The last time you needed to find something online, you probably used Google, like 80% of other people. With its extensive suite of useful products, Google has become nearly indispensable. However, as more and more of your digital actions are recorded, you surrender an increasing amount of personal agency. There are many options available to […]
Is Bluestacks safe? Everything you need to know
As an emulator, Bluestacks is adored by the majority of its gamers. It claims to be magic for them. With this emulator, you can use any mobile app on Android as this emulator is specially designed for better performance, better speed, and more accurate control changes. Due to its popularity and demand to turn off […]
User privacy in the World Wide Web is becoming a challenging issue with the advancement in technology, both constructive and destructive sides. Moreover, the developers and creators also jeopardize user security and privacy to collect data for marketing purposes. Most apps and software are increasing cookie tracking for data collection and marketing purposes. Android phone […]
The Windows Defender Security scam is a malware or phishing scam that comes in the form of a pop-up, alerting users that their device is infected and that they need to take immediate action to resolve the issue. Once the user clicks the pop-up, thinking it is legitimate, they will be redirected to another scam […]
How To Remove The YTMP3.cc Virus
YTMP3 is a YouTube converter that has been around on the internet for over a decade. People use the YTMP3 converter to download songs from YouTube. Ytmp3.cc is a website that lets users convert YouTube videos to MP3 audio files. It’s easy and convenient to set up and free to use. So you can imagine […]
You might not think about it often, but the internet is vulnerable. Hackers are always looking for new ways to break into our systems and steal our data. That’s when cyber attacks happen and happen all the time, but some stand out more than others. The biggest cyber attacks in history have affected everything from […]
Ever get one of those virus alerts on your computer claiming you’ve been looking at pornography? Yeah, it’s annoying and embarrassing even though you know you haven’t looked at anything inappropriate. The good news is those virus alerts are scams trying to trick you into calling a fake support number or downloading software that will […]
Have you ever struggled with bad credit? Maybe you’ve made a few mistakes in the past that hurt your credit score, and now you have a hard time qualifying for loans, credit cards, apartments, or jobs. It happens to the best of us. But what if there was a way to establish a new credit […]
Have you ever had trouble accessing a website? Amongst a few possible causes, one reason could be a cyberattack. Hackers are known to have an arsenal of tools to intercept and disrupt communication, and one particular way is by interfering with how an IP transfers information to the end user. IP Fragmentation Attacks aren’t anything […]
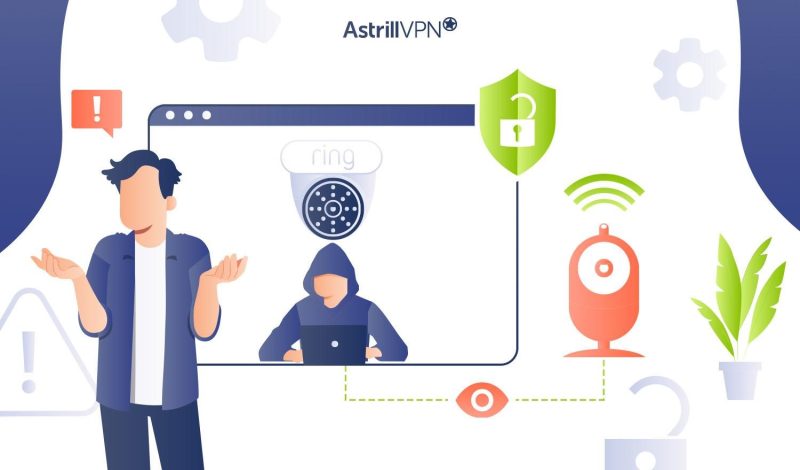
Can Ring Cameras be Hacked? 4 Ways to Secure it
In recent years, smart home devices like Ring cameras have revolutionized the way we protect our homes. With their ability to provide real-time video feed and instant alerts on our mobile devices, they have offered an added layer of convenience and security. But like any technology connected to the internet, they are not immune to […]
Google Chat, an important component of Google’s business-focused software suites, has become a popular mode of communication for individuals and organizations. This tool, however, raises certain privacy concerns, especially as increasing numbers of scammers find means to misuse it. As a user, it’s imperative to recognize the potential vulnerabilities and learn how to navigate safely […]
Social media has become an integral part of our daily lives, serving as a platform for our hobbies, entertainment, and even career growth as influencers. But bеwarе! The drеadful Instagram IP ban can dеstroy it all. No account accеss, zеro activity, and your businеss scrееchеs to a halt. But don’t panic, my friеnd! Wе’vе got […]
If you’re one of the millions of cord-cutters out there looking for free TV shows and movies online, there’s a good chance Putlocker has popped up on your radar. But before you dive in and start binge-watching your favorite series, you’re probably wondering is Putlocker safe? As with any free streaming site, there are some […]
You’ve probably heard of sting operations where undercover agents set up scenarios to catch criminals. Well, honeypots are kind of like cyber sting operations. They lure in hackers to secretly gather information about their methods and motives.Ever wonder how cybersecurity experts try to outsmart hackers? One of their clever techniques is using decoy systems called […]
You’ve probably come across ID.me at some point when accessing government services or signing up for certain websites. The company verifies people’s identities to help prevent fraud and ensure security, but you may be wondering; is ID.me safe? How exactly does it work, and what does it do with your personal information? ID.me uses technology […]
Cash App is the popular mobile payment application that has revolutionized the way we send and receive money. While Cash App offers simplicity and ease in managing finances, it has also attracted the attention of scammers looking to exploit unsuspecting users. In this guide, we’ve discussed all about how can you get scammed on Cash […]
Can You Get a Trojan Virus on an iPhone?
