Cross-site scripting (XSS) is a prevalent security vulnerability in web applications. It occurs when an attacker injects malicious scripts into otherwise benign and trusted websites. These scripts are executed in the victim’s browser, leading to potential security breaches, data theft, and unauthorized access. XSS typically exploits vulnerabilities in input validation and output encoding, making it […]
On December 26, 2024, General Dynamics, the global aerospace and defense company, announced that it had been the target of a phishing attack that compromised dozens of employee benefits accounts. The unauthorized activity was discovered on October 10 after the attackers accessed and changed the employee benefits accounts through a third-party login portal. General Dynamics […]
So you’re out on vacation or simply would like some downtime, and you want to catch up with some content on TSN. However, when you try to access it, you’re hit with a message that states, “Content not available for viewing in your region.” We can understand your frustration, but luckily, there is a way […]
You’ve been waiting all year for this day. The biggest football game of the season is finally here – Super Bowl LIX 2025! But what if you can’t make it to the stadium or don’t have cable access? Don’t worry; we’ve got you covered. In this article, we’ll walk through all the ways you can […]
The Internet is super important for how we communicate and stay connected today, but it also raises real concerns about privacy, security, and censorship. That’s where VPNs come in, giving people a chance to surf the web anonymously and securely. Traditional VPNs have been reliable for this, but they depend on centralized servers that can […]
VPNs have become essential tools for individuals and businesses looking to protect their data and access content without restrictions. However, when considering a VPN, one of the most common questions is: how much does a VPN cost? The price of a VPN can vary significantly depending on factors like features, service quality, and subscription duration. […]
The US government has launched an investigation into TP-Link, a leading Chinese router manufacturer, following growing concerns over potential cybersecurity risks associated with their products. TP-Link routers, which comprise a significant portion of the US market, are under scrutiny due to vulnerabilities that could be exploited for cyberattacks, posing a threat to individual users and […]
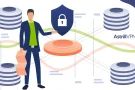
Zelle is a popular payment platform with a staggering $806 billion transaction volume, a 28% increase from last year. It is also set to expand at a growth rate of 20% in the next five years. Zelle allows free instant transfers from the app. As companies strive to enhance the customer experience and make things […]
As a business owner or financial professional, you understand the critical importance of protecting your organization from fraud. But do you truly grasp how modern fraud detection systems work to safeguard your assets? These sophisticated tools leverage advanced analytics and machine learning to identify suspicious patterns and anomalies that may indicate fraudulent activity. By understanding […]
Cybersecurity researchers have uncovered a sophisticated new investment scam targeting users through social media malvertising, AI-generated video testimonials, and fraudulent company-branded posts. The scam, known as Nomani, has already led to substantial financial and data losses, with experts warning that its reach is growing rapidly. In its latest H2 2024 Threat Report, cybersecurity company ESET […]
QAX’s XLab Uncovers Winnti Hacking Group’s New ‘Glutton’ PHP Backdoor December 15, 2024. The cybersecurity experts at QAX’s XLab have uncovered a new PHP backdoor, dubbed ‘Glutton,’ that is being leveraged by the notorious Winnti hacking group in attacks targeting organizations in China and the U.S. and other cybercriminal groups. According to QAX’s XLab, the […]
Security researchers have uncovered significant vulnerabilities in the Prometheus monitoring tool, revealing thousands of exposed servers and exporters leaking sensitive data and introducing risks such as denial of service (DoS) and repo jacking. Prometheus, a leading tool in observability for monitoring applications and cloud infrastructure, has long been favored for its robust features. However, its […]
As a tennis enthusiast, you’re undoubtedly eager to catch every serve and volley of the Australian Open live stream. But what if you don’t have a cable subscription or access to traditional broadcasts? Don’t worry, you can still experience the excitement of this Grand Slam tournament from the comfort of your home. In this guide, […]
The Rose Bowl, often called the “Granddaddy of Them All,” is one of the most prestigious college football bowl games in the United States. Scheduled for January 1, 2025, this event will feature top-tier college football teams and capture fans worldwide. Here’s a comprehensive guide on streaming the Rose Bowl live, ensuring you don’t miss […]
After a recent cybersecurity attack disrupted its operations, Krispy Kreme, the beloved doughnut brand, faces significant challenges in meeting the growing demand for its delectable treats. The attack, first detected on November 29th, has continued to impact Krispy Kreme’s ability to fulfill online orders, leaving doughnut enthusiasts across the country disappointed and craving their favorite […]
In a groundbreaking move against cybercrime, Europol has announced the successful dismantling of 27 illegal Distributed Denial-of-Service (DDoS) attack platforms as part of a coordinated international operation known as PowerOFF. The global crackdown, which involved law enforcement from 15 countries, led to the closure of several illicit websites commonly used for launching cyberattacks, including zdstresser.net, […]
