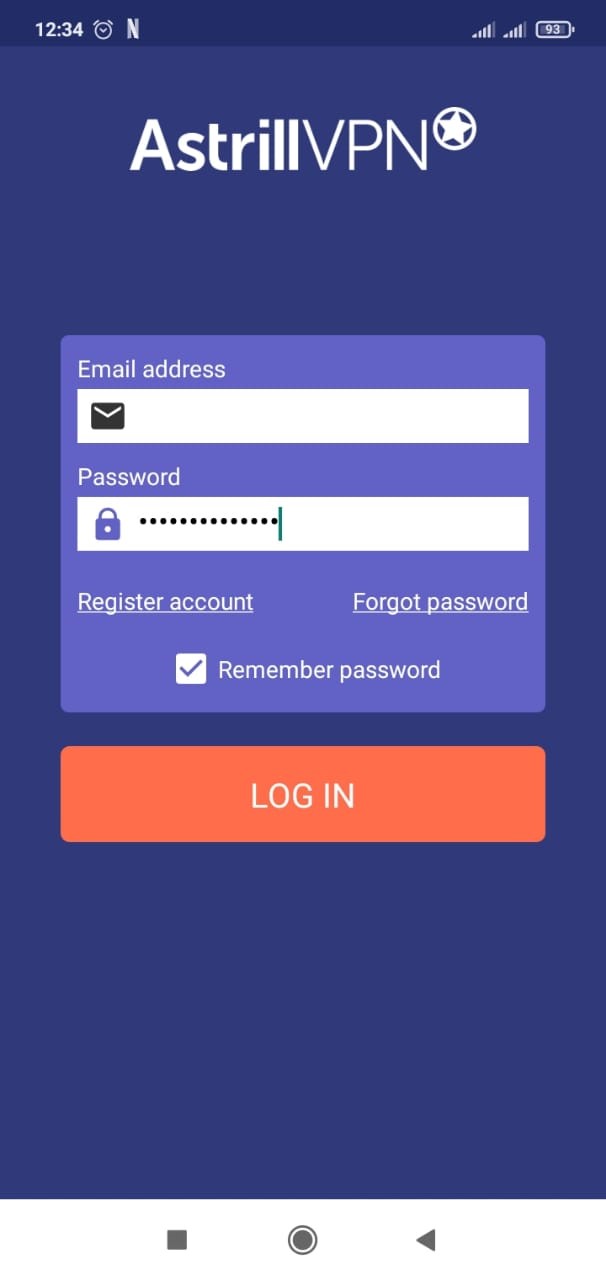
- Open the app and log in using your credentials.
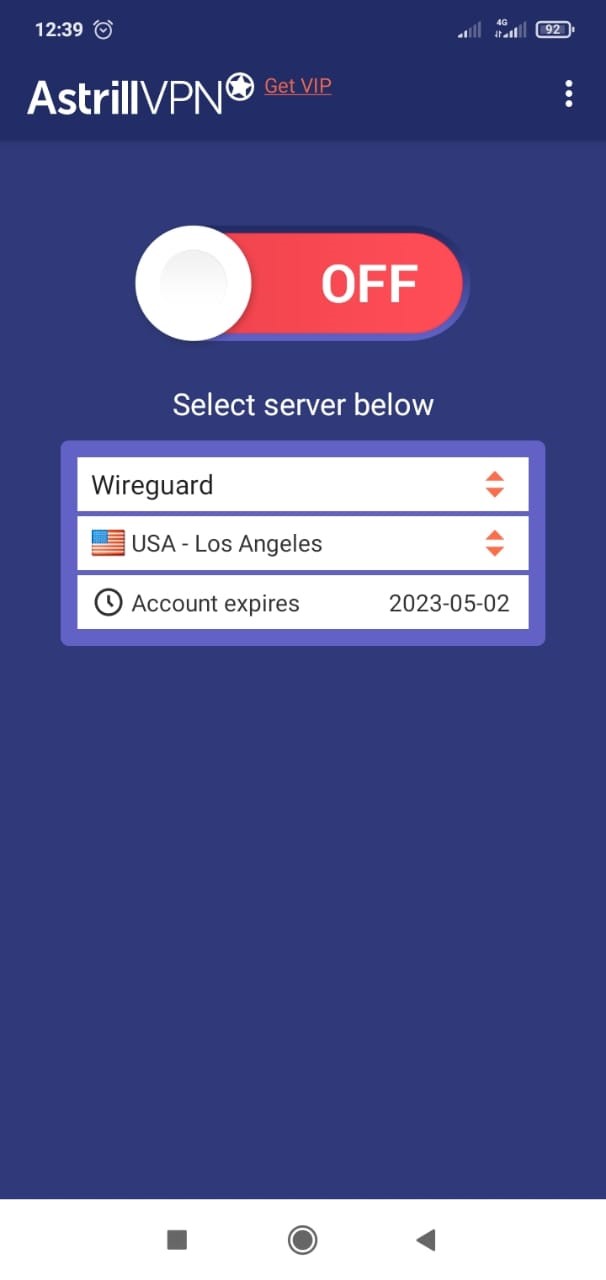
- Connect to any server of your choice to start protection.
Conclusion
If you suspect your Android phone has been hacked, it’s important to take immediate action to protect your device and personal information. Disconnect your phone from the internet, enter Safe Mode, uninstall suspicious apps, run a malware scan, and consider resetting your device.
FAQs
Will factory reset remove hackers?
Yes, a factory reset will remove hackers from your Android phone because the app providing access to hackers will be removed by resetting the device.
Can you check if your phone’s been hacked?
Yes, certain symptoms indicate that the phone has been hacked, like device heat-up, suspicious apps, ads, popups, etc.
Does turning your phone off get rid of hackers?
Yes, but that’s not a proper solution. You’ll have to check how the hacker has gained access to your device and fix the issue.



No comments were posted yet