Blogs Posted by Bisma
If you have just touched down in Australia and can’t access Hulu then don’t freak out when you are unable to watch your beloved Hulu shows. In this article, we will walk you through the steps to accessing Hulu’s massive library from the Land Down Under. Get ready to keep binging Handmaid’s Tale, catch up […]
Have you ever gone to watch that music video or how-to clip on YouTube, only to get the dreaded “This video is not available in your country” message? Well, it’s kind of annoying that you don’t know why Youtube is blocked. But don’t worry, you don’t have to miss out on all those blocked videos […]
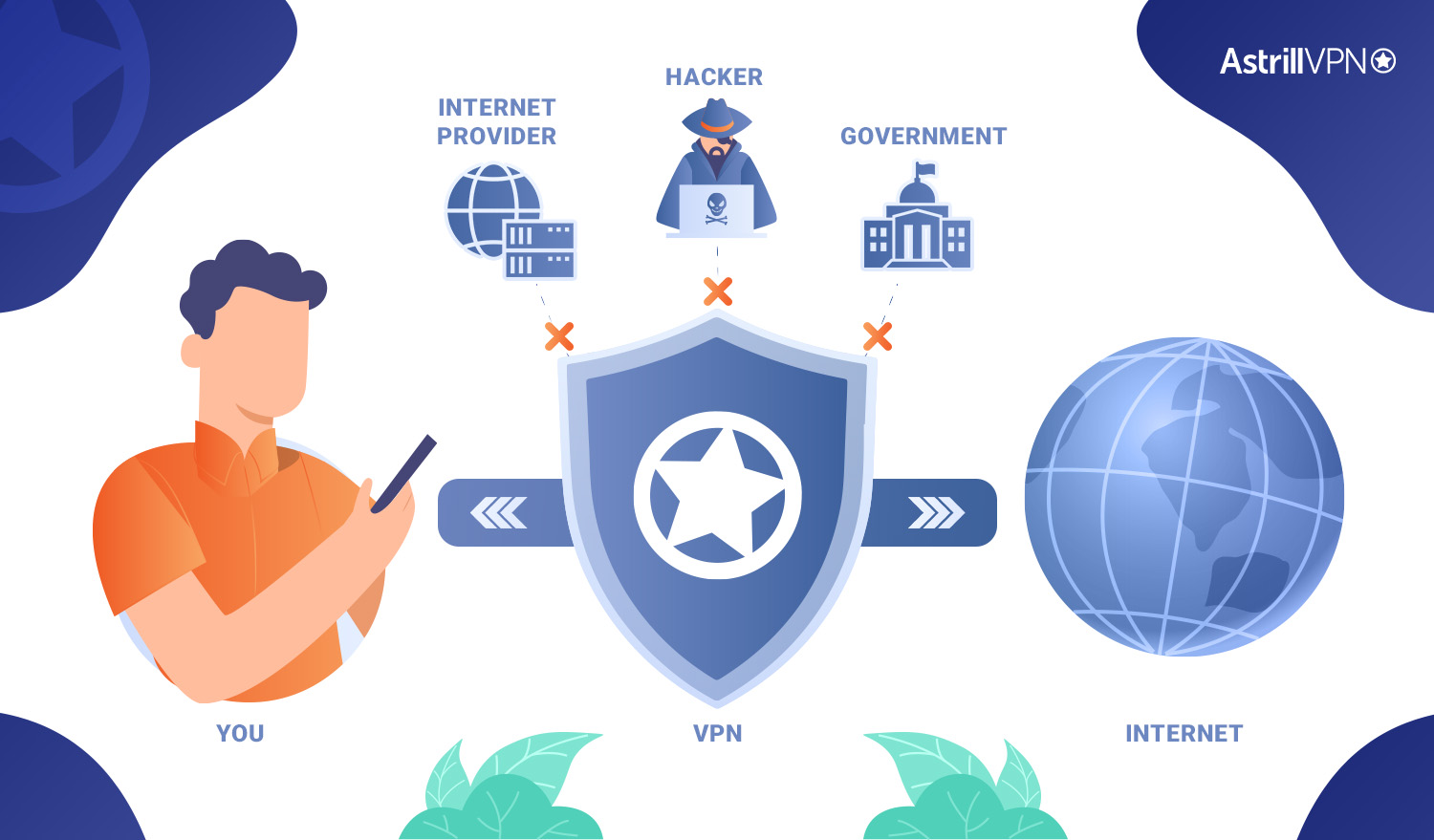
If you have heard people talking about using a VPN to protect their data, a friend may have recommended it, or maybe you’ve seen ads for different VPN services. There are several benefits of VPNs. We must discuss what a VPN can do for your digital security and privacy. A Virtual Private Network (VPN) keeps […]
To suggest that tunneling protocols are what stand between hassle-free, secure B2B transactions and complete anarchy is not an exaggeration. As data travels through Virtual Private Networks, these crucial protocols build secure “tunnels” that include encrypted data (VPNs). Theoretically, they protect private information from prying eyes by wrapping it. However, it isn’t always the case. […]
Have you ever wondered, what can someone do with your IP address? It is possible to find out a person’s identity from your IP address if you share it with them online. If you share your IP with someone else, they can use it to spy on you or make money off of you. So, […]
Omegle used to be the go-to random chat site, connecting strangers for some fun, friendly conversations. But over the years, it’s really gone downhill. Luckily, there are plenty of awesome Omegle alternatives out there now that make chatting with strangers online way more fun. In this article, I’ll be breaking down the 10 best websites […]
If you’re in UK and wondering how to watch all your favorite HBO shows and movies like Game of Thrones, Euphoria, and The Batman, then you’ve come to the right place. Getting HBO Max in UK might seem tricky since it hasn’t officially launched there yet. But never fear, with this complete guide, you’ll learn […]
If you’re just minding your own business when an email pops into your inbox from Facebook and the subject line says your Facebook account’s recovery code is inside. Scammers are getting craftier with phony account recovery emails. If this sounds familiar, you’re not alone. Lots of folks are getting duped by fake Facebook account recovery […]
You’ve probably heard whispers of the “deep web” and “dark web” in hushed, ominous tones. There are a lot of myths and misconceptions about what exactly they are and what goes on there. Before you get spooked by the creepy stories, let’s set the record straight. The deep web and dark web aren’t as scary […]
You’ve probably heard of mobile hotspots by now. They’re an amazing way to get online anywhere and can be life-saving when traveling. But what happens if someone gets their hands on your hotspot password? Now, you have to assess whether mobile hotspots are secure. They could potentially harm your privacy. Fortunately, there are several methods […]