Ransomware-as-a-Service (RaaS) represents a transformative evolution in the cybercrime landscape. By operating as a subscription-based model, RaaS provides cybercriminals with ready-made ransomware tools, significantly lowering the barriers to launching attacks. This “ransomware marketplace” allows even inexperienced actors to execute complex attacks, leading to a surge in ransomware incidents globally. The impact of RaaS is felt […]
A VPN creates a secure and encrypted connection between your device and the internet. By routing your internet traffic through a remote server, a VPN masks your IP address, ensuring your online activities remain private and protected from prying eyes. For iPhone users, integrating a VPN enhances security and bypasses restrictions. It ensures privacy, especially […]
If you are a Telegram user, be warned as scammers are increasingly targeting this popular messaging app. As Telegram’s user base grows, so do the sophisticated schemes designed to exploit unsuspecting individuals. From fake investment opportunities to phishing attempts, the threats are diverse and ever-evolving. You may think you’re too savvy to fall victim, but […]
Have you heard about the Booksi scam that’s been making waves online? As an avid reader, you may be tempted by deals that seem too good to be true. Unfortunately, scammers are targeting unsuspecting bibliophiles through fake websites and social media accounts. These fraudulent operations promise rare books and incredible discounts, only to leave you […]
As you rely more on your smartphone for banking, social media, and other sensitive accounts, you may be vulnerable to an insidious identity theft known as the SIM swap attack. This increasingly common scam allows criminals to hijack your phone number and gain access to your most valuable online information. By understanding how these attacks […]
Crypto scams have surged in recent years, leaving countless individuals vulnerable to fraud in the fast-evolving world of digital currencies. As cryptocurrency continues to gain popularity, so do the scams targeting unsuspecting investors. In this guide, we’ll explain the most common types of crypto scams, how to spot them, and the essential steps to protect […]
YouTube has become a go-to platform for entertainment, education, and everything in between. However, the relentless ads can disrupt the viewing experience, leading many users to turn to ad blockers. But with YouTube’s increasing efforts to detect and bypass these tools, watching ad-free content isn’t as simple as it used to be. In this guide, […]
Encryption serves as a powerful tool to safeguard sensitive information from unauthorized access and maintain confidentiality. In this guide, we have explained VPN encryption in detail and discussed the types of protocols you may come across. So without further ado, let’s dive right into VPN encryption and understand what it is and what it is […]
As cybersecurity threats evolve, you must stay vigilant against increasingly sophisticated attacks. Spear phishing in cybersecurity is one of the most targeted and dangerous forms of social engineering. Unlike broad phishing campaigns, spear phishing attacks are personalized to exploit your specific vulnerabilities. By understanding how these attacks work and cybercriminals’ techniques, you can better protect […]
In today’s digital age, your Instagram account is more than just a social platform. It’s a personal brand, a business tool, and a digital extension of yourself. Recognizing the signs of Instagram hacking is crucial for protecting your online presence and personal information. This article will guide you how to know if your Instagram is […]
Peacock TV, the popular streaming service from NBCUniversal, offers a wide range of content, including exclusive originals, blockbuster movies, and live sports. However, if you’re in Australia, accessing Peacock can be tricky due to its geo-restrictions that limit access to U.S. residents. In this guide, we’ll show you how to bypass these restrictions and provide you […]
UFC 310 is shaping up to be one of the most electrifying events of the year, with a stacked fight card headlined by a highly anticipated showdown between Flyweight Champion Alexandre Pantoja and the dynamic challenger Kyoji Asakura. On December 7, 2024, in Las Vegas, this event promises to deliver high-octane action for MMA enthusiasts […]
Note: The Deal is Expired. Stay tuned for more exciting discounts. The season of discounts and deals is finally here as Black Friday is just around the corner. To make this season much more amazing, AstrillVPN is offering the best and biggest Black Friday VPN deal. Overview AstrillVPN is offering a whooping flat 83.3% discount […]
In today’s digital world, it is important to be aware of our online privacy since prying еyеs arе always on thе watch. One of the most common types of harmful software that jeopardizes our privacy is spywarе. It is a long-standing and ever-present danger that may silеntly infiltratе our dеvicеs, resulting in unlawful acts such […]
Have you ever received a suspicious phone call claiming to be from your bank or a government agency? Vishing, short for “voice phishing,” uses phone calls or voice messages to trick you into divulging sensitive information or taking harmful actions. As technology advances, these scams become increasingly sophisticated and challenging to detect. Understanding what is […]
Wi-Fi hacking isn’t just a technical buzzword; it’s a real threat that can disrupt lives and businesses. Hackers target unsecured or weakly protected networks to infiltrate your digital world, often without your knowledge. The consequences of such an attack can be far-reaching, from identity theft and financial loss to compromising the security of your connected […]
Have you ever tried to access a website or service only to find that your IP has been temporarily blocked? Knowing how to unblock your IP address and regain access can be frustrating and confusing. In this blog, we’ll explore the reasons why your IP address might get blocked and provide you with ways to […]
