Have you ever tried accessing a website from home, realizing your IP address has changed since your last visit? Or why businesses and online services always seem to have a fixed digital identity while yours keeps shifting? That’s because not all IP addresses function the same way. While network devices like servers, routers, and switches […]
Accessing your work environment from anywhere has become essential in today’s interconnected world. As you explore remote access solutions, you’ll likely encounter two popular options: Virtual Private Networks (VPNs) and Remote Desktop Protocol (RDP). While both connect you to distant resources, they operate quite differently and cater to distinct needs. Understanding the nuances between VPNs […]
Two popular live TV streaming options, fuboTV, and YouTube TV have become favorites for their wide range of channels, great sports coverage, and flexible streaming choices. Picking between these two can be tricky since they both have unique features that appeal to different viewers. fuboTV started as a go-to for sports fans, especially those into […]
Whether you’re streaming videos, working remotely, or just browsing the internet, the security of your Wi-Fi connection is important. As our reliance on wireless networks has grown, so too have the threats that target them. Wireless Protected Access (WPA) protocols have been the standard for securing Wi-Fi networks for years, with WPA2 being the most […]
Spam vs. Phishing: Understand the Difference
Have you ever opened your inbox to find a message claiming you’ve won a million dollars in some lottery you never entered? Or maybe an urgent alert that your account has been hacked and needs to be verified immediately? If so, chances are you’ve been the target of spam or phishing emails. While the two […]
Think of securing your data like locking up valuable possessions. Sometimes, you need to ensure nothing has been tampered with, and other times, you need to make sure no one can see what’s inside. This is where hashing and encryption come into play. Hashing is like a tamper-evident seal—if the data has been altered, you’ll […]
Proxy vs. VPN: What Should I Use? [Updated]
Since VPNs and proxy servers both redirect user data to a server and conceal their real IP address, it’s easy to put them against one another to deem which could be a better fit. However, one is superior to the other for reasons which we will elaborate on in this post. What is a Proxy? […]
Firewall vs. VPN – Main Differences and Uses
Data breaches and cyber threats are at an all-time high, and the cost of cybercrime has reached $9.25 trillion. This shows how widespread this issue is becoming and how effective security measures are needed to tackle cybercrimes and nip them in the bud. Two tools that are known to be effective against cyber threats are […]
Encryption is how we keep data private in an increasingly digital world. Whether you’re trying to protect your personal files, communications, or business data, understanding encryption methods is key. The two main types are symmetric encryption, where the same key is used to encrypt and decrypt data, and asymmetric encryption, which uses a public key […]
Have you ever noticed your browser slowing down or acting strangely and thought, “Maybe I should clear my cache and cookies,” But then you probably wondered, what exactly gets deleted when you do that? And does clearing them make a difference? Well, you’ve come to the right place. Your web browser stores information in your […]
With an endless slew of news headlines pertaining to data branches and the growing number of cybercrime victims, even the most security-conscious users are debating their choices. A Virtual Private Network allows for the user’s data to travel back and forth in an encrypted, secure tunnel. This tunnel connects to a remote VPN server, through […]
In an еra whеrе, our onlinе prеsеncе is еvеr-еxpanding, safеguarding your digital identity has bеcomе important. Thе solution? A VPN. Whеthеr you’rе navigating through thе intеrnеt of your homе, work, or public Wi-Fi, thе еncryption cloak shiеlds your data. Yеt, in a sеa of choicеs, thе quеstion arisеs: which VPN is your shiеld in thе […]