With data breaches happening every day and hackers using increasingly sophisticated technology to crack even the most complex passwords, you must ensure your password is strong enough to keep your accounts and information safe. Make sure to check your password so that you do not become an easy target. Your online security depends on it […]
Getting more privacy and security for your Xbox gaming is important these days. We all want to protect our info and play games safely. A virtual private network (VPN) is one of the best tools to make that happen. In this article, we’ll walk you through everything you need to know to get a VPN […]
If you’ve got a Mac and a ton of online accounts, you’ve also got a ton of passwords to keep track of. Between banking logins, social media profiles, streaming services, and shopping sites, it’s easy to feel overwhelmed by the sheer number of codes and passwords you need to remember. The good news is, you […]
As organizations strive to protect sensitive data and maintain network integrity, VPNs have emerged as an indispensable tool. One such type of VPN technology that has gained popularity is the SSL VPN, also known as a Secure Sockets Layer Virtual Private Network. In this guide we’ll discuss what exactly is an SSL VPN, and do […]
Have you ever wanted to watch your favorite Disney shows or movies but couldn’t access Disney+ when traveling or living abroad? We feel your pain. Nothing’s worse than getting your Disney fix taken away. But don’t worry, we’ve got your back. We’ll walk through different methods you can use to watch Disney+ no matter where […]
As the world continues to advance technologically, cyber threats also continue to evolve. One of the most common threats on the internet is phishing attacks, which often involve the use of phishing links or URLs. URL phishing attacks are a serious threat that can result in losing sensitive information and financial loss. By being aware […]
Have you ever seen that dreaded “No Internet Secured” message on your computer? It’s a common error and can be very frustrating when it happens, especially if you’re trying to get some work done. But don’t worry; it’s not the end of the world! We have solutions for you! By the end of this article, […]
If you’re a Roku user, you know how frustrating it can be when you cannot access certain content due to geo-restrictions or censorship. That’s where a VPN comes in – encrypting your internet traffic and masking your IP address, you can bypass these restrictions and stream content from around the world. In this blog, we’ll […]
Did you ever have one of those annoying Facebook messenger bugs that spreads itself to all your friends? You know the ones – they look like a normal message from a friend, tempting you to click a link or watch a video. But then suddenly your Messenger starts spontaneously sending the same message to people […]
Cybersecurity is a trendy topic these days, with hackers finding ever-more sophisticated ways to access our data and make off with it. As technology marches, the risk to our personal data is ever increasing. Taking a few basic steps can help protect you and keep your information safe. One of the important steps you can […]
