Cyber threats are no longer a future concern, they are the present reality. As we enter 2025, digital security is under siege like never before. With cyberattacks increasing in scale, complexity, and impact, organizations across every sector are forced to rethink their cybersecurity strategies. This blog explores the evolving threat landscape, significant trends, high-profile incidents, […]
Imagine logging into your email or bank account, only to find that someone else has been accessing it without your knowledge. You might think your password was guessed, but it could result from a credential stuffing attack. Credential stuffing isn’t just another buzzword in cybersecurity, it’s a growing threat that exploits human behavior, specifically our […]
In today’s digital age, you’re likely familiar with various cybersecurity threats. However, one increasingly prevalent danger may have escaped your notice: smishing. This malicious tactic combines “SMS” and “phishing“. Smartphones have made banking, shopping, and two-factor codes as easy as glancing at a text and exactly why cyber-crooks love smishing. In 2025, SMS-based phishing accounts […]
Cyber threats are evolving, and one of the most alarming trends in recent years is the rise of Business Email Compromise. This is not your typical phishing scheme. It is a targeted attack that preys on trust, authority, and routine organizational communication. The financial and reputational damage caused by these scams is growing rapidly. From […]
In today’s cybersecurity landscape, ransomware attacks have evolved into a lucrative and destructive industry, and LockBit is at the forefront of this digital menace. Since its emergence in 2019, LockBit has rapidly become one of the most active and dangerous ransomware families, responsible for a significant share of global cyberattacks between 2021 and 2025. With […]
NanoCore RAT is a powerful and widely used Remote Access Trojan that allows attackers to control a victim’s system completely. First discovered in 2013, it has gained popularity among cybercriminals due to its low cost, ease of use, and range of malicious capabilities. From stealing login credentials to activating webcams and recording keystrokes, NanoCore poses […]
Is your phonе acting wеirdly? Tirеd of thosе irritating ads? Are constant freezes making you worried? Takе a deep brеath; it might just bе a pesky virus causing all thе trouble. Before you jump to the conclusion of buying a new phone, we kindly request 7 minutes of your valuable time to read on. Our […]
Distributed Denial of Service (DDoS) attacks have evolved into one of the most formidable threats in the cybersecurity landscape. With escalating attack volumes, sophisticated techniques, and significant financial repercussions, understanding DDoS protection is imperative for organizations of all sizes. This guide delves into the nuances of DDoS protection, offering insights into prevention strategies, mitigation techniques, […]
In today’s interconnected world, where cyber threats loom large, understanding and addressing the various techniques employed by cybercriminals is crucial. One such technique that has gained significant attention recently is “lateral movement” in cybersecurity. This article aims to clearly define lateral movement and shed light on its importance in cybersecurity. Nearly 90% of organizations reported […]
What is Identity Theft, and How to Prevent It?
Identity theft, a pervasive and disruptive cybercrime, poses a significant threat to individuals, businesses, and institutions. Cybercrime and identity theft trends are growing because technology is advancing rapidly, but people aren’t taking steps to protect what matters. Every individual must understand Identity theft, its dangers, and how everyone can prevent it. In this guide, we […]
In today’s digital age, you’re constantly sharing sensitive information online. Your data is vulnerable to prying eyes, from credit card numbers to private messages. This is where encryption comes in. Encryption is the process of encoding information, making it unreadable to unauthorized parties. Understanding encryption becomes crucial for protecting your privacy and security as you […]
In April 2024, cybersecurity researchers began tracking an unusually evasive malware strain spreading rapidly through phishing emails, fake software cracks, and malvertising campaigns. That malware was Lumma Stealer, a commercially sold infostealer designed to quietly extract sensitive data such as passwords, session tokens, crypto wallets, and authentication cookies from infected machines. Unlike viruses that cause […]
Cybersecurity services are essential for modern digital infrastructure as organizations increasingly adopt cloud environments and remote work, which expand their vulnerability to cyber threats like data breaches and ransomware. Without proper security measures, businesses face financial loss, legal issues, and reputational damage. These services protect networks, endpoints, applications, and data from unauthorized access and are […]
In an increasingly digital world, cyber threats are growing both in number and sophistication. One of the most dangerous forms of malware is the Remote Access Trojan (RAT). These stealthy threats can silently infiltrate your device, giving cybercriminals full control over your system without your knowledge. In this blog, we’ll explore what a RAT is, […]
Cash App is the popular mobile payment application that has revolutionized the way we send and receive money. While Cash App offers simplicity and ease in managing finances, it has also attracted the attention of scammers looking to exploit unsuspecting users. In this guide, we’ve discussed all about how can you get scammed on Cash […]
Crypto.com has emerged as a prominent cryptocurrency platform, offering many services, including trading, staking, lending, and a Visa debit card. With its rapid growth and global user base, questions about its safety and legitimacy are paramount. This article delves into Crypto.com’s security measures, legitimacy, and best practices for users to enhance their security. What Is […]
A watering hole attack is a cyberattack strategy in which the attacker targets a specific group of individuals by compromising a website or online service that they are known to frequent. The name “watering hole” is derived from the concept in nature, where predators wait at watering holes to catch their prey. Similarly, in a […]
How to check for viruses on iPhone
If you are an iPhone user and wonder if your beloved device could catch a digital cold? You’re not alone. With all the buzz about cybersecurity, worrying about your iPhone’s health is natural. But, while iPhones aren’t entirely immune to malware, they’re close. Apple’s tight security approach keeps most nasties at bay. Still, in 2024, […]
What is a Browser Hijacker & how to remove it?
