How to fix the “macOS cannot verify that this app is free from malware” error

Arsalan Rathore
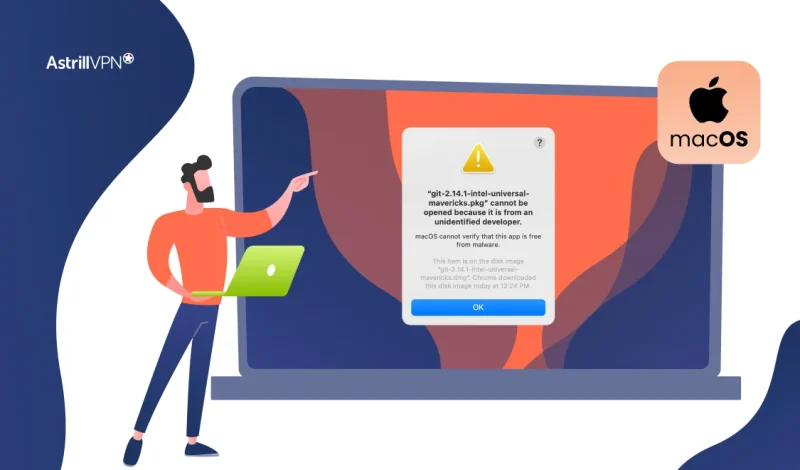
That moment when you try to open a new app and see the warning “macOS cannot verify that this app is free from malware” can be frustrating, but it’s also one of your Mac’s most important security features at work. This safeguard, powered by Apple’s Gatekeeper technology, isn’t just an arbitrary roadblock; it’s a critical checkpoint designed to protect your system from potentially harmful software.
While the warning might appear when you’re trying to install legitimate applications from trusted developers, it also serves as a vital alert against unrecognized or compromised software that could put your data and privacy at risk.
In this guide, we’ll walk you through exactly what triggers this security message, how to safely evaluate whether an app is trustworthy, and the right way to proceed
Table of Contents
Why macOS Shows macOS Cannot Verify That This App Is Free from Malware Error
Apple’s macOS is designed with multiple layers of security to protect users from malicious software. One of these critical security mechanisms is Gatekeeper, which enforces strict app validation before allowing software to run. When you encounter the warning “macOS cannot verify that this app is free from malware,” it means Gatekeeper has identified a potential security risk.
Below, we break down the technical and security reasons behind this warning.
1. Gatekeeper’s Role in macOS Security
Gatekeeper is a security feature that ensures only trusted software can be installed and executed on a Mac. It performs several key checks:
● Source Verification:
- Apps downloaded from the Mac App Store are pre-screened by Apple and considered safe.
- Apps from outside the App Store (e.g., direct downloads from developer websites) must be notarized and signed with an Apple-approved Developer ID.
● Notarization Requirements:
- Developers must submit their apps to Apple for automated malware scanning before distribution.
- If an app is modified after notarization or lacks proper certification, macOS blocks it.
● Certificate Revocation Checks:
- Even if an app was previously trusted, Apple may revoke its approval if the developer’s certificate is later associated with malware.
2. Common Triggers for This Warning
The warning appears in several scenarios, including:
● Apps from Unidentified Developers
- If an app is unsigned or lacks Apple notarization, macOS prevents it from running by default.
● Modified or Corrupted App Files
- If an app’s code has been altered (e.g., due to incomplete downloads or third-party repackaging), macOS detects a mismatch in its digital signature.
● Outdated Security Databases
- Apple’s XProtect (macOS’s built-in malware scanner) and Malware Removal Tool (MRT) rely on frequent updates. If your system hasn’t updated, it may distrust recently flagged apps.
3. Security Implications of Bypassing the Warning
While users can override Gatekeeper (via Right-Click → Open or Security Settings), doing so carries risks:
- Potential Exposure to Malware
- Malicious apps often mimic legitimate software. Bypassing Gatekeeper increases the risk of running trojanized or spyware-laden applications.
- System Integrity Compromise
- Some malware exploits elevated permissions once installed, leading to data theft, keylogging, or ransomware attacks.
How to Fix the “macOS Cannot Verify that this App is free from Malware error” Safely
Encountering macOS’s security warning doesn’t necessarily mean the app is malicious, it simply means Apple hasn’t scanned or approved it. Below are safe, step-by-step methods to resolve this issue while minimizing security risks.
Method 1: Use the “Open” Bypass (Recommended for Trusted Apps)
If you’re confident the app is safe (e.g., downloaded from the official developer’s site), follow these steps:
- Locate the app in Finder (usually in Applications or your Downloads folder).
- Right-click (or Control + Click) the app and select “Open” from the context menu.
- A second warning will appear. Click “Open” again to confirm.
