Blogs Posted by Bisma
Are you eager to catch the latest UFC action but hesitant to shell out for expensive pay-per-view events? You’re not alone. As the popularity of mixed martial arts continues to soar, many fans are searching for ways to watch their favorite fighters without breaking the bank. Fortunately, there are several legitimate methods on how to […]
You’ve probably heard of mobile hotspots by now. They’re an amazing way to get online anywhere and can be life-saving when traveling. But what happens if someone gets their hands on your hotspot password? Now, you have to assess whether mobile hotspots are secure. They could potentially harm your privacy. Fortunately, there are several methods […]
In today’s digital age, you’re constantly sharing sensitive information online. Your data is vulnerable to prying eyes, from credit card numbers to private messages. This is where encryption comes in. Encryption is the process of encoding information, making it unreadable to unauthorized parties. Understanding encryption becomes crucial for protecting your privacy and security as you […]
Venmo is a great way to pay friends back for dinner or to split the cost of a group gift, but it’s essential to be aware of the different types of Venmo scams that are out there. In this article, you will learn about the different types of Venmo scams and how to protect yourself […]
In the digital age, where nearly every aspect of our lives is intertwined with the internet, cybersecurity has become an increasingly critical concern. Cybercrime, as its name suggests, involves criminal activities that take place in cyberspace, primarily using the internet or computer networks. This type of crime can range from stealing personal data to spreading […]
The concept of online privacy is becoming more critical as we increasingly rely on the internet for personal and professional activities. Every time we browse the web, our online activity is tracked in various ways, leaving us vulnerable to advertisers, hackers, and even governments. Many users believe that using “Incognito Mode” in their browsers or […]
Multiple security vulnerabilities in Jan AI, an open-source alternative to ChatGPT, have been discovered, which could potentially be exploited by remote, unauthenticated attackers to manipulate systems. This warning comes from Snyk, a developer security platform. Jan AI, developed by Menlo Research, is marketed as a personal assistant that operates offline on desktops and mobile devices. […]
Are you looking to unlock a world of free streaming content on your Amazon Firestick? Installing Kodi can open up endless entertainment possibilities, giving you access to movies, TV shows, live sports, and more. While the process may seem daunting initially, adding Kodi to Firestick is relatively straightforward when you follow the proper steps. In […]
Protecting online privacy has become more crucial in today’s digital landscape. Your IP address is a digital fingerprint, potentially exposing your location and online activities to prying eyes. Whether you’re concerned about cybercriminals, intrusive advertisers, or government surveillance, masking your IP address is a powerful way to safeguard your digital identity. This article will guide […]
