You’ve probably heard of mobile hotspots by now. They’re an amazing way to get online anywhere and can be life-saving when traveling. But what happens if someone gets their hands on your hotspot password? Now, you have to assess whether mobile hotspots are secure. They could potentially harm your privacy. Fortunately, there are several methods […]
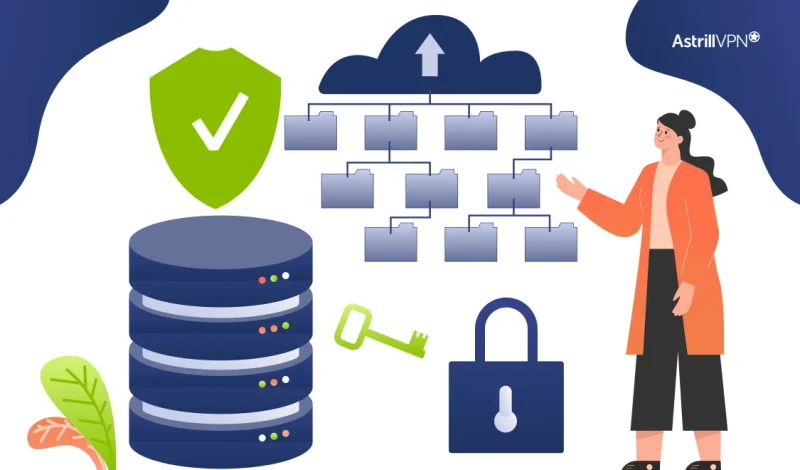
In today’s digital age, you’re constantly sharing sensitive information online. Your data is vulnerable to prying eyes, from credit card numbers to private messages. This is where encryption comes in. Encryption is the process of encoding information, making it unreadable to unauthorized parties. Understanding encryption becomes crucial for protecting your privacy and security as you […]
In the digital age, where nearly every aspect of our lives is intertwined with the internet, cybersecurity has become an increasingly critical concern. Cybercrime, as its name suggests, involves criminal activities that take place in cyberspace, primarily using the internet or computer networks. This type of crime can range from stealing personal data to spreading […]
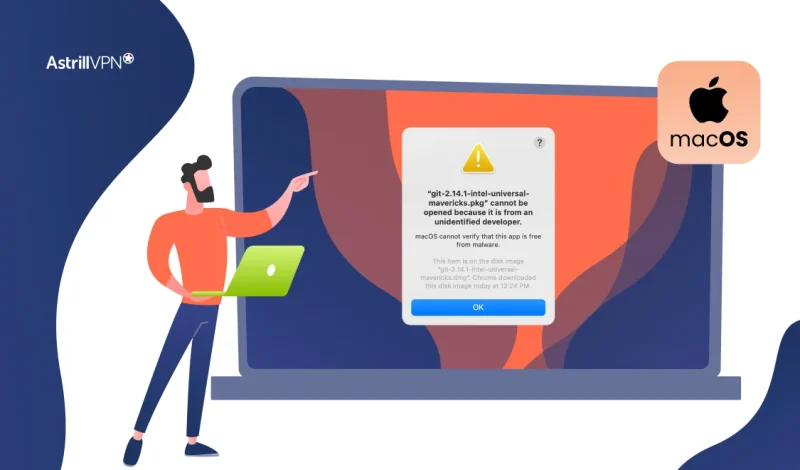
That moment when you try to open a new app and see the warning “macOS cannot verify that this app is free from malware” can be frustrating, but it’s also one of your Mac’s most important security features at work. This safeguard, powered by Apple’s Gatekeeper technology, isn’t just an arbitrary roadblock; it’s a critical […]
In today’s digital age, protecting your privacy, data, and online identity is important. From online banking to online shopping and work-related activities, the internet is full of potential threats that could compromise your personal information. That’s why many people turn to VPNs (Virtual Private Networks) to stay safe while browsing the web. But there is […]
If you have considered is opera gx good as your primary web browser then you are on the right track. As a gamer-focused variant of the Opera browser, it offers unique features tailored to enhance your gaming experience. However, before adopting any new software, it’s crucial to evaluate its security measures. We’ll delve into its […]
The Human Firewall: Your First Line of Defense
As cyber threats continue to evolve, your organization’s security depends on more than just technology. You and your employees are the human firewall in cybersecurity – the critical first line of defense against attacks. By cultivating security awareness and best practices across your workforce, you can significantly reduce vulnerabilities and prevent breaches. This article will […]
A baiting attack is a form of social engineering where cybercriminals use enticing offers or items to manipulate victims into compromising their own security. These attacks exploit human curiosity, trust, or greed, often leading to malware infections, data theft, or unauthorized system access. Understanding baiting attacks is critical to staying safe in an increasingly connected […]
What Is The Wacatac Trojan & How To Remove It?
