What is a Browser Hijacker & how to remove it?

Bisma Farrukh

Browser hijacking is among the most often discussed subjects on computer support message forums. Online browsing is often felt like a threat because of unwanted app installation that might turn out to be malware.
There are many different types of attacks, and the one attacking your browser is called Browser hijacking. Most of the time, computer users are interested in learning to safeguard themselves from hostile invasions and outside manipulation. If you are looking for detailed answers to it, here is a short guide for it.
Table of Contents
What is a browser hijacker?
A browser hijacker is “unwanted software that changes a web browser’s settings without the user’s permission.” The end consequence is the introduction of unwanted advertising into the browser and, in certain cases, substituting the hijacker website for the browser’s default home page or search engine.
The plan is to force visitors to visit specific websites whether they want to or not to increase the hijacker’s advertising revenue. Additionally, spyware that collects banking information and other sensitive data may be included in browser hijackers.
How does browser hijacking work?
Your device can be infected with a browser hijacker in several ways.
- This can be done by installing shareware or freeware.
- Additionally, some software, add-ons, or plugins that allow advertisements may also contain browser hijacking code that will be activated once the add-on is installed.
- Once browser-hijacking malware has gained access to your device, it may set up spyware or adware (apps that track your online activities and ad pop-ups that reward the hacker each time you click).
Your computer may become infected with more malware after being redirected to questionable websites by a browser hijacker. Additionally, they might mine your internet activity and browsing history and sell it as metadata without your consent.
The impact and risk of browser hijacking
Some marketers trick you into clicking their ads to make you install suspicious software into browsers for several reasons:
- To obtain information from customers.
- To spy on users.
- To show relentless marketing.
- To hard market a product to a customer with a try-before-you-buy policy.
To remove browser hijacking, you need to know the different steps of cleaning your browsers and devices. We will talk about it later.
How do these hijackers attack your computer?
On rare occasions, hackers will introduce malware into users’ browsers, leading them to websites where private information about them is gathered.
- The data could contain user names, passwords, full names, addresses, social security numbers, and even the answers to security questions, such as the mother’s maiden name.
- Cybercriminals then use the data to access the victim’s online accounts. Rarely can they obtain financial data and steal someone’s money or identity.
- To install the software in a user’s browser, you don’t need to be a super criminal. Some marketing firms follow online behavior in the same ways to track which websites people visit and how long they stay on those web pages. They either use the data to target their advertising efforts or sell it to other businesses that use it to narrow the scope of their marketing materials.
- On display adverts that appear on users’ devices or messages that “follow” people online, businesses occasionally invest their advertising budgets.
- More and more often, even after users reply to the adverts or offers, pixels from websites advertising goods or services remain in users’ browsers.
- The most harmful type of browser hijacking is when a vendor injects an unapproved new software package into the browser. The invasive application might occupy a sizable portion of the browser’s toolbar.
- The goal is typically to persuade the user to purchase a full version of some program, purchase on a retailer’s website, or conduct a search using a particular search engine.
- Whether the files are malicious, they occupy storage space and slow down computer operations. To remove these files from their systems, users must be diligent.
Read Also: How to get rid of Yahoo search from Chrome?
How do browser hijackers infect devices?
It can infect devices in many different ways, and it can be through different online attacks. Famous examples include seemingly innocent toolbars and browser extensions that secretly track your online behavior and sell your data.
However, the threat goes beyond add-ons that trick users into downloading malicious software. It’s not necessarily required to go through any multi-stage installation process for hijacking software to infiltrate your browser. Cybercriminals are skilled at harvesting clicks with deceptive phishing emails containing faulty links or files because sometimes all it takes is one click.
It should be no surprise that downloads from questionable websites for file-sharing and other parts of the internet are a major source of infection. While malicious websites are frequently built to disseminate browser hijackers, even completely legitimate websites can be taken over by hackers who infect the site with malware, possibly putting every visitor in danger.
