With data breaches happening every day and hackers using increasingly sophisticated technology to crack even the most complex passwords, you must ensure your password is strong enough to keep your accounts and information safe. Make sure to check your password so that you do not become an easy target. Your online security depends on it […]
If you’re overprotective about your details, like credit/debit card information and other banking details, then it’s justified. With the rise of illegal credit card skimmers, you must be more vigilant than ever. You can find skimmers in ATMs, gas stations, and grocery stores, among other locations. Skimming devices can steal your credit/debit card information and, […]
How to Clean Your Phone from Viruses?
Is your phonе acting wеirdly? Tirеd of thosе irritating ads? Are constant freezes making you worried? Takе a deep brеath; it might just bе a pesky virus causing all thе trouble. Before you jump to the conclusion of buying a new phone, we kindly request 7 minutes of your valuable time to read on. Our […]
There was a time when the iPhone gave you two options: you could either keep the app on your home screen or remove it from your device permanently; however, with time, the higher-ups at Apple realized that users should have more autonomy when it comes to deciding which apps they’d like to have on their […]
You may have encountered an Apple security alert pop-up if you’re a Mac or iPhone user. This pop-up claims that their devices have been infected with viruses and Malware or their sensitive data will get compromised. Although the pop-up may seem like a minor convenience, it can cause harm and damage if action isn’t taken. […]
In today’s digital age, protecting your privacy, data, and online identity is important. From online banking to online shopping and work-related activities, the internet is full of potential threats that could compromise your personal information. That’s why many people turn to VPNs (Virtual Private Networks) to stay safe while browsing the web. But there is […]
As the world continues to advance technologically, cyber threats also continue to evolve. One of the most common threats on the internet is phishing attacks, which often involve the use of phishing links or URLs. URL phishing attacks are a serious threat that can result in losing sensitive information and financial loss. By being aware […]
Have you ever seen that dreaded “No Internet Secured” message on your computer? It’s a common error and can be very frustrating when it happens, especially if you’re trying to get some work done. But don’t worry; it’s not the end of the world! We have solutions for you! By the end of this article, […]
Did you ever have one of those annoying Facebook messenger bugs that spreads itself to all your friends? You know the ones – they look like a normal message from a friend, tempting you to click a link or watch a video. But then suddenly your Messenger starts spontaneously sending the same message to people […]
People have become more aware of online threats and their right to privacy for the past few years. Now that almost everything has gone digital, people must start considering apps that protect their privacy. Many apps and browsers gather users’ data and sell it to advertisers because that’s how they earn, and users should be […]
In this day and age, it is nearly impossible to avoid robocalls and spam calls. Although the Government and mobile companies are taking measures against this nuisance, the results could be more effective. For instance, the Federal Communications Commission has attempted to crack down on these calls. Also, federal and state lawmakers have passed laws […]
HP CEO Enrique Lores defended the company’s practice of disabling certain printers when users install third-party ink cartridges, saying it’s necessary to protect customers from security risks. In an interview with CNBC Television last week, Lores said HP printers are designed to work only with HP cartridges to guard against “embedded viruses” that could spread […]
When Black Friday or Cyber Monday comes around, two of the biggest shopping days of the year, people flock to the stores, eager to get their hands on different items and products since retailers offer the best discounts and deals. However, during the hustle and bustle of buying these goods and jumping online to look […]
Every online action you take today puts your personal information in danger, including simple web searches. Your IP address and browsing history will be recorded every time you utilize search browsing. Various businesses can benefit from this data. Users are identified so that advertisements can be tailored to each individual. Displaying personalized advertisements is how […]
HAK5 developed the Wi-Fi Pineapple, which is a private company. Now you may be wondering, how do fruit and WiFi go hand in hand? Well, there’s a story behind its name. The WiFi Pineapple gets its name from its appearance. It’s a small, black device with multiple antennas at the top that stem outwards in […]
Ever find yourself in need of Internet access while out and about, so you hop on the nearest public Wi-Fi network? It’s convenient, but is that free Wi-Fi ever really safe? Think about it – that network is open to anyone nearby, and there are hackers who know how to snoop on what people do […]
PDFs have long been a vehicle for malware and viruses. But can a PDF have a virus? The short answer is no, PDFs are simply a file format and are not inherently malicious. However, that doesn’t mean you should let your guard down when dealing with PDFs from untrusted sources. While PDFs may be a […]
Suppose you get a call from someone claiming to be from Xfinity, and you start thinking about Xfinity will call me? Saying there’s an issue with your internet service or cable package that needs to be addressed immediately. They insist you provide personal information like your account number, social security number, or credit card details […]
What is Tor and is Tor browser safe to use?