The Wacatac Trojan virus can cause severe damage to your device and compromise your data if action isn’t taken. This virus specifically targets Windows devices; once it enters your device, it can compromise sensitive and confidential data. Suppose you suspect your computer device has been infected with the Wacatac malware. In that case, you must […]
As a technology professional, you’re likely familiar with various cybersecurity threats. However, one often-overlooked danger lurking in your systems could be macro viruses. These insidious programs hide within seemingly innocuous documents, waiting to wreak havoc on your network. The initial macro virus emerged in July 1995, and macro viruses, primarily targeting Word documents, quickly became […]
As you navigate the complex landscape of modern cybersecurity, understanding and combating network security threats is paramount. Your organization’s digital infrastructure faces an ever-evolving array of risks in today’s interconnected world. From sophisticated malware to social engineering tactics, the threats to your network’s integrity are diverse and relentless. This comprehensive guide will equip you with […]
As a cybersecurity professional, you know the ever-present threat of malicious code. From stealthy malware to sophisticated ransomware, nefarious actors constantly develop new ways to infiltrate systems and wreak havoc. To stay ahead of these evolving threats, you need a comprehensive strategy for malicious code detection. This article will equip you with cutting-edge techniques and […]
Streaming media to your TV has never been easier than with a Roku streaming player. When coupled with an internet-enabled device, this streaming stick makes it possible to watch live video from any location. This is why Roku surpassed the 85.5 million active users milestone last month (Q3 2024). In this guide, we have lined […]
As you navigate the digital landscape, your organization’s cybersecurity is constantly under threat. One particularly insidious danger lurking in the shadows is DNS hijacking. This malicious attack can redirect your web traffic, compromise sensitive data, and damage your reputation, all while operating largely undetected. Understanding the mechanics of DNS hijacking and implementing robust defense strategies […]
In the digital age, your online security is paramount. Yet, lurking in the shadows of the internet is a threat you may not be aware of: packet sniffing. This powerful technique allows cybercriminals to intercept and analyze data transmitted over a network, potentially exposing your sensitive information. As you navigate the online world, understanding packet […]
Most countries have a variety of internet service providers to choose from, each with its own set of pricing packages, download limits, access methods, and routing technology. How to Check Your ISP? If you are wondering, “Who is my internet service provider” then you can follow these steps: Who Can See Your ISP? If you […]
My email has been hacked! How do i fix it?