In today’s digital world, staying anonymous can be trickier than it sounds. Everything from the websites you visit to the messages you send is tracked and recorded, often without your knowledge or consent. Achieving true online anonymity requires the right tools and techniques. This guide will show you how to protect your identity, remain anonymous […]
In today’s world, streaming platforms are a dime a dozen, offering users a wealth of content at their fingertips. One of the newer names in the world of free streaming is Tubi. With a vast library of movies, TV shows, and even some exclusive content, Tubi has garnered attention from viewers seeking free alternatives to […]
You might think using a VPN makes you completely anonymous while you browse the internet freely. But is that really the case? We’re often led to believe that cybersecurity and national security measures have our backs, but the reality is more complex. Despite claiming a no-logs policy, one of the UK-based VPN handed over user […]
In an increasingly interconnected world, the importance of online privacy and security cannot be overstated. As messaging apps become an integral part of our daily lives, the need for protecting our communications has never been more pressing. Telegram, a popular messaging platform known for its speed and security features, is used by millions worldwide. However, […]
The UK’s Information Commissioner’s Office (ICO) has provisionally fined Advanced Computer Software Group £6.09 million after a 2022 ransomware attack compromised the personal data of nearly 83,000 individuals. The breach disrupted critical NHS services, including NHS 111, and exposed sensitive information such as medical records and personal contact details. In August 2022, hackers exploited a […]
A new ransomware-as-a-service (RaaS) operation, named VanHelsing, has emerged, affecting multiple platforms including Windows, Linux, BSD, ARM, and ESXi systems. CYFIRMA first reported this new ransomware operation on March 7, and Check Point Research followed up with a detailed analysis yesterday. VanHelsing operates on a revenue-sharing model where affiliates keep 80% of ransom payments, with […]
If you are relocating internationally or have no idea how to change app store country, you may need to switch your country to access region-specific apps and content. Changing your App Store location isn’t as straightforward as expected, but you can navigate the process smoothly with the proper guidance. This step-by-step guide will walk you […]
In today’s digital age, protecting your privacy, data, and online identity is important. From online banking to online shopping and work-related activities, the internet is full of potential threats that could compromise your personal information. That’s why many people turn to VPNs (Virtual Private Networks) to stay safe while browsing the web. But there is […]