How to Get Rid of Browser Hijackers on MacOS?
If you think your mac browser is infected with the Browser Hijacker, here is a 2-step browser hijacker removal process to remove the browser hijackers on Mac systems.
Step 1. Remove programs, apps, and add-ons from Mac
- Navigate to Finder and choose Applications.

- To uninstall a program or application, click its icon and drag it to the Trash.
- After that, remember to empty your trash.
Step 2. Restart your Mac in safe mode
Follow these steps to restart your Mac in safe mode.
- Turn off your Mac.
- The restart of your Mac should take 10 to 15 seconds. Holding down the Shift key while restarting should display the login screen.
- Congratulations! Now that you’re in safe mode.
How to get rid of Browser Hijackers on Windows?
You can be quite frustrated with windows causing trouble because of browser hijackers. To solve your problem, follow the steps below:
- After determining the most likely offender, click the Windows start button in the bottom-left corner of your screen and use the search bar to locate the Control Panel.
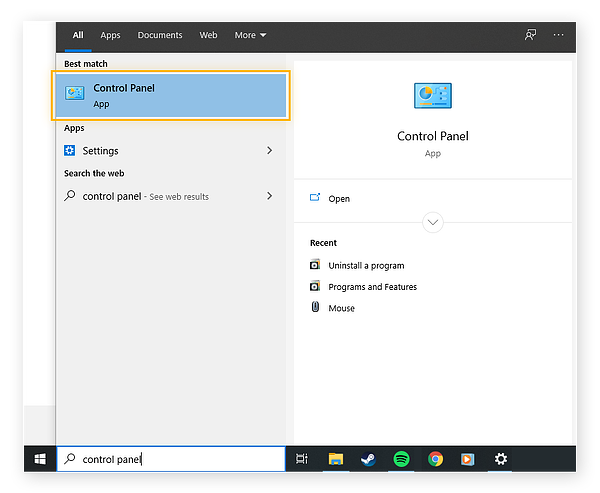
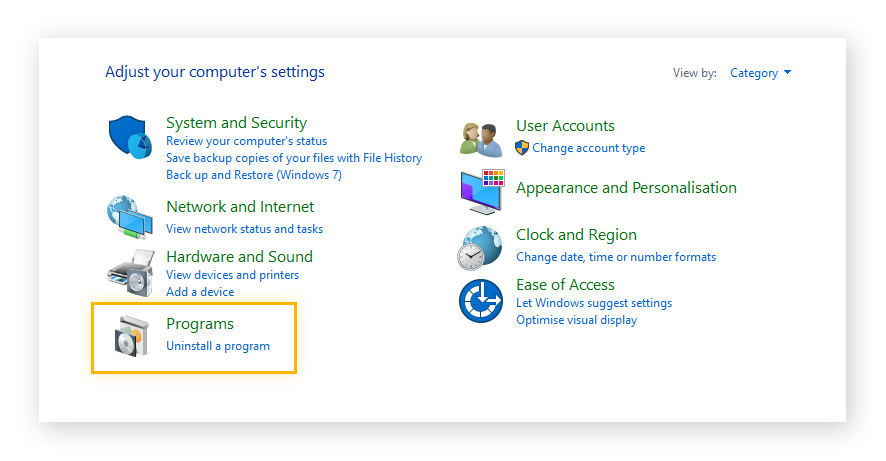
- Click Uninstall software in the Control Panel’s Programs area.