Has your email account been compromised? Discovering that your email has been hacked can be a distressing experience. You may feel violated, anxious about what information was accessed, and unsure how to regain control. However, acting swiftly and methodically is crucial to mitigate potential damage and secure your digital presence. This step-by-step guide will walk […]
In today’s digital age, you’re likely familiar with various cybersecurity threats. However, one increasingly prevalent danger may have escaped your notice: smishing. This malicious tactic combines “SMS” and “phishing,” referring to fraudulent text messages designed to deceive you into divulging sensitive information. This is also called SMS phishing. Understanding smishing and how to protect yourself […]
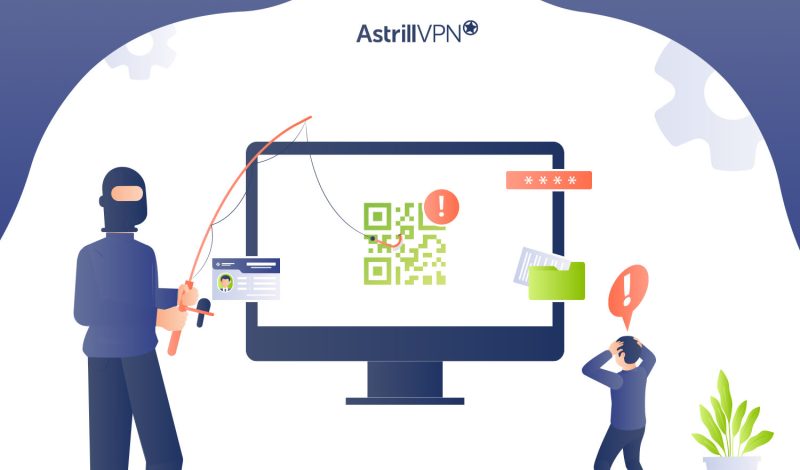
As cybersecurity threats evolve, you must stay vigilant against new forms of attack. One emerging threat you need to be aware of is quishing, a sophisticated variation of phishing that exploits QR codes to deceive victims. Unlike traditional phishing emails, quishing definition is that it leverages QR codes’ widespread use and convenience to lure you […]
As cybersecurity threats continue to evolve, you must remain vigilant against both digital and physical attacks on your organization. One often overlooked vulnerability is the tailgating attack, where an unauthorized individual gains access to secure areas by closely following an authorized person through a restricted entry point. This deceptively simple tactic can have severe consequences, […]
In the current era, privacy is more important than ever, and digital privacy must be protected at all costs. Just like that, your browsing history is precious data. It can reveal much about you, your interests, and your political views. Before reaching any website, all of this must pass through your trusted internet service provider […]
Phishing emails are a prevalent and dangerous cyber threat, designed to trick recipients into revealing sensitive information like passwords or credit card numbers. These fraudulent messages often mimic trusted sources, making them hard to identify. The goal of phishing is to steal personal or financial data, spread malware, or gain unauthorized access to systems. Cybercriminals […]
Cyber attacks have become increasingly prevalent in recent years, with attackers always looking for new and innovative ways to compromise systems and steal sensitive data. One such attack that has gained notoriety is the Evil Twin Attack, also known as the Evil Twin WiFi Attack. An Evil Twin Attack is a type of cyber attack […]
If you’re surfing the web when suddenly everything slows to a crawl, and Pop-ups bombard your screen with scary warnings that your computer is infected. Well! Could a VPN have stopped this virus attack? We did the digging to find out what does a VPN protect you from. Get ready to separate fact from fiction […]
As you navigate the digital landscape, your online security is constantly threatened. One particularly insidious danger lurking in the shadows is session hijacking. This sophisticated attack can compromise your sensitive data and online identity in mere moments. By intercepting and exploiting your active web sessions, cybercriminals can gain unauthorized access to your accounts, financial information, […]
As you look ahead to 2025, cloud security issues loom large on the horizon. Your organization’s digital assets and sensitive data face an evolving landscape of threats in the cloud environment. From sophisticated cyber attacks to compliance hurdles, you’ll need to navigate a complex array of challenges to keep your cloud infrastructure secure. This article […]
In today’s hyper-connected digital landscape, your devices face constant threats from malicious software. Malware, short for “malicious software,” encompasses many harmful programs to infiltrate and damage your computer systems. These digital threats can compromise your data, financial information, and overall cybersecurity, from viruses and worms to trojans and ransomware. Understanding the various types of malware […]
In today’s digital landscape, your organization’s cybersecurity is only as strong as its weakest link. One of the most insidious vulnerabilities you may face is the broken authentication attack. This method exploits flaws in your authentication processes, potentially granting unauthorized access to sensitive systems and data. As a security professional, understanding and mitigating this threat […]
As cybersecurity threats continue to evolve, you need a robust framework to understand and combat adversary tactics. Enter the MITRE ATT&CK framework – a comprehensive knowledge base of cyber adversary behavior. This powerful tool equips you with the intelligence to strengthen your organization’s security posture. In this guide, you’ll explore the intricacies of Mitre ATT&CK […]
Pretexting is a critical cybersecurity threat that focuses on human manipulation rather than technical exploits. Attackers use fabricated scenarios to deceive individuals into revealing sensitive information or granting access to secure systems. Understanding how pretexting works, spotting everyday situations where it pops up, and knowing how to avoid these kinds of attacks can really help […]
As a cybersecurity enthusiast, you’re likely all too familiar with the devastating potential of remote code execution (RCE) attacks. In an increasingly interconnected digital landscape, RCE vulnerabilities pose a significant risk to organizations of all sizes. This article will equip you with the knowledge and tools to effectively detect, prevent, and mitigate RCE attacks. By […]
In today’s interconnected world, your organization’s digital infrastructure is both its greatest asset and its most vulnerable target. As cyber threats evolve and multiply, safeguarding your network has become more critical than ever. By implementing robust monitoring protocols, you can stay one step ahead of malicious actors, protect sensitive information, and maintain the trust of […]
Social media has become the new normal, allowing people to connect with friends, family, and others from all across the globe, get updated on the latest news, and use it for entertainment purposes and to promote their businesses and whatnot. But even though social media does offer a lot of benefits to users, it also […]
What is AES Encryption: How It Secures Your Data
AES encryption is a critical component of modern cybersecurity. It protects sensitive data in a wide range of applications, from securing online transactions to protecting confidential communication across networks. Its widespread use and proven effectiveness have made it the standard for encrypting data in transit and at rest. In this guide, we’ll explore AES, how […]
What is a spam risk call and How to avoid it?