If you’re concerned about privacy online and want to get a VPN to secure your internet connection, it’s smart thinking. But with so many VPN services out there, how do you choose? Before signing up for any VPN, you must understand what matters when protecting your data. Not all VPNs are created equal, and some […]
A sophisticated malware campaign known as ‘DollyWay’ has been actively exploiting WordPress websites since 2016, compromising more than 20,000 sites globally. Security researchers have identified that the malware’s primary goal is to redirect unsuspecting visitors to malicious websites, including fake dating, gambling, cryptocurrency, and sweepstakes platforms. The **DollyWay** malware infiltrates WordPress websites by exploiting vulnerabilities […]
If you have considered is opera gx good as your primary web browser then you are on the right track. As a gamer-focused variant of the Opera browser, it offers unique features tailored to enhance your gaming experience. However, before adopting any new software, it’s crucial to evaluate its security measures. We’ll delve into its […]
Google’s parent company, Alphabet, has agreed to acquire cloud security startup Wiz for $32 billion, marking its largest acquisition to date. The deal aims to strengthen Google Cloud’s cybersecurity capabilities to compete with Amazon Web Services and Microsoft Azure. Wiz, a rapidly growing startup, provides cloud security solutions across multiple platforms. Pending regulatory approval, the […]
Malicious actors have found a new way to exploit Cascading Style Sheets (CSS), which are primarily used for styling web pages, to bypass spam filters and invade users’ privacy. According to recent findings by Cisco Talos, these malicious tactics pose serious risks to both security and personal information. Omid Mirzaei, a researcher at Talos, noted […]
As cyber threats continue to evolve, your organization’s security depends on more than just technology. You and your employees are the human firewall in cybersecurity – the critical first line of defense against attacks. By cultivating security awareness and best practices across your workforce, you can significantly reduce vulnerabilities and prevent breaches. This article will […]
As a technology professional, you’re likely familiar with various cybersecurity threats. However, one often-overlooked danger lurking in your systems could be macro viruses. These insidious programs hide within seemingly innocuous documents, waiting to wreak havoc on your network. The initial macro virus emerged in July 1995, and macro viruses, primarily targeting Word documents, quickly became […]
As you navigate the complex landscape of modern cybersecurity, understanding and combating network security threats is paramount. Your organization’s digital infrastructure faces an ever-evolving array of risks in today’s interconnected world. From sophisticated malware to social engineering tactics, the threats to your network’s integrity are diverse and relentless. This comprehensive guide will equip you with […]