If your browser has been hijacked, you’re not alone. Over 3.2 million people are browsing the internet through compromised browsers right now and most have absolutely no idea they’re being manipulated, tracked, and robbed blind. Browser hijacking is among the most often discussed subjects on computer support message forums. Online browsing is often felt like […]
What to do if you Clicked on a Phishing link
In today’s digital world, phishing attacks are a common tactic used by cybercriminals to trick individuals into giving away sensitive information. These attacks often arrive in legitimate-looking emails, text messages, or websites. But what happens behind the scenes when you click on a phishing link? Let’s break it down. What to do if you clicked […]
You’ve probably come across ID.me at some point when accessing government services or signing up for certain websites. The company verifies people’s identities to help prevent fraud and ensure security, but you may be wondering; is ID.me safe? How exactly does it work, and what does it do with your personal information? ID.me uses technology […]
Discord is a super popular app for text, voice, and video chat on both public and private servers. It started mainly for gamers but has since attracted all kinds of communities, like students, remote workers, and hobby groups. What makes it so appealing is how easy it is to use and set up your own […]
Cryptojacking is a type of cyberattack where hackers secretly use your device’s computing power to mine cryptocurrency. Unlike ransomware or data breaches, it doesn’t steal your data, instead, it slows down your system, drains battery life, and increases energy usage, often without you noticing. This threat has become increasingly common, especially as cryptocurrency values rise. […]
If you’ve been using Discord recently and noticed some strange things happening with your account, there’s a good chance you may have picked up some malware. Discord viruses and hackers are on the rise, targeting users to steal information or use your account for their own purposes. The good news is, there are some steps […]
Transactions in a cashless environment can be completed quickly and easily with the help of contactless scanning. However, the widespread adoption of digital payment systems has prompted new concerns about fraudulent transactions. RFID protection solutions, such as RFID-blocking wallets and passport covers, provide solutions to these issues. However, the technology’s efficacy is crucial to assess. […]
To think of a world without the Internet is to think of a world without information, community, commerce, and entertainment. However, it can also be a risky environment for kids to explore. Every parent wants to do what they can to protect their children from harm, whether from exposure to harmful material or undesired contact […]