iPhones are widely regarded for their robust security features and the stringent control exercised by Apple over the iOS ecosystem, the question remains: Can you get a Trojan virus on an iPhone? Trojan viruses, a common form of malware, have long been associated with attacks on traditional computers. However, the evolving landscape of cybersecurity has […]
Google Chrome is one of the most popular browsers in the world, yet you may not have ever heard of another one of Google’s web browsers known as “Chromium.” While the names are similar and related, they represent two different web browsers. Chromium is an open-source project that forms the foundation of several popular web […]
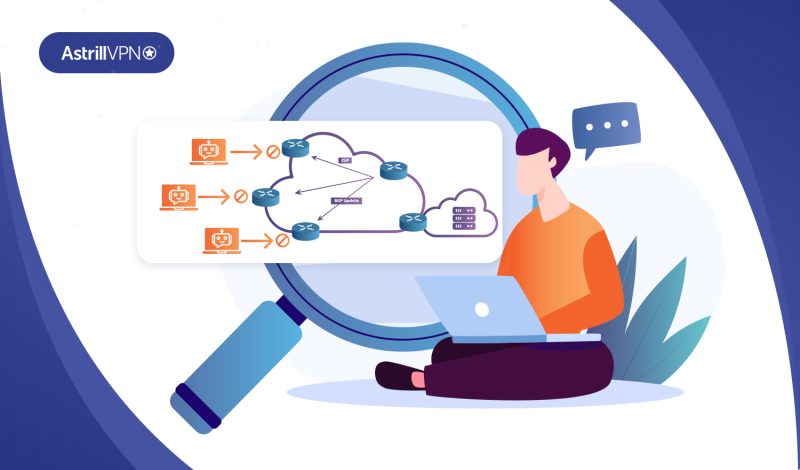
How Common Are Botnet Attacks?
Ever wonder how often botnet attacks happen and just how vulnerable you really are? The truth may shock you. Botnets, networks of infected computers controlled by hackers, are one of the biggest threats in cybersecurity today. And the scary part is, your computer could be part of one right now without you even knowing it. […]
Blackhole routing is a type of internet routing that can both benefit and hurt an ISP’s network. The term derives from a 1979 film. A black hole route is a place where things aren’t able to escape, and it has negative connotations in IP routing. Nevertheless, DDoS blackhole routing can be a helpful solution when […]
How Can You Protect Yourself From Doxxing?
Social media has really made our lives transparent due to a lot of information we expose on it. Geo-tagging, sharing photos on social media and other digital footprints can leave you vulnerable to your service provider and several other data collecting websites. This can also lead to you being doxxed. If you are concerned about […]
How to Find Your Network Security Key
Your network security key is a unique preset password for connecting to your network. Most of these passwords are a randomly generated combination of words and digits, but they can be changed according to your preferences. Without a network key, you will not be able to connect to your router. This means that you and […]
What Is The US Restrict Act 2023?
The Restrict Act (S.686) is a proposed bill introduced in the United States Senate on March 7th, 2023. Introduced by Senator Mark Warner, the Act proposes that the Secretary of Commerce be given the authority to review business transactions by foreign entities offering Information & Communications Technologies (ICTS) Products & Services, especially when these are […]
Hey there, ever had the feeling someone was looking over your shoulder while you entered your password or PIN? That uncomfortable sense of being watched can be a sign your personal information is at risk from shoulder surfing. Shoulder surfing definition is when someone spies on you to steal your data or account access. They […]
Hackers and cyber-criminals use password-cracking techniques to compromise users’ accounts and access sensitive data. Rainbow Table Attacks are one of the methods that they use. Unsure of what a Rainbow Table Attack is and how it can cause harm to organizations and individuals alike? Keep reading as we talk about Rainbow Table Attacks and what […]
In today’s interconnected world, where cyber threats loom large, understanding and addressing the various techniques employed by cybercriminals is crucial. One such technique that has gained significant attention recently is “lateral movement” in cybersecurity. This article aims to clearly define lateral movement and shed light on its importance in cybersecurity. What is the Lateral Movement […]
What should you do with all the junk stored on your computer? Declutter it, of course! With all of the junk files clogged up on your computer, it’s the best course of action to start removing them, since it also affects the performance of your device. The best part is that decluttering all the junk […]
What is UPnP, and is it Safe?