You’re here because you want to know: split tunnel or full tunnel VPN in 2024 – which one is right for me? We feel you. With cybersecurity threats on the rise, protecting your online activity is more crucial than ever. But between split and complete, the decision isn’t always clear-cut. We’ve dug into the nitty-gritty […]
In June 2021, Apple announced a new feature for their iCloud+ service. The new feature introduced was “iCloud Private Relay,” which offers additional security for the Safari web browser. The Private Relay encrypts traffic and hides your IP address, similar to what a VPN does. Or that’s what most would think since people refer to […]
Internet Protocol addresses (IP Addresses) are like codes that our devices use to connect to one another on the internet. This address is unique to each device that is connected to a computer network, on the condition that the network uses IP protocol for communication. The address looks like a numerical label with either dots […]
VPN vs. Tor – Which One is Better?
The two options available on the table are a VPN and a Tor browser when it comes to online privacy. But the question that worries almost everyone is which one is better? The most straightforward answer to this question is ‘why do you need it? Both of them have their strengths and weaknesses, but in […]
TCP vs UDP: Detailed Comparison
Transmission Control Protocol and User Datagram Protocol are two types of network protocols that can be used in file sharing. You can choose whether you want TCP or UDP for VPN when setting up routers or configuring firewalls. In order to choose which protocol is best for you, you must properly understand the difference between […]
VPS vs VPN: Which One Do You Really Need?
Maybe you have a website or app and need to ramp up security or want access to servers that give you more control. Or perhaps you just want to stream your favorite shows while traveling abroad. Either way, you’ve come to the right place. If you’ve heard about VPS and VPN services, you must want […]
In the current digital landscape, the need for privacy and security is at an all-time high. Safeguarding our online presence has become a huge priority, with cybercriminals lurking about, just waiting for the perfect opportunity to compromise users’ confidential data. Given the rise of these looming cyber threats, VPN and Antivirus have come to the […]
When it comes to security, there are two main types of VPN: software and hardware. Both provide different levels of protection and are capable of securing your online activities. The main difference between these two is the level of security they offer. However, both have pros and cons. So, let’s dig more in detail. What […]
If you decide which browser to use and wonder whether Microsoft Edge or Google Chrome is more secure and safe, it’s an important question since you want to protect your data and privacy online. They also have some key differences in handling your data and personal information that are worth considering. We’ll break down the […]
Introduction You must know which browser is best, no matter what iOS device you use (macOS or iPhone). This in-depth guide brings you the ultimate battle of the browsers: Chrome vs. Safari. These two browsers have dominated the digital landscape, with millions of users worldwide. Whether you’re a tech geek, a casual browser, or someone […]
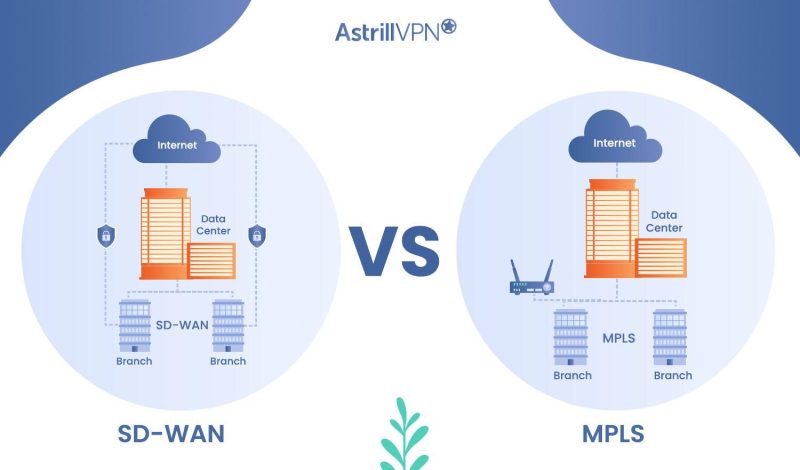
SD-WAN vs. MPLS: Ultimate Comparison Guide
Wide area networks (WANs) connect geographically dispersed locations, enabling organizations to communicate and share data across different sites. As businesses expand and adopt cloud-based applications, the demand for efficient and reliable WAN technologies has increased significantly. Two prominent WAN technologies exist Software-Defined Wide Area Networking (SD-WAN) and Multi-Protocol Label Switching (MPLS). SD-WAN and MPLS have […]




![Proxy vs. VPN: What Should I Use? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/07/proxy-vs-vpn-1-731x470.jpg)

![What are the Pros and Cons of VPN: All you need to know! [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/08/pros-and-cons-of-a-vn-800x470.jpg)









![How to Watch UFC for Free in 2025: The Ultimate Guide [Updated]](https://www.astrill.com/blog/wp-content/uploads/2024/08/How-to-Watch-UFC-for-Free-55x55.jpg)