As our lives become more and more dependent on technology, protecting our devices from cyber threats is more critical than ever. One common annoyance that many of us face are spam phone calls, which can range from annoying telemarketers to dangerous scammers trying to steal our personal information. Follow this guide to learn what dies […]
Data exfiltration is the unauthorized transfer of sensitive data from an organization’s network to an external location. Unlike data breaches, which often involve data exposure due to security gaps, data exfiltration in cyber security is typically a deliberate act carried out by cybercriminals or malicious insiders. This can involve various methods, such as using malware, […]
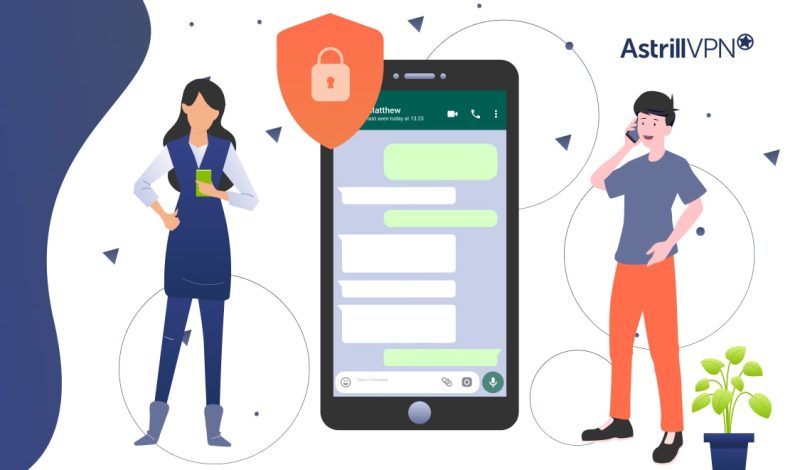
In today’s digital age, you rely on messaging apps to stay connected with friends, family, and colleagues. With its widespread popularity, WhatsApp likely plays a significant role in your daily communications. But as cyber threats evolve and privacy concerns grow, you may question the safety and security of this platform. As we enter 2025, it’s […]
FileRepMalware is a type of malware detected by antivirus programs under the “FileRep” classification. Its suspicious traits characterize it, and it may lack a known signature in malware databases. This classification aids in identifying new threats. FileRepMalware is often linked to files from unknown sources that resemble legitimate software, making detection difficult. Its impact can […]
As a cybersecurity professional, you’re likely familiar with the persistent threat of social engineering attacks. These sophisticated schemes exploit human psychology rather than technical vulnerabilities, making them particularly challenging to defend against. In today’s interconnected business landscape, your organization faces an ever-present risk of falling victim to these insidious tactics. This article will equip you […]
Cross-site scripting (XSS) is a prevalent security vulnerability in web applications. It occurs when an attacker injects malicious scripts into otherwise benign and trusted websites. These scripts are executed in the victim’s browser, leading to potential security breaches, data theft, and unauthorized access. XSS typically exploits vulnerabilities in input validation and output encoding, making it […]
Is Zelle Safe To Use In 2025? Let’s Find Out
Zelle is a popular payment platform with a staggering $806 billion transaction volume, a 28% increase from last year. It is also set to expand at a growth rate of 20% in the next five years. Zelle allows free instant transfers from the app. As companies strive to enhance the customer experience and make things […]
As a business owner or financial professional, you understand the critical importance of protecting your organization from fraud. But do you truly grasp how modern fraud detection systems work to safeguard your assets? These sophisticated tools leverage advanced analytics and machine learning to identify suspicious patterns and anomalies that may indicate fraudulent activity. By understanding […]