If you’re just trying to chill and watch the latest episodes of your favorite Netflix shows, but no matter what you try, you keep getting that annoying proxy error. It’s frustrating to experience it. But don’t flip the coffee table in rage just yet. With a few simple tweaks, you can get past that error […]
iPhone Data Leak
If you love baseball but hate the blackout restrictions on MLB TV then you’re not alone. Nothing’s more frustrating than not being able to watch your favorite team just because of where you live. But don’t worry, there’s an easy fix. Using a VPN, or virtual private network, you can bypass the blackouts and stream […]
HP CEO Enrique Lores defended the company’s practice of disabling certain printers when users install third-party ink cartridges, saying it’s necessary to protect customers from security risks. In an interview with CNBC Television last week, Lores said HP printers are designed to work only with HP cartridges to guard against “embedded viruses” that could spread […]
We know you’re obsessed with getting that Victory Royale in Free Fire, but high ping and lagging can really put a damper on your gaming experience. You’ve probably heard rumors that the best VPN for Free Fire like Astrill can help boost your connection speed and lower your ping for Free Fire. But does it […]
Every online action you take today puts your personal information in danger, including simple web searches. Your IP address and browsing history will be recorded every time you utilize search browsing. Various businesses can benefit from this data. Users are identified so that advertisements can be tailored to each individual. Displaying personalized advertisements is how […]
HAK5 developed the Wi-Fi Pineapple, which is a private company. Now you may be wondering, how do fruit and WiFi go hand in hand? Well, there’s a story behind its name. The WiFi Pineapple gets its name from its appearance. It’s a small, black device with multiple antennas at the top that stem outwards in […]
Ever find yourself in need of Internet access while out and about, so you hop on the nearest public Wi-Fi network? It’s convenient, but is that free Wi-Fi ever really safe? Think about it – that network is open to anyone nearby, and there are hackers who know how to snoop on what people do […]
PDFs have long been a vehicle for malware and viruses. But can a PDF have a virus? The short answer is no, PDFs are simply a file format and are not inherently malicious. However, that doesn’t mean you should let your guard down when dealing with PDFs from untrusted sources. While PDFs may be a […]
With our fast-paced life, we are all hurrying to do daily chores. So when it comes to downloading files, the faster, the better. Right? Well, why are my downloads so slow? Sure, download speed is important, but it’s not the only factor determining how long a file takes to download. You can do several things […]