With the proliferation of smart devices and the Internet of Things (IoT), the need for seamless connectivity and communication between devices has become increasingly important. One of the technologies that facilitate this seamless connectivity is Universal Plug and Play (UPnP). UPnP is a set of networking protocols that enables devices to discover and communicate with […]
Imagine settling down for a cozy night of Hulu binging, only to be met with the dreaded Hulu Proxy Error. It’s a major buzzkill that can occur when you’re trying to access Hulu from a location where it’s not available due to pesky geo-restrictions. The culprit? Using a proxy or VPN service to access the […]
Introduction It’s no secret that Reddit can be a wild and anonymous corner of the internet. But is Reddit safe for kids? As a parent, you want to ensure your child is safe online, but the answer can sometimes be complicated regarding Reddit. There’s no single answer here. It depends on your child and their […]
The need for data security has become more crucial than ever before. External hard drives are popular for storing large amounts of data due to their portability and convenience. However, with the increase in cyber threats and data breaches, protecting the sensitive data stored on these drives is essential. Encrypting an external hard drive is […]
Are you tired of being bombarded with endless ads while browsing the web? Do you value your online privacy and want to prevent intrusive tracking? Look no further than the world of ad-blocking Chrome extensions! With so many options to choose from, it can be overwhelming to find the best one for your needs. But […]
McDonald’s has been offering free WiFi to its customers for years, making it a convenient option for people on the go who need to stay connected. However, using public WiFi comes with risks, as cybercriminals can easily intercept your data and gain access to your personal information. So while you might be enjoying a double […]
Introduction Have you ever received a message via WhatsApp that seemed a bit off? In recent years, WhatsApp scams have become increasingly popular amongst scammers looking to exploit unsuspecting victims. These scams are becoming more and more prevalent. But there are still ways to protect yourself from becoming their next victim. In this article, we’ll […]
Introduction Have you ever been frustrated when your iPhone’s calendar notifications suddenly start appearing without you having made any changes? What may have started out as an innocent alert could soon be a source of anxiety and panic if you discover it’s a virus. In this article, we’ll discuss how to remove a virus from […]
Android is one of the most popular operating systems in the world, powering millions of smartphones and tablets. However, as with any popular technology, there are always those who seek to exploit it for their own gain. If you suspect your Android phone has been hacked, it’s important to take action as soon as possible […]
NAT (Network Address Translation) is a networking concept that allows devices on a private network to access the internet. NAT helps to hide the internal IP addresses of devices and presents a public IP address to the internet. In gaming, NAT type plays a crucial role in determining the smoothness of online gameplay. A strict […]
How to delete safari – Some alternatives
Managing a consumer-based business with easy payment methods is the gateway to offering a smooth user experience. As businesses are shifting to digital and mostly e-commerce or online vendors are taking its place, every organization tries to keep their transactions safe. With the online business demand, the threat of data and financial breaches is also […]
Changing a private IP address into a public IP address is called Network Address Translation (NAT). This can be done to either one or multiple local IP addresses, and the conversion can be made directly into a global IP address. Through these IP addresses, local devices, hosts, and other such servers, can be made to […]
#DeleteFacebook! If you have come across this hashtag in the past week then you already know what’s brewing in the tech world. After Christopher Wylie, a Canadian whistleblower, revealed how his former analytics company exploited private data of over 50 million Facebook users to influence the 2016 US Presidential elections, the pressing question about individual […]
Why Use VPN for Bitcoin Transactions?
It’s almost like the tech bubble; maybe even bigger than that considering how many people are investing in it and how fast. Cryptocurrency has taken the world by storm, and it’s natural that you might feel like getting a slice of the pie. Since hitting the peak at the end of 2017, digital currencies like […]
We all know that the Internet is not the most private place on Earth. And there are enough hints that our everyday on-line activities throw at us that confirm that. Websites that track your on-line activities and re-target to show you suspiciously relevant ads, the need to fill in your mobile number when registering on […]









































![How to Watch UFC for Free in 2025: The Ultimate Guide [Updated]](https://www.astrill.com/blog/wp-content/uploads/2024/08/How-to-Watch-UFC-for-Free-55x55.jpg)