Venmo is a great way to pay friends back for dinner or to split the cost of a group gift, but it’s essential to be aware of the different types of Venmo scams that are out there. In this article, you will learn about the different types of Venmo scams and how to protect yourself […]
In the digital age, where nearly every aspect of our lives is intertwined with the internet, cybersecurity has become an increasingly critical concern. Cybercrime, as its name suggests, involves criminal activities that take place in cyberspace, primarily using the internet or computer networks. This type of crime can range from stealing personal data to spreading […]
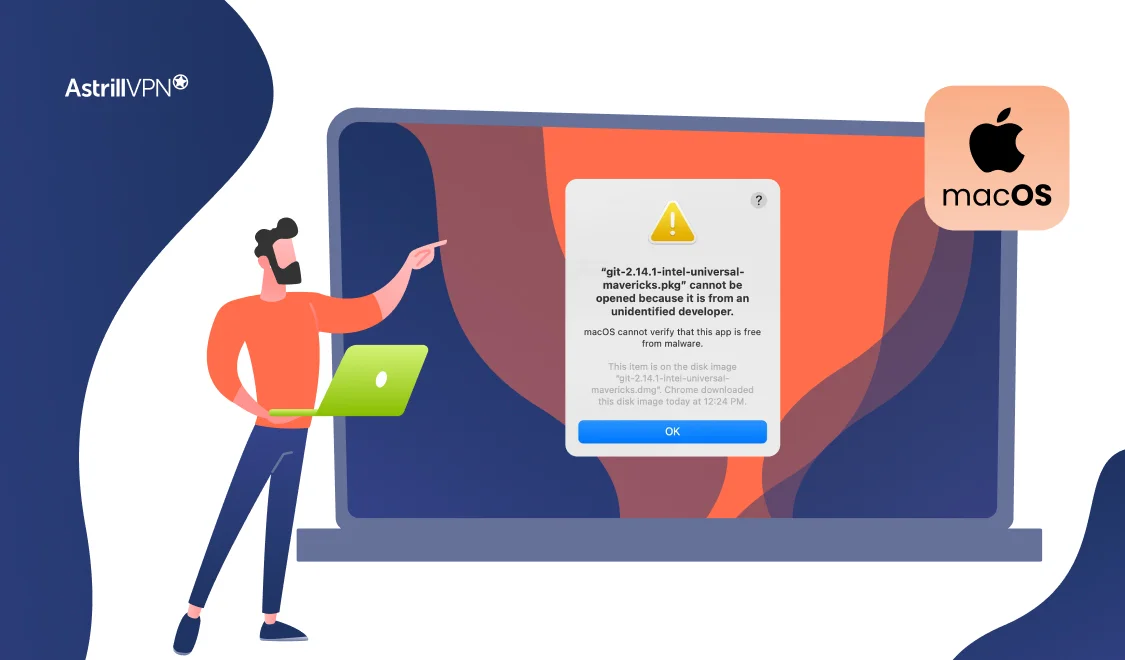
That moment when you try to open a new app and see the warning “macOS cannot verify that this app is free from malware” can be frustrating, but it’s also one of your Mac’s most important security features at work. This safeguard, powered by Apple’s Gatekeeper technology, isn’t just an arbitrary roadblock; it’s a critical […]
Data breaches are no longer rare occurrences but frequent and unsettling events that impact millions of users worldwide. In 2024 alone, companies like T-Mobile, LastPass, and Uber have faced significant data breaches, compromising vast amounts of personal information. These incidents serve as stark reminders of the vulnerability of our digital lives. Maintaining the privacy of […]
If you have considered is opera gx good as your primary web browser then you are on the right track. As a gamer-focused variant of the Opera browser, it offers unique features tailored to enhance your gaming experience. However, before adopting any new software, it’s crucial to evaluate its security measures. We’ll delve into its […]
The Human Firewall: Your First Line of Defense
As cyber threats continue to evolve, your organization’s security depends on more than just technology. You and your employees are the human firewall in cybersecurity – the critical first line of defense against attacks. By cultivating security awareness and best practices across your workforce, you can significantly reduce vulnerabilities and prevent breaches. This article will […]
A baiting attack is a form of social engineering where cybercriminals use enticing offers or items to manipulate victims into compromising their own security. These attacks exploit human curiosity, trust, or greed, often leading to malware infections, data theft, or unauthorized system access. Understanding baiting attacks is critical to staying safe in an increasingly connected […]
What Is The Wacatac Trojan & How To Remove It?