Suppose you get a call from someone claiming to be from Xfinity, and you start thinking about Xfinity will call me? Saying there’s an issue with your internet service or cable package that needs to be addressed immediately. They insist you provide personal information like your account number, social security number, or credit card details […]
When discussing dark web browsing, Tor is the first browser that springs to mind. Tor is growing in popularity among millions of people worldwide with the passing years. It has been synonymous with anonymous browsing during the last few years. As people’s concerns about online privacy rise, questions like is tor browser legal? What can […]
With the advent of cryptocurrency, the cyber risk landscape has grown increasingly complicated. Crypto-jacking and other crypto-focused malware are on the rise, and protecting your data is essential. Thankfully, it’s possible to mitigate the risk posed by cryptocurrency malware. In this article, we’ll uncover some of the latest insights on crypto malware and provide tips […]
As an emulator, Bluestacks is adored by the majority of its gamers. It claims to be magic for them. With this emulator, you can use any mobile app on Android as this emulator is specially designed for better performance, better speed, and more accurate control changes. Due to its popularity and demand to turn off […]
ESO Solutions, a leading provider of data and software for emergency responders and healthcare organizations, announced today that it suffered a ransomware attack impacting the sensitive data of up to 2.7 million individuals. In an incident notice published on its website, the Austin, Texas-based company stated that an unauthorized third party deployed ransomware to encrypt […]
So you’re in India and want to protect your privacy and security online? With increased government monitoring and censorship, using a VPN is crucial. But with so many VPN services out there, how do you choose? As India’s leading VPN provider, AstrillVPN is the obvious choice for privacy, security and bypassing geo-restrictions. With servers optimized […]
Have you ever been in the middle of an intense team fight in Dota 2, your fingers flying across the keyboard as you dodge spells and land perfect combos, only to have your screen freeze for a few seconds? Lag spikes and high ping in Dota 2 can ruin the experience and cost you the […]
Ever get one of those virus alerts on your computer claiming you’ve been looking at pornography? Yeah, it’s annoying and embarrassing even though you know you haven’t looked at anything inappropriate. The good news is those virus alerts are scams trying to trick you into calling a fake support number or downloading software that will […]
Have you ever struggled with bad credit? Maybe you’ve made a few mistakes in the past that hurt your credit score, and now you have a hard time qualifying for loans, credit cards, apartments, or jobs. It happens to the best of us. But what if there was a way to establish a new credit […]
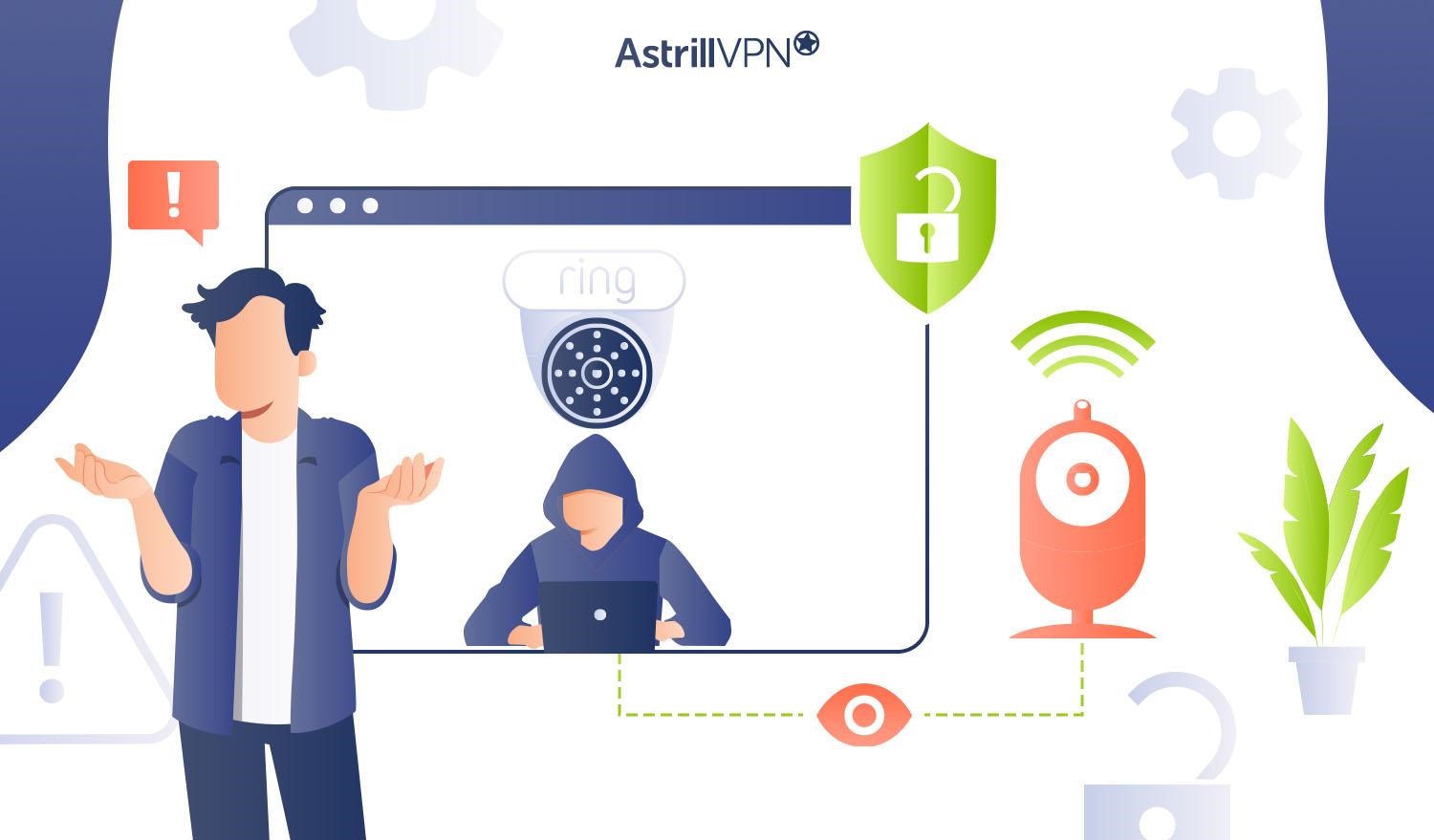
In recent years, smart home devices like Ring cameras have revolutionized the way we protect our homes. With their ability to provide real-time video feed and instant alerts on our mobile devices, they have offered an added layer of convenience and security. But like any technology connected to the internet, they are not immune to […]