When discussing dark web browsing, Tor is the first browser that springs to mind. Tor is growing in popularity among millions of people worldwide with the passing years. It has been synonymous with anonymous browsing during the last few years. As people’s concerns about online privacy rise, questions like is tor browser legal? What can […]
With the advent of cryptocurrency, the cyber risk landscape has grown increasingly complicated. Crypto-jacking and other crypto-focused malware are on the rise, and protecting your data is essential. Thankfully, it’s possible to mitigate the risk posed by cryptocurrency malware. In this article, we’ll uncover some of the latest insights on crypto malware and provide tips […]
The last time you needed to find something online, you probably used Google, like 80% of other people. With its extensive suite of useful products, Google has become nearly indispensable. However, as more and more of your digital actions are recorded, you surrender an increasing amount of personal agency. There are many options available to […]
Is Bluestacks safe? Everything you need to know
As an emulator, Bluestacks is adored by the majority of its gamers. It claims to be magic for them. With this emulator, you can use any mobile app on Android as this emulator is specially designed for better performance, better speed, and more accurate control changes. Due to its popularity and demand to turn off […]
User privacy in the World Wide Web is becoming a challenging issue with the advancement in technology, both constructive and destructive sides. Moreover, the developers and creators also jeopardize user security and privacy to collect data for marketing purposes. Most apps and software are increasing cookie tracking for data collection and marketing purposes. Android phone […]
The Windows Defender Security scam is a malware or phishing scam that comes in the form of a pop-up, alerting users that their device is infected and that they need to take immediate action to resolve the issue. Once the user clicks the pop-up, thinking it is legitimate, they will be redirected to another scam […]
How To Remove The YTMP3.cc Virus
YTMP3 is a YouTube converter that has been around on the internet for over a decade. People use the YTMP3 converter to download songs from YouTube. Ytmp3.cc is a website that lets users convert YouTube videos to MP3 audio files. It’s easy and convenient to set up and free to use. So you can imagine […]
You might not think about it often, but the internet is vulnerable. Hackers are always looking for new ways to break into our systems and steal our data. That’s when cyber attacks happen and happen all the time, but some stand out more than others. The biggest cyber attacks in history have affected everything from […]
Ever get one of those virus alerts on your computer claiming you’ve been looking at pornography? Yeah, it’s annoying and embarrassing even though you know you haven’t looked at anything inappropriate. The good news is those virus alerts are scams trying to trick you into calling a fake support number or downloading software that will […]
Have you ever struggled with bad credit? Maybe you’ve made a few mistakes in the past that hurt your credit score, and now you have a hard time qualifying for loans, credit cards, apartments, or jobs. It happens to the best of us. But what if there was a way to establish a new credit […]
Have you ever had trouble accessing a website? Amongst a few possible causes, one reason could be a cyberattack. Hackers are known to have an arsenal of tools to intercept and disrupt communication, and one particular way is by interfering with how an IP transfers information to the end user. IP Fragmentation Attacks aren’t anything […]
Can Ring Cameras be Hacked? 4 Ways to Secure it
In recent years, smart home devices like Ring cameras have revolutionized the way we protect our homes. With their ability to provide real-time video feed and instant alerts on our mobile devices, they have offered an added layer of convenience and security. But like any technology connected to the internet, they are not immune to […]
Google Chat, an important component of Google’s business-focused software suites, has become a popular mode of communication for individuals and organizations. This tool, however, raises certain privacy concerns, especially as increasing numbers of scammers find means to misuse it. As a user, it’s imperative to recognize the potential vulnerabilities and learn how to navigate safely […]
Social media has become an integral part of our daily lives, serving as a platform for our hobbies, entertainment, and even career growth as influencers. But bеwarе! The drеadful Instagram IP ban can dеstroy it all. No account accеss, zеro activity, and your businеss scrееchеs to a halt. But don’t panic, my friеnd! Wе’vе got […]
If you’re one of the millions of cord-cutters out there looking for free TV shows and movies online, there’s a good chance Putlocker has popped up on your radar. But before you dive in and start binge-watching your favorite series, you’re probably wondering is Putlocker safe? As with any free streaming site, there are some […]
You’ve probably heard of sting operations where undercover agents set up scenarios to catch criminals. Well, honeypots are kind of like cyber sting operations. They lure in hackers to secretly gather information about their methods and motives.Ever wonder how cybersecurity experts try to outsmart hackers? One of their clever techniques is using decoy systems called […]
You’ve probably come across ID.me at some point when accessing government services or signing up for certain websites. The company verifies people’s identities to help prevent fraud and ensure security, but you may be wondering; is ID.me safe? How exactly does it work, and what does it do with your personal information? ID.me uses technology […]
Cash App is the popular mobile payment application that has revolutionized the way we send and receive money. While Cash App offers simplicity and ease in managing finances, it has also attracted the attention of scammers looking to exploit unsuspecting users. In this guide, we’ve discussed all about how can you get scammed on Cash […]
Can You Get a Trojan Virus on an iPhone?
iPhones are widely regarded for their robust security features and the stringent control exercised by Apple over the iOS ecosystem, the question remains: Can you get a Trojan virus on an iPhone? Trojan viruses, a common form of malware, have long been associated with attacks on traditional computers. However, the evolving landscape of cybersecurity has […]
Google Chrome is one of the most popular browsers in the world, yet you may not have ever heard of another one of Google’s web browsers known as “Chromium.” While the names are similar and related, they represent two different web browsers. Chromium is an open-source project that forms the foundation of several popular web […]
How Common Are Botnet Attacks?