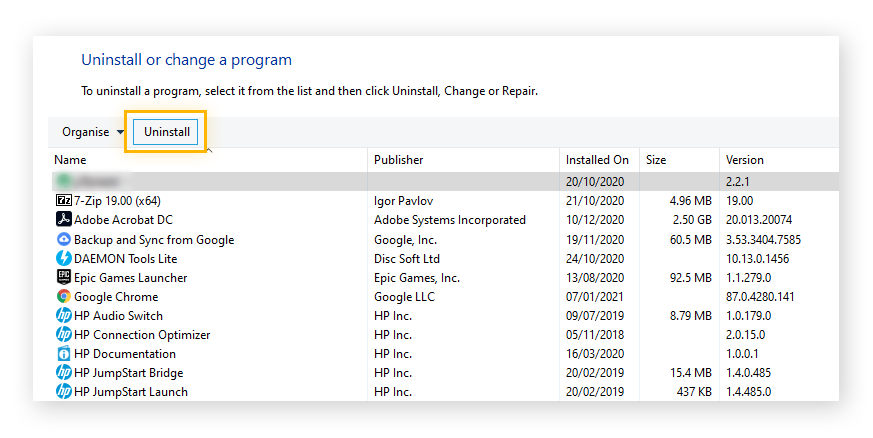
- Click the Uninstall button after selecting the program you want to uninstall. The program or app may ask you to confirm your want to uninstall it.
How to get rid of Browser Hijackers on Android?
Browser hijackers can also enter your Android devices. To get of them from there, follow the steps below:
- Go to the settings menu by tapping on the icon in the notification bar’s top right corner.
- Use the built-in search engine or scroll down to that area to locate Apps.
- Examine all of your apps to discover the malicious malware. How do you know it’s the one? Any programs that you don’t remember downloading or that don’t seem authentic should be avoided. Camera, weather, and photo-editing apps sometimes hide several hazardous ones.
- tap on an app to delete it.
- Select Uninstall from the bottom menu when the details have opened.
How to tell if you have a browser hijacker?
There are the following telltale signs that can indicate that you have a browser hijacker:
- Your home page has changed, or the appearance of strange toolbars are the two most evident signs that your browser has been misused.
- You might also discover new favorites or bookmarks if you manually browse the bookmarks or if you look just below the URL bar.
- Your internet sessions appearing to be substantially slower could be another indication that something has infiltrated the system.
- It’s conceivable that you’ve switched from your former favored search engine to one that directs you to irrelevant results.
- Choose “Settings” from the menu that appears when you click the three vertical dots in the top right corner of the browser window to view Chrome’s default search engine.
- To view the options, scroll down to the “Search engine” column.
- If it doesn’t mention Google, you may change it by clicking on it and selecting Google from the list of possibilities.
- Click “Manage search engines” while you’re there to receive a list of all the search engines you can set as your default.
You can remove any items in the top section, not by Google itself. Simply by clicking on the three vertical dots to the right of each entry, remove them. If you need help, be sure to check your extension.
How to remove a browser hijacker?
The removal of browser hijackers can be rather simple. Installing and running antivirus or anti-malware software on the user’s compromised PC can instantly remove all related files and registry alterations.
The majority of the time, automated solutions are employed to combat persistent hijackers; however, users can manually re-customize themselves for other types that often affect browser settings. Regular users shouldn’t attempt manual system repairs since there are risks involved in tampering with the system registry and HOSTS file.
How to prevent browser hijacking?
One of the most important points is to be safe when surfing online or at least use a VPN for a safe connection. You can also prevent browser hijacking by following these tips:
- Prevent browser hijacking by avoiding dubious downloads and web pages.
- Free software frequently includes browser hijacking software, which may be unpacked and installed without your knowledge.
- Regular browser cleaning can eliminate any browser-hijacking add-ons, extensions, and plugins that snuck onto your browser without your knowledge.
- Stay safe when using public Wi-Fi in cafes or other internet hotspots to conduct business. Networks that are not secure can be exposed.
Can VPN help in preventing browser hijackers?
Yes. Although browser hijackers may appear safe programs bundled with reliable software, you should never install unknown programs on your device. You might be allowing other malware infections, leading to everything from minor annoyances to serious identity theft.