If you’re tired of all those annoying ads on YouTube and want to upgrade to YouTube Premium, Great choice – you will get ad-free videos, access to YouTube Originals shows, and the ability to download videos to watch offline. The only downside is that YouTube Premium isn’t cheap at $13.99 per month. Don’t worry, you […]
As a cybersecurity professional, you know the ever-present threat of malicious code. From stealthy malware to sophisticated ransomware, nefarious actors constantly develop new ways to infiltrate systems and wreak havoc. To stay ahead of these evolving threats, you need a comprehensive strategy for malicious code detection. This article will equip you with cutting-edge techniques and […]
If you have finally scored a PS5 and you’re ready to start gaming online with your friends, the only problem is you’re stuck with a strict NAT type and laggy multiplayer. Port forwarding your PS5 is actually pretty straightforward and will open up your connection in no time. In just a few steps, you’ll be […]
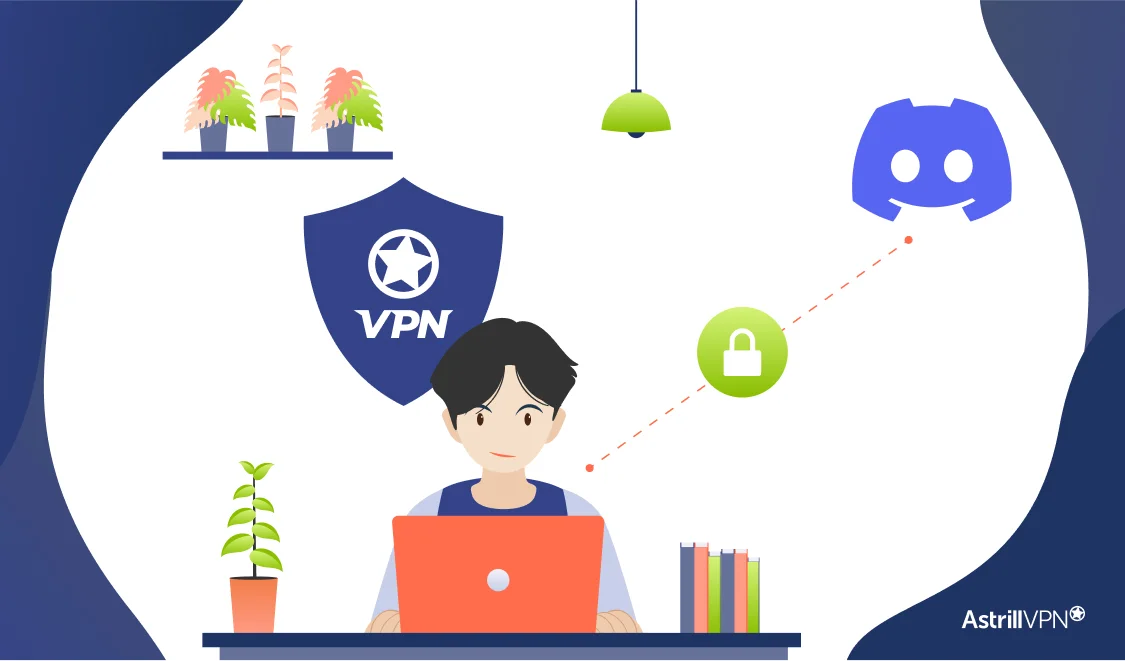
Are you concerned about your privacy and security while using Discord? As an avid Discord user, you understand the importance of protecting your online communications. With cyber threats on the rise, securing your Discord experience has become more crucial than ever. By using a virtual private network (VPN), you have a digital shield in the […]
As you navigate the digital landscape, your organization’s cybersecurity is constantly under threat. One particularly insidious danger lurking in the shadows is DNS hijacking. This malicious attack can redirect your web traffic, compromise sensitive data, and damage your reputation, all while operating largely undetected. Understanding the mechanics of DNS hijacking and implementing robust defense strategies […]
If you are a tennis fan, you don’t want to miss a single volley or passing shot when Wimbledon rolls around next year. As the world’s oldest and most prestigious tennis tournament, Wimbledon is a must-see event. But for those of us not lucky enough to score tickets to Center Court, how can we get […]
In the digital age, your online security is paramount. Yet, lurking in the shadows of the internet is a threat you may not be aware of: packet sniffing. This powerful technique allows cybercriminals to intercept and analyze data transmitted over a network, potentially exposing your sensitive information. As you navigate the online world, understanding packet […]
If a “VPN not working” error hits you, we know it’s terrible. If you are connecting from a country with internet restrictions then find out how to fix your VPN connection problems. Outdated VPN software, blocked router or ports can cause problems as well. Read on to find out VPN connection problems. Why is my […]
Has your email account been compromised? Discovering that your email has been hacked can be a distressing experience. You may feel violated, anxious about what information was accessed, and unsure how to regain control. However, acting swiftly and methodically is crucial to mitigate potential damage and secure your digital presence. This step-by-step guide will walk […]