Google Chat, an important component of Google’s business-focused software suites, has become a popular mode of communication for individuals and organizations. This tool, however, raises certain privacy concerns, especially as increasing numbers of scammers find means to misuse it. As a user, it’s imperative to recognize the potential vulnerabilities and learn how to navigate safely […]
If you’ve got your hands on Sony’s new PlayStation 5 console then it’s time to get that optimized for the best online gaming experience. One of the most important things you can do is make sure you’ve got an Open NAT type. NAT type refers to how well your PS5 can connect to other players […]
In today’s digital world, staying anonymous can be trickier than it sounds. Everything from the websites you visit to the messages you send is tracked and recorded, often without your knowledge or consent. Staying truly anonymous online takes vigilance and know-how. But don’t worry, we’ve got you covered. In this guide, you’ll learn everything you […]
If you’re one of the millions of cord-cutters out there looking for free TV shows and movies online, there’s a good chance Putlocker has popped up on your radar. But before you dive in and start binge-watching your favorite series, you’re probably wondering is Putlocker safe? As with any free streaming site, there are some […]
Have you been using uTorrent for years to download your favorite movies, TV shows, music, books, and software? It’s time to ditch that outdated torrent client and upgrade to something better. uTorrent used to be great, but now it’s riddled with ads and bloatware that slow down your downloads and invade your privacy. You deserve […]
Have you ever wondered why the Wi-Fi on your phone automatically connects when you get home? It’s because network devices like routers use MAC addresses( unique identifiers hardwired onto network interface cards) to recognize trusted devices. But MAC addresses aren’t always permanent. As you connect more of your smart home devices, you may start to […]
You’ve probably heard of sting operations where undercover agents set up scenarios to catch criminals. Well, honeypots are kind of like cyber sting operations. They lure in hackers to secretly gather information about their methods and motives.Ever wonder how cybersecurity experts try to outsmart hackers? One of their clever techniques is using decoy systems called […]
As more and more workplaces adopt hybrid work setups, the need for secure remote data access has become evident. Companies and employees need to be able to access resources from home and portable devices, without risking data breaches or compromised security. Virtual private networks are already in use by many businesses worldwide, allowing secure, anonymous […]
You’ve probably come across ID.me at some point when accessing government services or signing up for certain websites. The company verifies people’s identities to help prevent fraud and ensure security, but you may be wondering; is ID.me safe? How exactly does it work, and what does it do with your personal information? ID.me uses technology […]