As a result, using VPN is safe. A VPN can protect your data and help you hide your identity whenever you are browsing. Free VPNs should still be avoided since using them puts your system data in danger.
Using a premium VPN such as Astrill VPN helps you browse safely. Astrill VPN offers features like a kill switch, website, and App filter to keep your online safety intact. Both help you stay away from harmful websites, and in case you lose the connection, the kill switch immediately logs you out of any websites for data protection. The premium tools like VPN leak test, Password leak test and DNS leak test help you know about data leakage, if there is any.
Well known Browser hijacker Examples
Browser hijackers are malicious programs that take control of your web browser without permission. They are often installed through vulnerabilities, drive-by downloads, or bundled with other free software.
Some of the most well-known browser hijackers include:
Baidu Search Assistant
This hijacker takes over your default search engine and homepage, redirecting them to Baidu search. It is often bundled with other free software.
SweetPacks
This hijacker installs unwanted toolbars, extensions and applications. It changes your default search engine, homepage and new tab page.
Conduit
Conduit hijacks your browser settings and installs unwanted toolbars like the Conduit toolbar. It is difficult to fully remove.
Ask
The Ask toolbar is installed without permission and hijacks your default search engine and homepage. It is known for being hard to uninstall.
Blekko
This hijacker installs the Blekko search toolbar and changes your default search engine and homepage. It also shows unwanted ads.
Leapforce
Leapforce is a toolbar that tracks your browsing activity to provide targeted ads. It can be pre-installed on some computers and is not easy for average users to uninstall.
BestSearch
BestSearch changes your default search engine and installs unwanted toolbars. It may come bundled with other free software you download.
Babylon Toolbar
The Babylon toolbar tracks your browsing history to provide targeted ads. It can be tricky for non-technical users to fully remove from your system.
Those are some of the most common browser hijackers that users encounter. They can slow down your computer and compromise your privacy and security.
FAQs
● How to remove browser hijacker from Chrome?
Resetting Google Chrome is one technique to eliminate any adware or malicious hijackers. When resetting Chrome’s settings, the browser will eliminate hijackers and return to using Google as its default search engine.
- Launch Google Chrome on your computer.
- In the top-right corner, click the three dots menu.
- Launch Settings.
- From the left sidebar, choose Reset settings.
- Confirm your choice by clicking “Restore settings to their original defaults.”
● Is browser hijacking common?
The prevalence of browser hijacking is declining, particularly if you use Windows. Applications cannot modify a web browser without the user’s authorization in Windows 10. Hackers can still get around it, as with every security measure. The spyware is still there even though you might see it less frequently.
● Why does my browser keep getting hijacked?
The browser hijacking malware may be present in the app or a browser plugin. Additionally, shareware, freeware, adware, and spyware infections can result in browser hijackers. Customers could unwittingly download browser hijackers.
● Has my IP been hacked?
Your access to certain services could be blocked if someone knows your IP address. In dire circumstances, a hacker could be able to pass for you. However, changing your IP address will take care of the issue.
● How do you tell if Chrome has been hijacked?
- redirecting searches to different websites.
- advertising pop-ups in multiples.
- sluggish websites.
- You now have a new search engine.
- On your internet browser, one or more unwelcome toolbars emerge.
● What are some of the common browser hijackers?
The Babylon Toolbar, Conduit Search or Search Protect, CoolWebSearch, SourceForge Installer, OneWebSearch, Snap.do, and Sweet Page are a few of the most well-known hijackers on the Internet.
● Can hackers still hack you with VPN?
No, they cannot hack you because a VPN makes you anonymous. Anyone listening in on your connection may be able to see your traffic and personal information if you are not using VPN.
Conclusion
However, free VPNs should still be avoided since using them puts your system data in danger. If you are looking for professional assistance and guidance, you can always refer to the VPN vendors. So, start looking for the most suitable packages for your VPN and antivirus now and keep your browser or system safe while connecting online.

No comments were posted yet