In today’s digital age, you’re likely familiar with various cybersecurity threats. However, one increasingly prevalent danger may have escaped your notice: smishing. This malicious tactic combines “SMS” and “phishing,” referring to fraudulent text messages designed to deceive you into divulging sensitive information. This is also called SMS phishing. Understanding smishing and how to protect yourself […]
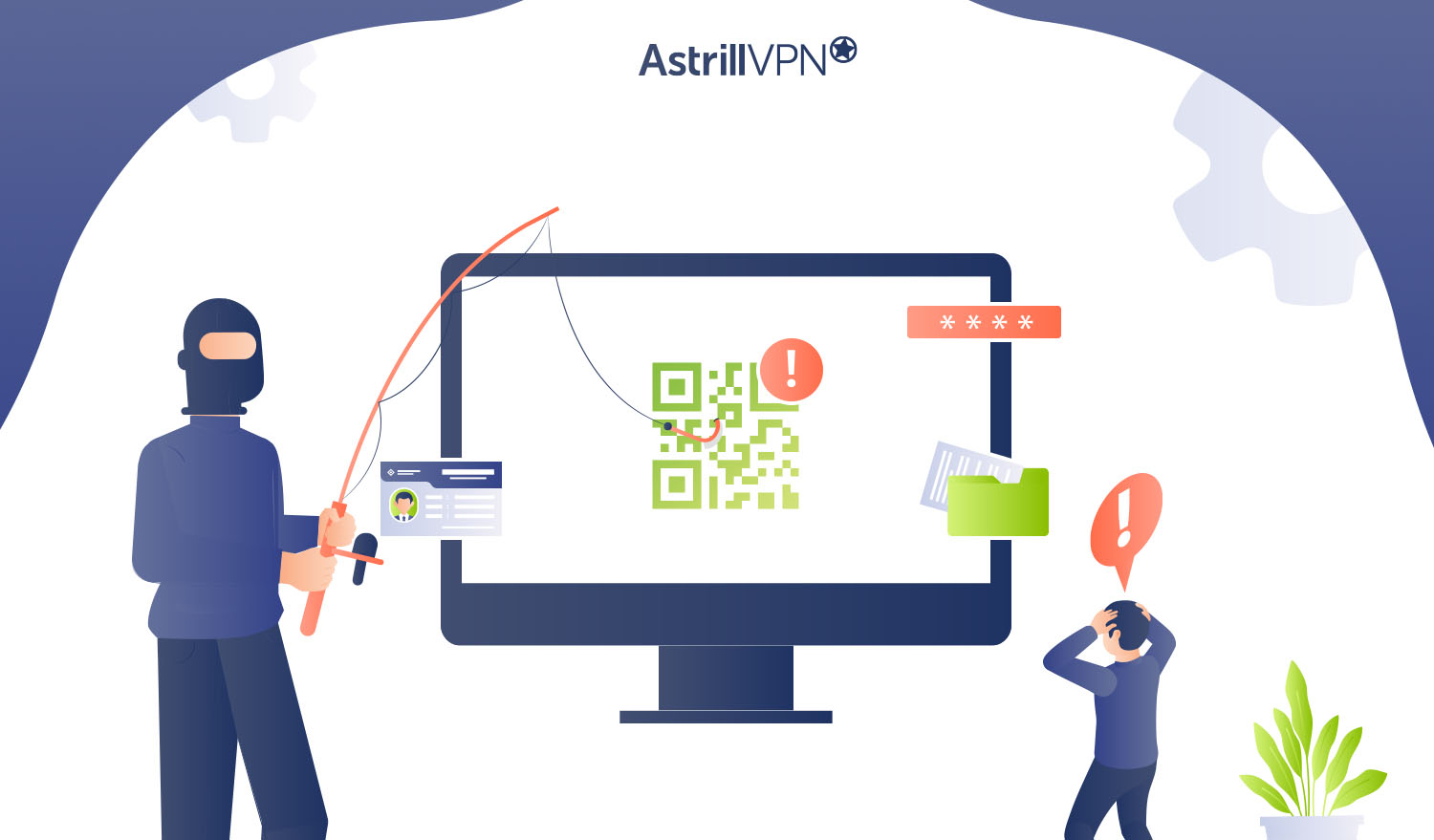
As cybersecurity threats evolve, you must stay vigilant against new forms of attack. One emerging threat you need to be aware of is quishing, a sophisticated variation of phishing that exploits QR codes to deceive victims. Unlike traditional phishing emails, quishing definition is that it leverages QR codes’ widespread use and convenience to lure you […]
As cybersecurity threats continue to evolve, you must remain vigilant against both digital and physical attacks on your organization. One often overlooked vulnerability is the tailgating attack, where an unauthorized individual gains access to secure areas by closely following an authorized person through a restricted entry point. This deceptively simple tactic can have severe consequences, […]
In the current era, privacy is more important than ever, and digital privacy must be protected at all costs. Just like that, your browsing history is precious data. It can reveal much about you, your interests, and your political views. Before reaching any website, all of this must pass through your trusted internet service provider […]
With the rising privacy issues, it’s important to hide your location from strangers. There are several other reasons why you might want to change your browser location. Maybe you’re traveling and want to access websites that are specific to the country you’re visiting. Maybe you live in a country other than the one you were […]
As an Amazon Prime subscriber, you have access to a vast library of streaming content. However, you may encounter frustrating geographic restrictions when traveling or living abroad. Enter the virtual private network (VPN), your ticket to unrestricted Prime viewing from anywhere in the world. By using a VPN with Amazon Prime, you can bypass regional […]
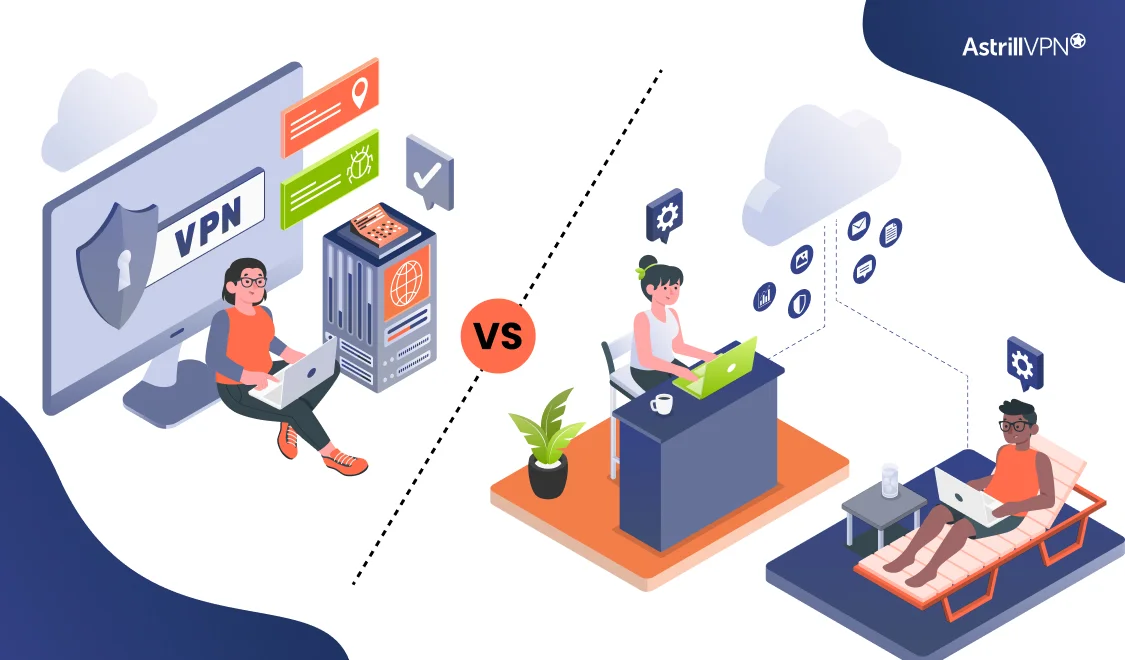
Accessing your work environment from anywhere has become essential in today’s interconnected world. As you explore remote access solutions, you’ll likely encounter two popular options: Virtual Private Networks (VPNs) and Remote Desktop Protocol (RDP). While both connect you to distant resources, they operate quite differently and cater to distinct needs. Understanding the nuances between VPNs […]
If you’re surfing the web when suddenly everything slows to a crawl, and Pop-ups bombard your screen with scary warnings that your computer is infected. Well! Could a VPN have stopped this virus attack? We did the digging to find out what does a VPN protect you from. Get ready to separate fact from fiction […]
In today’s era, it’s really difficult to protect your privacy online. Social media apps, internet browsing and different software can make the privacy of data a really ambiguous concept. Using the VPN is a good way to protect your privacy on the internet. By using a VPN, you can protect yourself from having your IP […]