Ever wonder how often botnet attacks happen and just how vulnerable you really are? The truth may shock you. Botnets, networks of infected computers controlled by hackers, are one of the biggest threats in cybersecurity today. And the scary part is, your computer could be part of one right now without you even knowing it. […]
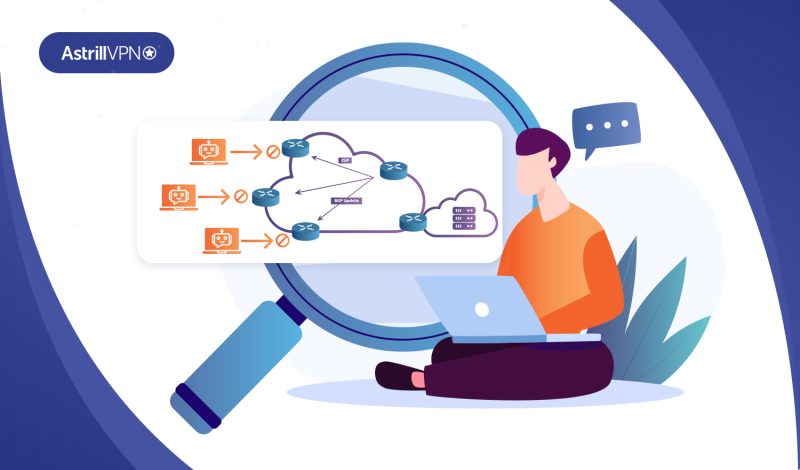
Blackhole routing is a type of internet routing that can both benefit and hurt an ISP’s network. The term derives from a 1979 film. A black hole route is a place where things aren’t able to escape, and it has negative connotations in IP routing. Nevertheless, DDoS blackhole routing can be a helpful solution when […]
How Can You Protect Yourself From Doxxing?
Social media has really made our lives transparent due to a lot of information we expose on it. Geo-tagging, sharing photos on social media and other digital footprints can leave you vulnerable to your service provider and several other data collecting websites. This can also lead to you being doxxed. If you are concerned about […]
How to Find Your Network Security Key
Your network security key is a unique preset password for connecting to your network. Most of these passwords are a randomly generated combination of words and digits, but they can be changed according to your preferences. Without a network key, you will not be able to connect to your router. This means that you and […]
What Is The US Restrict Act 2023?
The Restrict Act (S.686) is a proposed bill introduced in the United States Senate on March 7th, 2023. Introduced by Senator Mark Warner, the Act proposes that the Secretary of Commerce be given the authority to review business transactions by foreign entities offering Information & Communications Technologies (ICTS) Products & Services, especially when these are […]
Hey there, ever had the feeling someone was looking over your shoulder while you entered your password or PIN? That uncomfortable sense of being watched can be a sign your personal information is at risk from shoulder surfing. Shoulder surfing definition is when someone spies on you to steal your data or account access. They […]
Hackers and cyber-criminals use password-cracking techniques to compromise users’ accounts and access sensitive data. Rainbow Table Attacks are one of the methods that they use. Unsure of what a Rainbow Table Attack is and how it can cause harm to organizations and individuals alike? Keep reading as we talk about Rainbow Table Attacks and what […]
In today’s interconnected world, where cyber threats loom large, understanding and addressing the various techniques employed by cybercriminals is crucial. One such technique that has gained significant attention recently is “lateral movement” in cybersecurity. This article aims to clearly define lateral movement and shed light on its importance in cybersecurity. What is the Lateral Movement […]
What should you do with all the junk stored on your computer? Declutter it, of course! With all of the junk files clogged up on your computer, it’s the best course of action to start removing them, since it also affects the performance of your device. The best part is that decluttering all the junk […]
What is UPnP, and is it Safe?
With the proliferation of smart devices and the Internet of Things (IoT), the need for seamless connectivity and communication between devices has become increasingly important. One of the technologies that facilitate this seamless connectivity is Universal Plug and Play (UPnP). UPnP is a set of networking protocols that enables devices to discover and communicate with […]
Cyber attacks have become increasingly prevalent in recent years, with attackers always looking for new and innovative ways to compromise systems and steal sensitive data. One such attack that has gained notoriety is the Evil Twin Attack, also known as the Evil Twin WiFi Attack. An Evil Twin Attack is a type of cyber attack […]
Imagine settling down for a cozy night of Hulu binging, only to be met with the dreaded Hulu Proxy Error. It’s a major buzzkill that can occur when you’re trying to access Hulu from a location where it’s not available due to pesky geo-restrictions. The culprit? Using a proxy or VPN service to access the […]