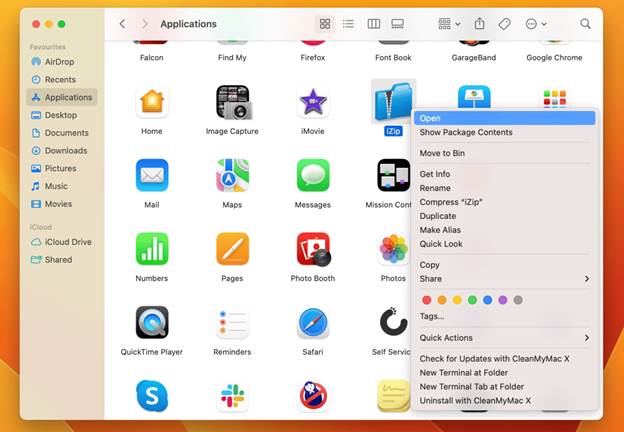
This method temporarily exempts the app from the strict enforcement of the gatekeeper while keeping macOS’s security intact. Unlike disabling Gatekeeper entirely, it doesn’t lower your Mac’s overall protection.
Method 2: Adjust Security & Privacy Settings
If the app repeatedly triggers warnings, you can temporarily allow it in System Settings:
- Go to Apple Menu → System Settings → Privacy & Security.
- Under “Security,” look for the message:
“[App Name] was blocked because it is not from an identified developer.”
- Click “Open Anyway” to approve the app.
Method 3: Verify & Re-download the App (For Suspicious Errors)
If macOS still blocks the app, it may be corrupted or tampered with. Here’s how to ensure a clean installation:
- Delete the current app (drag to Trash and empty it).
- Re-download the app from the official source (e.g., if you want to instal AstrillVPN then download the app from AstrillVPN’s download page).
- Check the developer’s website for any security notices.
Method 4: Use Terminal to Bypass (Advanced Users Only)
For developers or IT admins, manually approving an app via Terminal is an option:
- Open Terminal (Finder → Applications → Utilities).
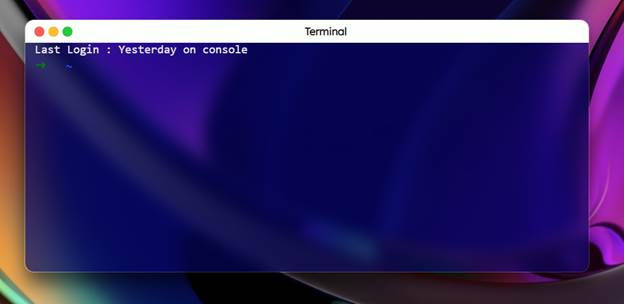
- Enter:
sudo xattr -rd com.apple.quarantine /Applications/AppName.app
(Replace AppName.app with the actual app name.)
- Enter your admin password when prompted.
How to Check If an App Is Legitimate
Before bypassing macOS security warnings, you need to verify an app’s authenticity. Here’s how to conduct thorough checks while maintaining security:
1. Check Where You Downloaded It
- Only download apps from the official developer’s website or the Mac App Store
- Be suspicious if you got it from a forum, torrent, or third-party download site
- Look for HTTPS in the website URL (the padlock icon)
2. Verify the Developer
- Right-click the app and select “Get Info”
- Look for the developer name under “General”
- Google that name to make sure it’s legitimate
3. Look for These Warning Signs
- The app asks for way more permissions than it needs
- You see spelling mistakes or bad graphics in the app
- It tries to install extra software you didn’t ask for
- Your Mac starts running slower after installing it
4. Extra Checks for Important Apps
For banking, work, or security apps:
- Check reviews on multiple websites
- Search “[app name] scam” or “[app name] malware”
- See if tech news sites have written about it
Signs of Potential Malware
Even if an app bypasses Gatekeeper, watch for these red flags:
1. Unusual Behavior After Installation
- Unexpected Processes: Check Activity Monitor for suspicious CPU/memory usage.
- Network Anomalies: Use Little Snitch or Lulu to monitor outgoing connections.
- Browser Hijacking: New toolbars, search engine changes, or pop-up ads.
2. Poor Design or Typos
- Malware often has:
- Generic icons (e.g., a default .app bundle icon).
- Spelling errors in menus or prompts.
- Fake “System Alert” dialogs urging immediate action.
3. Requests for Excessive Permissions
- A legitimate VPN like AstrillVPN only needs:
- Network access (to encrypt traffic).
- Admin rights (for installation only).
- Malware may demand:
- Full Disk Access (to steal files).
- Keylogging permissions (under Input Monitoring).
4. Missing Developer Transparency
- No public LinkedIn/GitHub profiles for the developer.
- Domain registered recently (check via Whois).
- No contact info beyond a generic support form.
5. Persistence Mechanisms
- Malware often hides in:
- LaunchAgents (~/Library/LaunchAgents/)
- Login Items (System Settings → General → Login Items)
- Kernel Extensions (rare, but check via kextstat in Terminal).
FAQs
Proceed only if you trust the source. Override warnings for apps downloaded from official developer websites or the Mac App Store. Avoid bypassing for pirated software, email attachments, or apps requesting excessive permissions. Always scan unknown files with antivirus software first.
Common causes include expired developer certificates, delayed notarization, post-signing app modifications, or outdated macOS security databases. Even reputable apps may trigger warnings temporarily after updates or system changes.
Right-click the app and select “Open” to create a Gatekeeper exception. Advanced users can whitelist via Terminal (spctl –add). Note that Apple may revoke trust if the developer’s certificate is later flagged. For businesses, MDM solutions can manage app approvals centrally.

No comments were posted yet