As you navigate the digital landscape, your online security is constantly threatened. One particularly insidious danger lurking in the shadows is session hijacking. This sophisticated attack can compromise your sensitive data and online identity in mere moments. By intercepting and exploiting your active web sessions, cybercriminals can gain unauthorized access to your accounts, financial information, […]
As you look ahead to 2025, cloud security issues loom large on the horizon. Your organization’s digital assets and sensitive data face an evolving landscape of threats in the cloud environment. From sophisticated cyber attacks to compliance hurdles, you’ll need to navigate a complex array of challenges to keep your cloud infrastructure secure. This article […]
In today’s hyper-connected digital landscape, your devices face constant threats from malicious software. Malware, short for “malicious software,” encompasses many harmful programs to infiltrate and damage your computer systems. These digital threats can compromise your data, financial information, and overall cybersecurity, from viruses and worms to trojans and ransomware. Understanding the various types of malware […]
Hulu is a widely-used streaming service, but it can only be accessed in the US. If you attempt to watch Hulu or Hulu + Live TV from other countries, you’ll likely see a message indicating that the content is not accessible in your location. However, you can overcome these geographic restrictions and enjoy full access […]
In today’s digital landscape, your organization’s cybersecurity is only as strong as its weakest link. One of the most insidious vulnerabilities you may face is the broken authentication attack. This method exploits flaws in your authentication processes, potentially granting unauthorized access to sensitive systems and data. As a security professional, understanding and mitigating this threat […]
As cybersecurity threats continue to evolve, you need a robust framework to understand and combat adversary tactics. Enter the MITRE ATT&CK framework – a comprehensive knowledge base of cyber adversary behavior. This powerful tool equips you with the intelligence to strengthen your organization’s security posture. In this guide, you’ll explore the intricacies of Mitre ATT&CK […]
Pretexting is a critical cybersecurity threat that focuses on human manipulation rather than technical exploits. Attackers use fabricated scenarios to deceive individuals into revealing sensitive information or granting access to secure systems. Understanding how pretexting works, spotting everyday situations where it pops up, and knowing how to avoid these kinds of attacks can really help […]


![How to Watch UFC for Free in 2025: The Ultimate Guide [Updated]](https://www.astrill.com/blog/wp-content/uploads/2024/08/How-to-Watch-UFC-for-Free.jpg)





















![How to get the Cheapest YouTube Premium Discount? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2024/01/How-to-get-Cheapest-YouTube-Premium-Deals.jpg)