The Wacatac Trojan virus can cause severe damage to your device and compromise your data if action isn’t taken. This virus specifically targets Windows devices; once it enters your device, it can compromise sensitive and confidential data. Suppose you suspect your computer device has been infected with the Wacatac malware. In that case, you must […]
As a technology professional, you’re likely familiar with various cybersecurity threats. However, one often-overlooked danger lurking in your systems could be macro viruses. These insidious programs hide within seemingly innocuous documents, waiting to wreak havoc on your network. The initial macro virus emerged in July 1995, and macro viruses, primarily targeting Word documents, quickly became […]
As you navigate the complex landscape of modern cybersecurity, understanding and combating network security threats is paramount. Your organization’s digital infrastructure faces an ever-evolving array of risks in today’s interconnected world. From sophisticated malware to social engineering tactics, the threats to your network’s integrity are diverse and relentless. This comprehensive guide will equip you with […]
As a cybersecurity professional, you know the ever-present threat of malicious code. From stealthy malware to sophisticated ransomware, nefarious actors constantly develop new ways to infiltrate systems and wreak havoc. To stay ahead of these evolving threats, you need a comprehensive strategy for malicious code detection. This article will equip you with cutting-edge techniques and […]
Streaming media to your TV has never been easier than with a Roku streaming player. When coupled with an internet-enabled device, this streaming stick makes it possible to watch live video from any location. This is why Roku surpassed the 85.5 million active users milestone last month (Q3 2024). In this guide, we have lined […]
In the digital age, your online security is paramount. Yet, lurking in the shadows of the internet is a threat you may not be aware of: packet sniffing. This powerful technique allows cybercriminals to intercept and analyze data transmitted over a network, potentially exposing your sensitive information. As you navigate the online world, understanding packet […]
My email has been hacked! How do i fix it?
Has your email account been compromised? Discovering that your email has been hacked can be a distressing experience. You may feel violated, anxious about what information was accessed, and unsure how to regain control. However, acting swiftly and methodically is crucial to mitigate potential damage and secure your digital presence. This step-by-step guide will walk […]
As cybersecurity threats evolve, you must stay vigilant against new forms of attack. One emerging threat you need to be aware of is quishing, a sophisticated variation of phishing that exploits QR codes to deceive victims. Unlike traditional phishing emails, quishing definition is that it leverages QR codes’ widespread use and convenience to lure you […]
As cybersecurity threats continue to evolve, you must remain vigilant against both digital and physical attacks on your organization. One often overlooked vulnerability is the tailgating attack, where an unauthorized individual gains access to secure areas by closely following an authorized person through a restricted entry point. This deceptively simple tactic can have severe consequences, […]
Phishing emails are a prevalent and dangerous cyber threat, designed to trick recipients into revealing sensitive information like passwords or credit card numbers. These fraudulent messages often mimic trusted sources, making them hard to identify. The goal of phishing is to steal personal or financial data, spread malware, or gain unauthorized access to systems. Cybercriminals […]
Cyber attacks have become increasingly prevalent in recent years, with attackers always looking for new and innovative ways to compromise systems and steal sensitive data. One such attack that has gained notoriety is the Evil Twin Attack, also known as the Evil Twin WiFi Attack. An Evil Twin Attack is a type of cyber attack […]
If you’re surfing the web when suddenly everything slows to a crawl, and Pop-ups bombard your screen with scary warnings that your computer is infected. Well! Could a VPN have stopped this virus attack? We did the digging to find out what does a VPN protect you from. Get ready to separate fact from fiction […]
As you navigate the digital landscape, your online security is constantly threatened. One particularly insidious danger lurking in the shadows is session hijacking. This sophisticated attack can compromise your sensitive data and online identity in mere moments. By intercepting and exploiting your active web sessions, cybercriminals can gain unauthorized access to your accounts, financial information, […]
As you look ahead to 2026, cloud security issues loom large on the horizon. Your organization’s digital assets and sensitive data face an evolving landscape of threats in the cloud environment. From sophisticated cyber attacks to compliance hurdles, you’ll need to navigate a complex array of challenges to keep your cloud infrastructure secure. This article […]
In today’s digital landscape, your organization’s cybersecurity is only as strong as its weakest link. One of the most insidious vulnerabilities you may face is the broken authentication attack. This method exploits flaws in your authentication processes, potentially granting unauthorized access to sensitive systems and data. As a security professional, understanding and mitigating this threat […]
As cybersecurity threats continue to evolve, you need a robust framework to understand and combat adversary tactics. Enter the MITRE ATT&CK framework – a comprehensive knowledge base of cyber adversary behavior. This powerful tool equips you with the intelligence to strengthen your organization’s security posture. In this guide, you’ll explore the intricacies of Mitre ATT&CK […]
Pretexting is a critical cybersecurity threat that focuses on human manipulation rather than technical exploits. Attackers use fabricated scenarios to deceive individuals into revealing sensitive information or granting access to secure systems. Understanding how pretexting works, spotting everyday situations where it pops up, and knowing how to avoid these kinds of attacks can really help […]

























![A Detailed Online Privacy Guide for Staying Safe on the Web [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/10/online-privacy-guide.jpg)