Have you ever considered how vulnerable your personal information is to criminal exploitation? In today’s digital age, criminal identity theft has become an increasingly prevalent threat, leaving countless victims in its wake. This insidious crime can wreak havoc on your finances, reputation, and peace of mind. Cybercriminals employ increasingly sophisticated tactics, so you must understand […]
If you’ve ever tried to catch a live game on ESPN or ESPN+ and got hit with a “blackout” message, you totally know how annoying that is. Blackouts happen when a game can’t be streamed in certain places because local networks have exclusive rights to show it. This means you can’t watch your favorite teams […]
A computer virus can be more than just a headache. It’s a serious security risk that can mess with your files, slow down your system, and even steal personal information without you knowing. Viruses often get into your computer through things like email attachments, infected websites, or software downloads, exploiting weaknesses in your system’s defenses. […]
In a new advisory, IBM X-Force researchers have uncovered ongoing campaigns by the cybercriminal group Hive0145, deploying the advanced Strela Stealer malware to steal sensitive email credentials across Europe. According to the report, the attacks primarily target Spain, Germany, and Ukraine. They use authentic invoices in phishing emails to deceive recipients and boost the credibility […]
Hulu is one of the most popular streaming services, with 50.2 million users as of 2024. You’d want to change your location on Hulu for many reasons, and if you’re unsure where to start, we’re here to help. You might want to change your location so that you can access tons of diverse movies and […]
Has your email account been compromised? Discovering that your email has been hacked can be a distressing experience. You may feel violated, anxious about what information was accessed, and unsure how to regain control. However, acting swiftly and methodically is crucial to mitigate potential damage and secure your digital presence. This step-by-step guide will walk […]
Are you eager to catch the latest UFC action but hesitant to shell out for expensive pay-per-view events? You’re not alone. As the popularity of mixed martial arts continues to soar, many fans are searching for ways to watch their favorite fighters without breaking the bank. Fortunately, there are several legitimate methods on how to […]
Two popular live TV streaming options, fuboTV, and YouTube TV have become favorites for their wide range of channels, great sports coverage, and flexible streaming choices. Picking between these two can be tricky since they both have unique features that appeal to different viewers. fuboTV started as a go-to for sports fans, especially those into […]
Unlock Privacy & Freedom this Singles’ Day – Get AstrillVPN at 35% OFF! Special offer: Apply coupon code SINGLES11 to avail of the exclusive discount.
In today’s digital age, you rely on messaging apps to stay connected with friends, family, and colleagues. With its widespread popularity, WhatsApp likely plays a significant role in your daily communications. But as cyber threats evolve and privacy concerns grow, you may question the safety and security of this platform. As we enter 2024, it’s […]
Apple Pay is a super quick, secure, and easy way to manage your digital payments. Its transactions are protected by biometric authentication, tokenization, and encryption, keeping your information safe from prying eyes. However, the convenience of Apple Pay has also caught the attention of cybercriminals. Even though Apple Pay has solid security measures, it’s important […]
In today’s hyper-connected world, your smartphone is both a powerful tool and a potential vulnerability. An insidious threat lurks as you navigate daily life: spam call scams. These deceptive tactics have evolved significantly in 2024, becoming more sophisticated and challenging to detect. Understanding the latest techniques employed by scammers is crucial for protecting yourself and […]
Whether you’re streaming videos, working remotely, or just browsing the internet, the security of your Wi-Fi connection is important. As our reliance on wireless networks has grown, so too have the threats that target them. Wireless Protected Access (WPA) protocols have been the standard for securing Wi-Fi networks for years, with WPA2 being the most […]
The Sysdig Threat Research Team (TRT) today announced the discovery of a global operation called “Emeraldwhale” that has stolen over 15,000 cloud service credentials from misconfigured Git configurations. According to the Sysdig TRT, the attackers used a blend of private tools to exploit misconfigured web services, gaining unauthorized access to cloud credentials, cloning private repositories, […]
Phone mirroring allows someone to monitor your phone activities. This is a severe breach of privacy, and we can imagine your many concerns if you feel like you’re a victim of unwanted screen mirroring. Screen mirroring allows hackers to monitor everything on your mobile device and then steal your sensitive and confidential data. The screen […]
The digital era has offered many benefits to users, making things more accessible and convenient. While that is true, the digital landscape also has a dark side, and you can see it in the form of malicious actors and hackers waiting for the perfect opportunity to steal vulnerable users’ sensitive and confidential data. If you […]
In today’s digital age, you’re likely familiar with various cybersecurity threats. However, one increasingly prevalent danger may have escaped your notice: smishing. This malicious tactic combines “SMS” and “phishing,” referring to fraudulent text messages designed to deceive you into divulging sensitive information. This is also called SMS phishing. Understanding smishing and how to protect yourself […]




























![The Best Black Friday VPN Deal 2024 that You Will Ever Come Across [Expired]](https://www.astrill.com/blog/wp-content/uploads/2022/11/Feature-Image-135x90.jpg)






