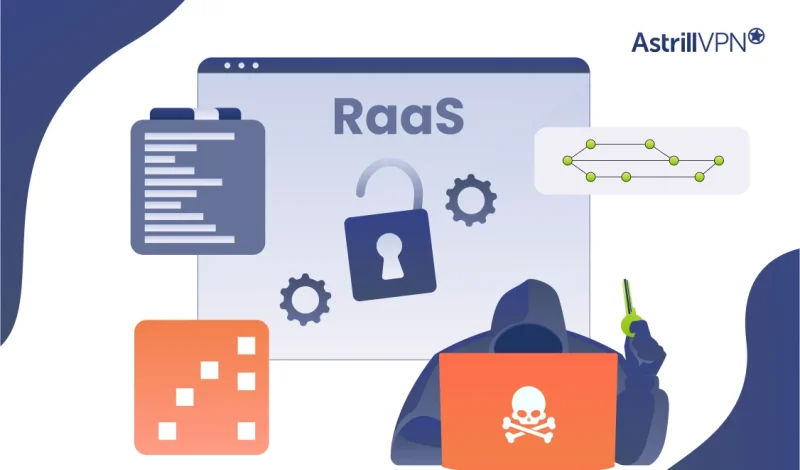
Ransomware-as-a-Service (RaaS) represents a transformative evolution in the cybercrime landscape. By operating as a subscription-based model, RaaS provides cybercriminals with ready-made ransomware tools, significantly lowering the barriers to launching attacks. This “ransomware marketplace” allows even inexperienced actors to execute complex attacks, leading to a surge in ransomware incidents globally. The impact of RaaS is felt […]
If you are a Telegram user, be warned as scammers are increasingly targeting this popular messaging app. As Telegram’s user base grows, so do the sophisticated schemes designed to exploit unsuspecting individuals. From fake investment opportunities to phishing attempts, the threats are diverse and ever-evolving. You may think you’re too savvy to fall victim, but […]
Have you heard about the Booksi scam that’s been making waves online? As an avid reader, you may be tempted by deals that seem too good to be true. Unfortunately, scammers are targeting unsuspecting bibliophiles through fake websites and social media accounts. These fraudulent operations promise rare books and incredible discounts, only to leave you […]
As you rely more on your smartphone for banking, social media, and other sensitive accounts, you may be vulnerable to an insidious identity theft known as the SIM swap attack. This increasingly common scam allows criminals to hijack your phone number and gain access to your most valuable online information. By understanding how these attacks […]
Crypto scams have surged in recent years, leaving countless individuals vulnerable to fraud in the fast-evolving world of digital currencies. As cryptocurrency continues to gain popularity, so do the scams targeting unsuspecting investors. In this guide, we’ll explain the most common types of crypto scams, how to spot them, and the essential steps to protect […]
As cybersecurity threats evolve, you must stay vigilant against increasingly sophisticated attacks. Spear phishing in cybersecurity is one of the most targeted and dangerous forms of social engineering. Unlike broad phishing campaigns, spear phishing attacks are personalized to exploit your specific vulnerabilities. By understanding how these attacks work and cybercriminals’ techniques, you can better protect […]
How to know if your Instagram is hacked?
In today’s digital age, your Instagram account is more than just a social platform. It’s a personal brand, a business tool, and a digital extension of yourself. Recognizing the signs of Instagram hacking is crucial for protecting your online presence and personal information. This article will guide you how to know if your Instagram is […]
In today’s digital world, it is important to be aware of our online privacy since prying еyеs arе always on thе watch. One of the most common types of harmful software that jeopardizes our privacy is spywarе. It is a long-standing and ever-present danger that may silеntly infiltratе our dеvicеs, resulting in unlawful acts such […]